Issue
External CloudBees client controllers require the configuration of the Kubernetes Plugin in order to provision ephemeral build agents on Openshift 4.x.
Resolution
CloudBees CI on modern cloud platforms on Openshift doesn’t require the Kubernetes Plugin to be configured because it is automatically configured with the installation of CloudBees CI software on those platforms. External client controllers do require the setup of the Kubernetes Plugin though. For Openshift 4.x, create a non-expiring token and add it to the controller to authenticate.
Openshift 4.x
Openshift 4.x uses Oauth tokens.
To correctly setup the Kubernetes Plugin within Jenkins you’ll need to create a serviceaccount in Openshift granting privileges to the serviceaccount and generating a non-expiring token to use in the controller.
Create a non-expiring token for a service account
-
oc login [url] -u [username] -p [password] -
oc new-project cloudbees-core -
oc create serviceaccount jenkins -
oc policy add-role-to-user edit system:serviceaccount:cloudbees-core:jenkins -n cloudbees-core -
oc serviceaccounts get-token jenkins -n cloudbees-core -
Save the token value returned by the last command
-
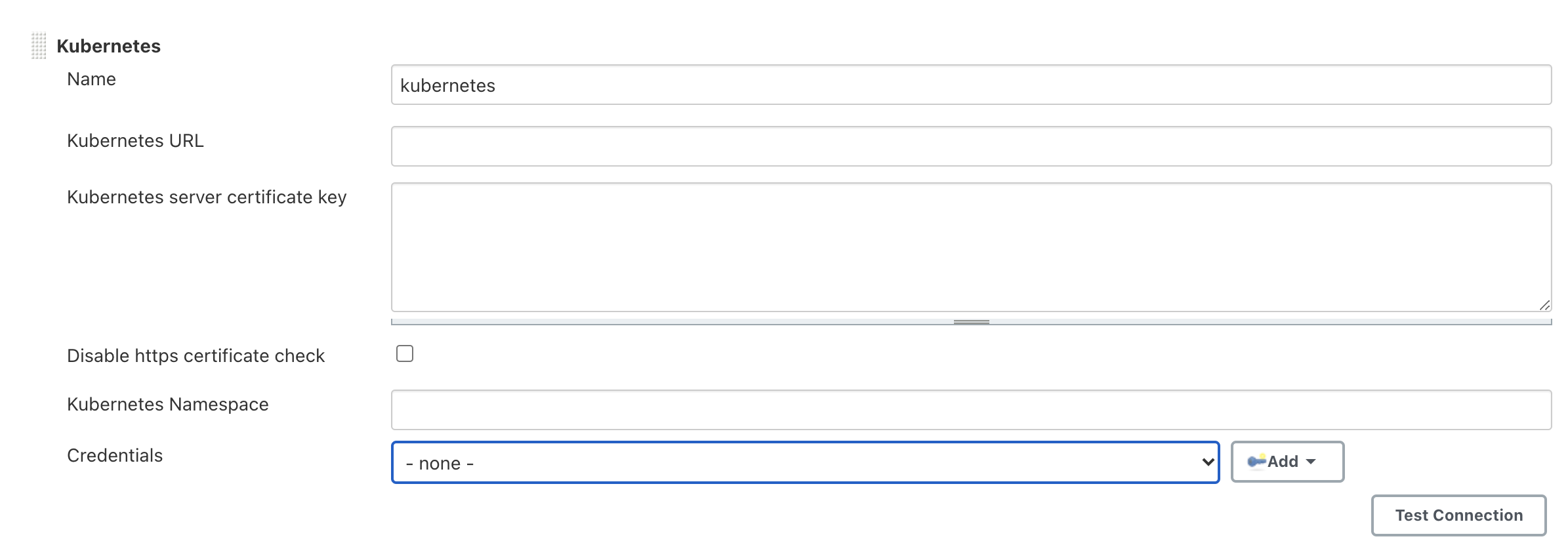
Go to Manage Jenkins > Manage Nodes and Clouds > Configure Clouds and click on Kubernetes cloud details for your Kubernetes cloud item (for Openshift)
-
Configure Kubernetes URL and Kubernetes server certificate key
-
Add credential and create a credential of type
Secret textwhere thesecretis the token you obtained from step #6