Issue
-
How to integrate Active Directory in Jenkins via LDAPS.
-
How to integrate trusted Active Directory domains in Jenkins.
Environment
-
CloudBees Jenkins Enterprise - Managed controller (CJE-MM)
-
CloudBees Jenkins Enterprise - Operations Center (CJE-OC)
-
Active Directory (AD) plugin
-
Windows Server 2012 R2
Resolution
The following resolution steps explains the process for integrating a Secure Active Directory with a non-trusted (self-signed) certificate.
On the AD host
Step 1. Install the Active Directory Certificate Services
| If Certificate Services are already installed, skip to step 2, below. |
-
Log in to your Active Directory server as an administrator.
-
Click
Start, point toAdministrative Tools, and then clickServer Manager. -
Then
Manage>Add Roles and Features. -
On the
Select Server Rolespage, select theActive Directory Certificate Servicescheck box. ClickNexttwice. -
On the
Select Role Servicespage, select theCertification Authoritycheck box, and then clickNext. -
On the
Specify Setup Typepage, clickEnterprise, and then clickNext. -
On the
Specify CA Type, clickRoot CA, and then click Next. -
On the
Set Up Private KeyandConfigure Cryptography for CApages, you can configure optional configuration settings, including cryptographic service providers. However, the default values should be fine. Click Next twice. -
In the
Common name for this CAbox, type the common name of the CA, and then clickNext. -
On the
Set Validity Periodpage, accept the default values or specify other storage locations for the certificate database and the certificate database log, and then clickNext. -
After verifying the information on the
Confirm Installation Selectionspage, clickInstall.
Step 2. Obtain the Server Certificate
As explained on Microsoft’s LDAP over SSL (LDAPS) Certificate > Exporting the LDAPS Certificate and Importing for use with AD DS. Note that you need to:
-
Choose "No, do not export the private key" in step-10
-
Choose "DER encoded binary X.509 (.CER)" in step-11. This file will be used in the following step.
On the Jenkins host
Requirements: At the network/infrastructure level, the Jenkins instance must be able to connect to your AD services.
Step 3. Install your cert into your Jenkins cacerts
Having your AD cert file, follows steps from B. Adding “certX” to the keystore on the KB How to install a new SSL certificate.
Step 4. Run Jenkins with proper startup parameters
Include the parameters mentioned in How to install a new SSL certificate plus -Dhudson.plugins.active_directory.ActiveDirectorySecurityRealm.forceLdaps=true. So to sum up, the following parameters need to be added:
-
-Djavax.net.ssl.trustStore=<FULL_PATH_TO_JENKINS_CACERTS> -
-Djavax.net.ssl.trustStorePassword=<PASS_FOR_JENKINS_CACERTS> -
-Dhudson.plugins.active_directory.ActiveDirectorySecurityRealm.forceLdaps=true
Step 5. Set-up AD plugin in Jenkins in secure mode
Please, take special caution in the Domain Controller field by using a secure port, by default 3269.
As an example:
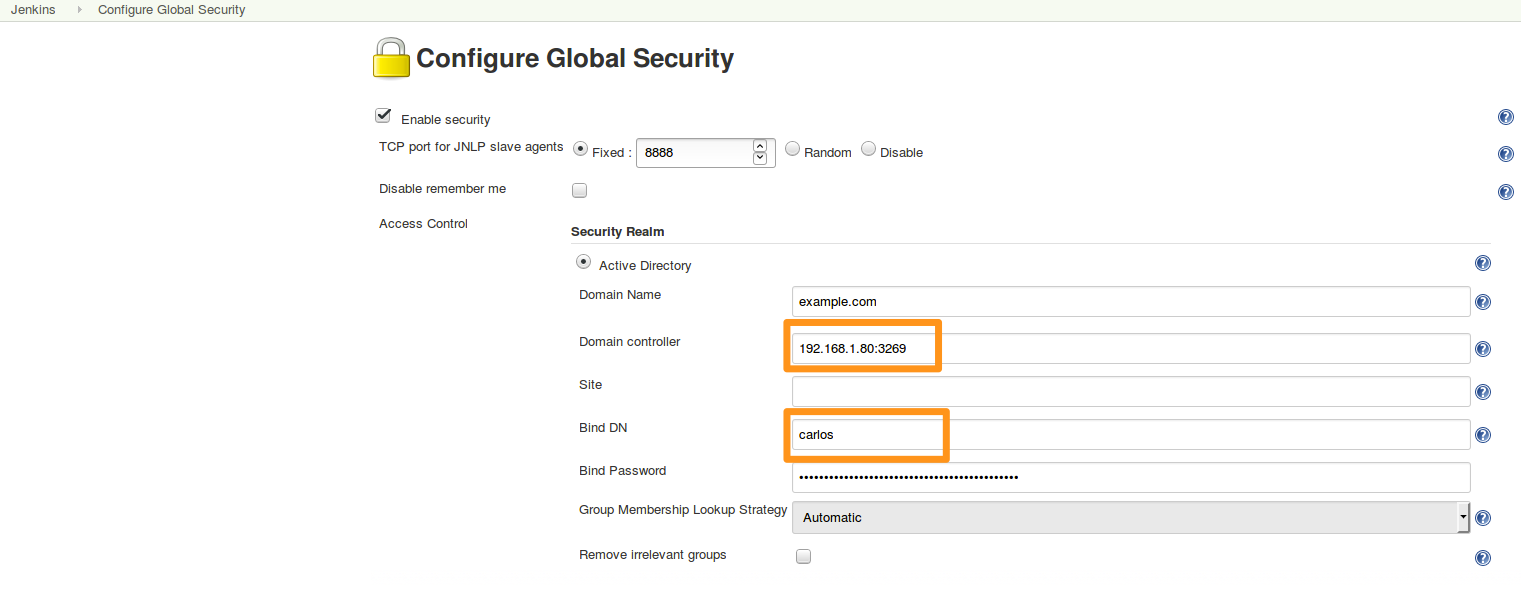
Step 6. Check the integration is working via LDAPS
Create a Dedicated logger, including hudson.plugins.active_directory.ActiveDirectorySecurityRealm
After trying to Log in with an AD user ("userX" on the below example) using a trusted domain ("192.168.1.80" on the example), expected output for dedicated logger would look like:
nov 18, 2016 5:05:27 PM FINE hudson.plugins.active_directory.ActiveDirectorySecurityRealm$DescriptorImpl bind Connecting to ldaps://192.168.1.80:3269/ nov 18, 2016 5:05:27 PM FINE hudson.plugins.active_directory.ActiveDirectorySecurityRealm$DescriptorImpl bind Binding as userX@contoso.com to ldaps://192.168.1.80:3269/ nov 18, 2016 5:05:27 PM FINE hudson.plugins.active_directory.ActiveDirectorySecurityRealm$DescriptorImpl bind Bound to 192.168.1.80:3269 nov 18, 2016 5:05:28 PM FINE hudson.plugins.active_directory.ActiveDirectorySecurityRealm$DescriptorImpl bind Connecting to ldaps://192.168.1.80:3269/ nov 18, 2016 5:05:28 PM FINE hudson.plugins.active_directory.ActiveDirectorySecurityRealm$DescriptorImpl bind Binding as CN=userX,OU=users,OU=support1,DC=example,DC=com to ldaps://192.168.1.80:3269/ nov 18, 2016 5:05:29 PM FINE hudson.plugins.active_directory.ActiveDirectorySecurityRealm$DescriptorImpl bind Bound to 192.168.1.80:3269
According to those logs, we can conclude that the integration with the trusted Active Directory domain has been done successfully.