Issue
-
I want to configure Ingress Nginx behind CloudFlare.
-
After deploying CloudBees CI / Ingress Nginx behind CloudFlare, some URL are redirecting to
https://$DOMAIN:80/...
Explanation
CloudFlare SSL service acts a Reverse Proxy in front of the Ingress Controller (and the Load Balancer backing the Ingress Controller service). Roughly the traffic looks like this:
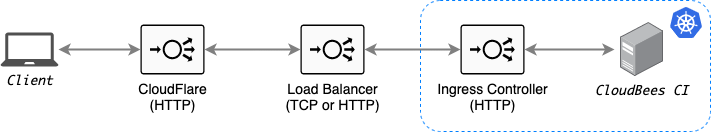
Traffic between the Client (the browser) and CloudFlare is encrypted. Traffic between CloudFlare and the backend (i.e. the Ingress Controller and / or the Load Balancer backing the Ingress Controller service) may or may not be encrypted based on CloudFlare SSL configuration.
There are 2 particular behaviors that must be considered about CloudFlare:
-
It sets the
X-Forwarded-Protoheader but does not set theX-Forwarded-Portheader (How does Cloudflare handle HTTP Request headers ?).** -
There are different CloudFlare SSL Options that controls how the traffic between CloudFlare and the backend (Ingress Controller) is handled and forwarded to the backend
This brings some complexity to the overall Ingress deployment. In scenarios where the SSL option Off or Flexible is used, CloudFlare sets the header X-Forwarded-Proto to https and forward traffic on port 80 to the backend. This can cause all sorts of issues:
-
endless redirect loops (see Cloudflare SSL options incompatible with your origin web server)
-
wrong redirection and troubles to connect to Operations Center due to inconsistent values for
X-Forwarded-*(see Reverse Proxy Troubleshooting Guide and Cannot Log In to Connected controllers with Operations Center SSO after Upgrading to 2.222.4.3)
Both CloudFlare and the Ingress Controller deployment must be configured accordingly.
Resolution
There is no single absolute solution that would work for every scenario. Depending on the Ingress Controller solution chosen and the CloudFlare SSL Options, a specific configuration must be used. This article provides a recommendation that hopefully can apply to most CloudBees CI deployment.
When following the setup of CloudBees CI, the Ingress deployment is eventually setup to be secured:
-
terminates TLS at either Ingress or Load Balancer level
-
redirects HTTP traffic to HTTPS
To make CloudFlare work in front of those setups the more straightforward solution is to:
-
configure CloudFlare SSL with Full, Full (Strict) or Strict (SSL-Only Origin Pull) (See CloudFlare SSL Options) so that traffic is forwarded to Ingress Controller on port
443- that is also recommended so that traffic between CloudFlare and the Ingress Controller is always secured. -
configure the Ingress Controller to set the
X-Forwarded-headers *if there are not already set (for example with Ingress Nginx, use the option use-forwarded-headers: "true")