Issue
-
operations center and/or the controller is configured as a TLS endpoint using a self-sign certificate
-
The shared agent cannot be connected against OC
-
The shared agent is never provisioned to the controller
-
The following stacktrace is visible on either operations center or controller logs.
Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision Caused by: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision at sun.security.validator.PKIXValidator.doBuild(Unknown Source) Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision at sun.security.validator.PKIXValidator.engineValidate(Unknown Source) Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision at sun.security.validator.Validator.validate(Unknown Source) Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision at sun.security.ssl.X509TrustManagerImpl.validate(Unknown Source) Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision at sun.security.ssl.X509TrustManagerImpl.checkTrusted(Unknown Source) Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision at sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(Unknown Source) Apr 25, 2017 5:45:54 PM INFO com.cloudbees.opscenter.client.cloud.CloudImpl provision ... 14 more
Environment
-
CloudBees Jenkins Enterprise - Operations center
-
operations center and/or controller using a TLS end-point with a self-sign certificate.
Resolution
Prior to Operations Center JNLP Agent Controller Plugin 2.60.0.3 (included in CloudBees Jenkins Operations Center 2.60.3.1), the agent options - such as -noCertificateCheck - do not work on shared agents/clouds.
|
The recommended approach is to create a trustStore for the shared agent. The way to create a trustStore is documented on the KB How to install a new SSL certificate.
The first thing you need to do is to get the certificate from the operations center and the controller - in case those are different. You can do this by using:
keytool -printcert -rfc -sslServer <CJOC_HOSTNAME>:<CJOC_PORT>
Example:
pegaso:~ fbelzunc$ keytool -printcert -rfc -sslServer cjoc.example.com:9090 BEGIN CERTIFICATE MIIDNjCCAh4CCQCOd+0yDiOfpzANBgkqhkiG9w0BAQUFADBdMQswCQYDVQQGEwJFUzETMBEGA1UE CBMKU29tZS1TdGF0ZTEhMB8GA1UEChMYSW50ZXJuZXQgV2lkZ2l0cyBQdHkgTHRkMRYwFAYDVQQD FA0qLmV4YW1wbGUuY29tMB4XDTE3MDQyNjA2NDcwOFoXDTE4MDQyNjA2NDcwOFowXTELMAkGA1UE BhMCRVMxEzARBgNVBAgTClNvbWUtU3RhdGUxITAfBgNVBAoTGEludGVybmV0IFdpZGdpdHMgUHR5 IEx0ZDEWMBQGA1UEAxQNKi5leGFtcGxlLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC ggEBALhdyeOfOE0XBr/el5kl9tyq78J/TFeX5M1N77qboS6JKOIKXBuzYMeJm2rkuaSq9oAuuvbf EwHtWK4D+nGR8MXjhJoOvBzaQmHhi6zhhCFpmP6Yzwzk8JOase/3PPiRBtJnGsFFsSs3ywsmAB+/ CL2vh9ekVXpSHS/cM0nnkPyVQyPJNVrLCixDoByM/BJXhsb9tZP7UVzInwidjkwIlgRiGgO9naAI A3jkRDfeceRfzj/Wx7gxgk7EWM3U9DpR8EpW/3enrxnzvSZZyFnCJ7OMasSyYXV0DnUUuoG7vSDH LGsNzyWIbDbwXN5eIfKKXIFzCJjeDJgsJ0v1y8mlzPUCAwEAATANBgkqhkiG9w0BAQUFAAOCAQEA pJUB604M5qcmziG09Hz/Uv0Gc218gx+2tOUT5KRuI3882AyZ6dg23Mg6Ugz3DT0NiWSXhiHGTVLn g3UlASjP4LJiSdwBGpdwFKATzQHzRDph5iPO1Tld//UC/6wdPwygYTV5fsWe65gopobY3GwTWN9V Pe0XrYB/2xSYEAjFT70yTQFAotmzSXrZQ/E0NYfAWSuUWI+oUOzDmCQ8MCNEDIARenoLMAUH+O/h 0ZGVXND5pvMqwaLe0qp8Oyk8YoFiI+ZCxKFKUJ8hbR14o60HBg5iAxK5mfRLcZL0FqdgZEhnln+h olN89/gx9K0/V4O/Ic9LBsg+0YvuKE3X5ItOhw== END CERTIFICATE
Then, you need to follow the following points if the KB article
-
Create a custom keystore from the JVM keystore
-
Import your certificate
and finally, add the certificate to the Agent startup parameters.
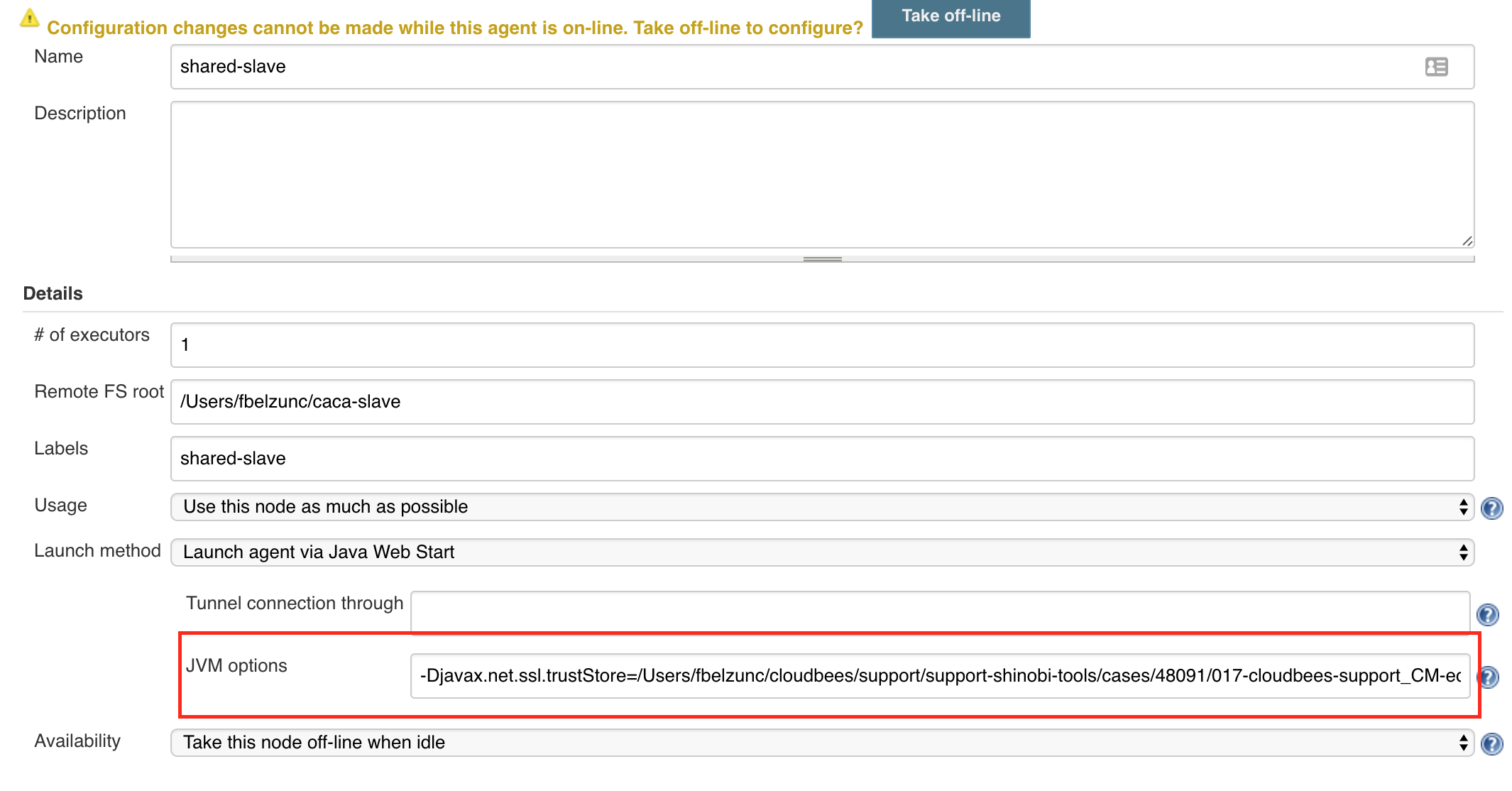
-Djavax.net.ssl.trustStore=/var/jenkins-home/.keystore/cacerts -Djavax.net.ssl.trustStorePassword=changeit