Issue
-
I want to setup an Amazon Classic Elastic Load Balancer (ELB) for CloudBees Jenkins Operations Center in High Availability
Environment
-
CloudBees Jenkins Operations Center or Client controller
-
Amazon Classic Elastic Load Balancer (ELB)
-
AWS
Resolution
This setup will follow the Load Balancer configuration from the main HA (active/passive) document but will specific to the Amazon ELB.
| This document will not cover the steps for the 'Amazon Application Load Balancer' as it is unsupported for the following reasons: |
-
It cannot route TCP Traffic
-
It requires Multi-AZ
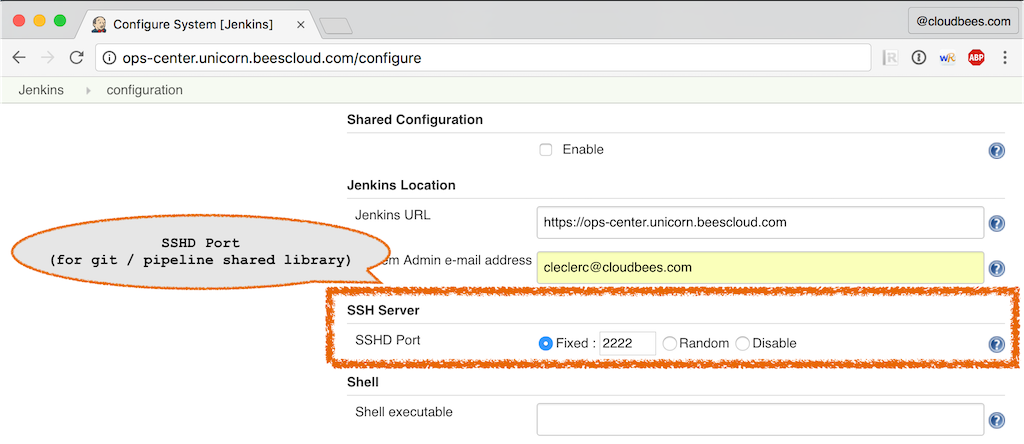
Verify your SSHD Listen Port (optional: read below)
SSHD routing is required if using the Git internal server of Jenkins to manage a "Pipeline global shared library". If you are using this feature, determine your SSHD port by:
-
Navigate to "Manage Jenkins / Configure System"
-
Ensure that the SSHD Port is set to a fixed value (e.g. 2222)
Create an Amazon Classic Elastic Load Balancer
-
Navigate to the AWS Admin Console / EC2"
-
Create a new Amazon Classic ELB load balancer
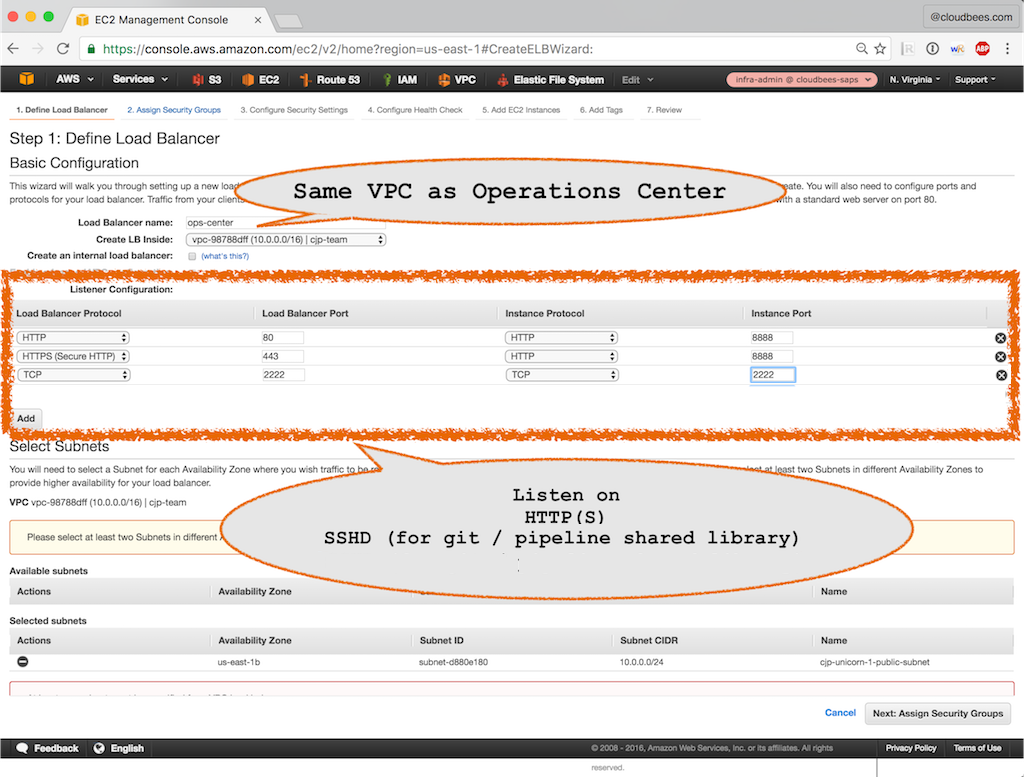
Step 1: Define Load Balancer
-
Load Balancer name: Name of the Amazon ELB load balancer (e.g. "ops-center")
-
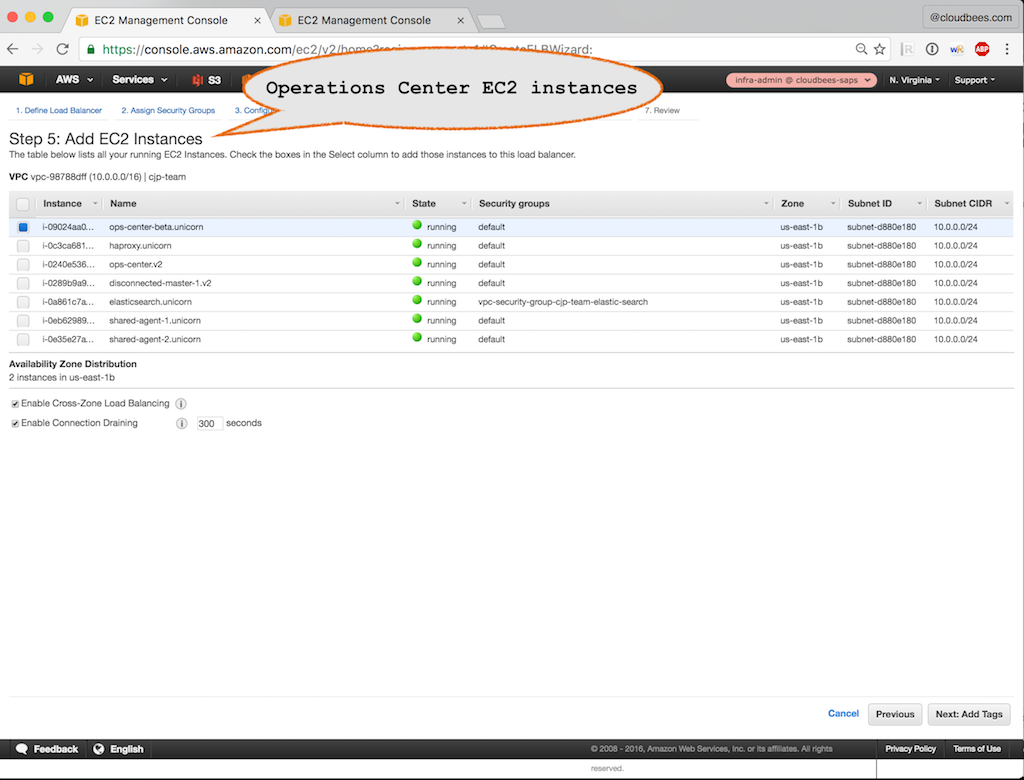
Create LB Inside: VPC in which the load balancer will be created. Should be the VPC in which the Operations Center EC2 VMs are started
-
Listener Configuration
-
HTTP traffic
-
Load Balancer Protocol: HTTP
-
Load balancer port: 80
-
Instance Protocol: HTTP
-
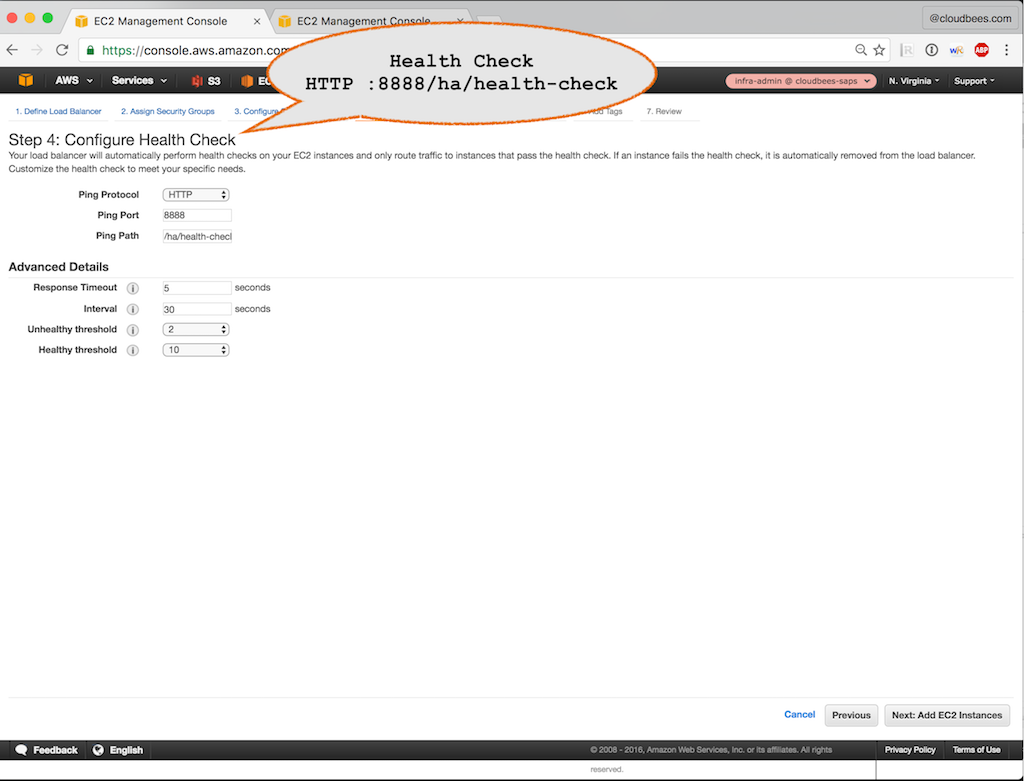
Instance Port: 80 (a listen port on Operations Center instances that redirect to HTTPS). If HTTPS is not used, then enter the HTTP endpoint of Operations Center (e.g. 8888)
-
-
HTTPS (skip if HTTPS is not used)
-
Load Balancer Protocol: HTTPS (Secure HTTP)
-
Load balancer port: 443
-
Instance Protocol: HTTP
-
Instance Port: 8888 (HTTP endpoint of Operations Center)
-
-
SSHD / Git (skip if 'Pipeline global shared library' is not used)
-
Load Balancer Protocol: TCP
-
Load balancer port: 2222
-
Instance Protocol: TCP
-
Instance Port: 2222 (the "SSHD Port" defined on Operations Center)
-
-
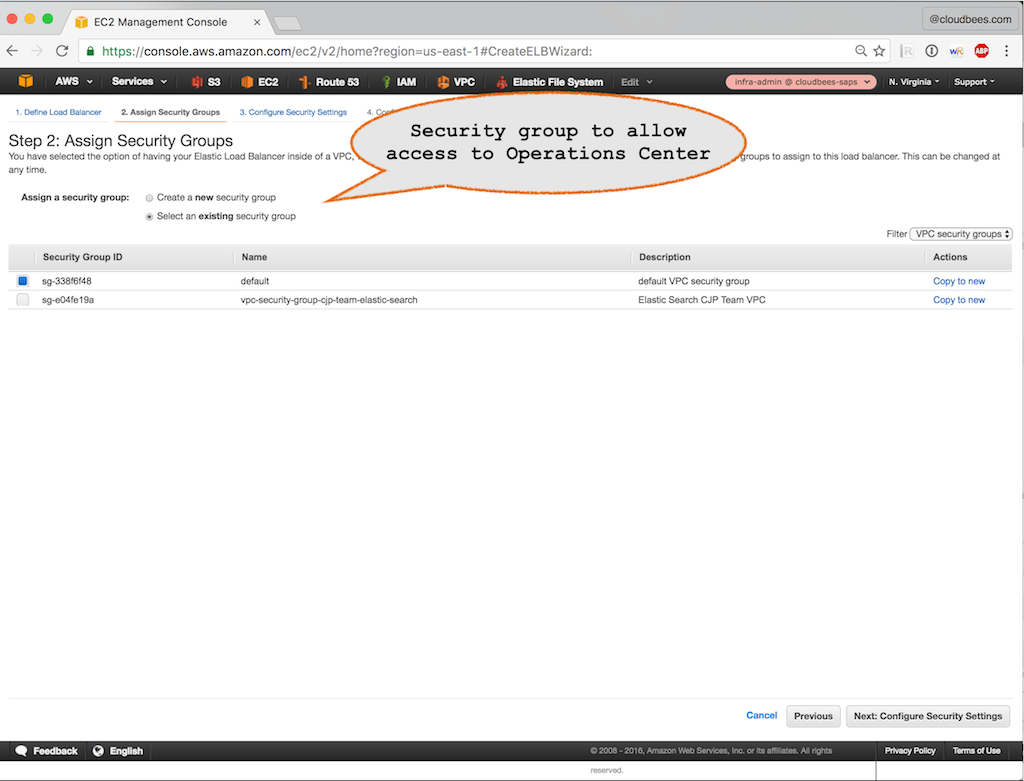
Step 2: Assign Security Group
Choose a security group that allows access to the desired groups of users
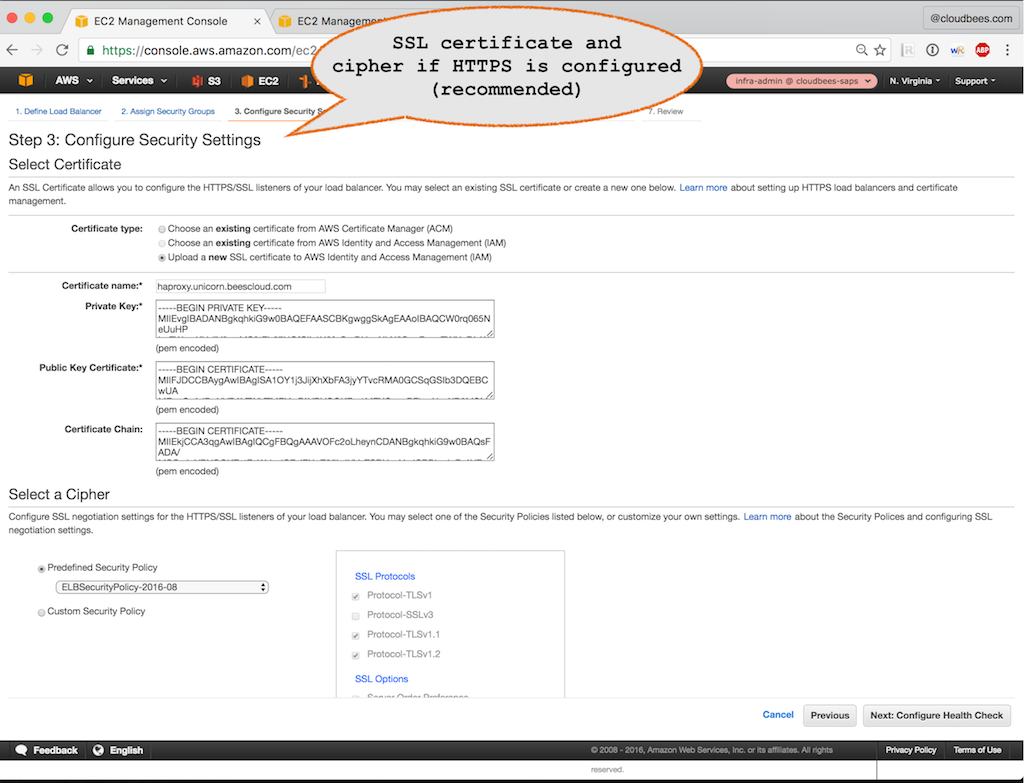
Step 3: Configure Security Settings (optional: read below)
Needed if HTTPS / SSL is enabled. Note: It is required to use SSL certificates that are by default trusted by the JVM. Using a self signed certificate or a certificate generated by an enterprise Certificate Authority requires a better understanding of HTTPS / SSL and more configuration.