Resolution
| This model is not recommended at all and it is just described in case the policy of your organization forces you to really implement SSL on each Jenkins box. The best practice is to implement the SSL at ELB/…/HAProxy level instead of doing it on each box separately. |
Architecture
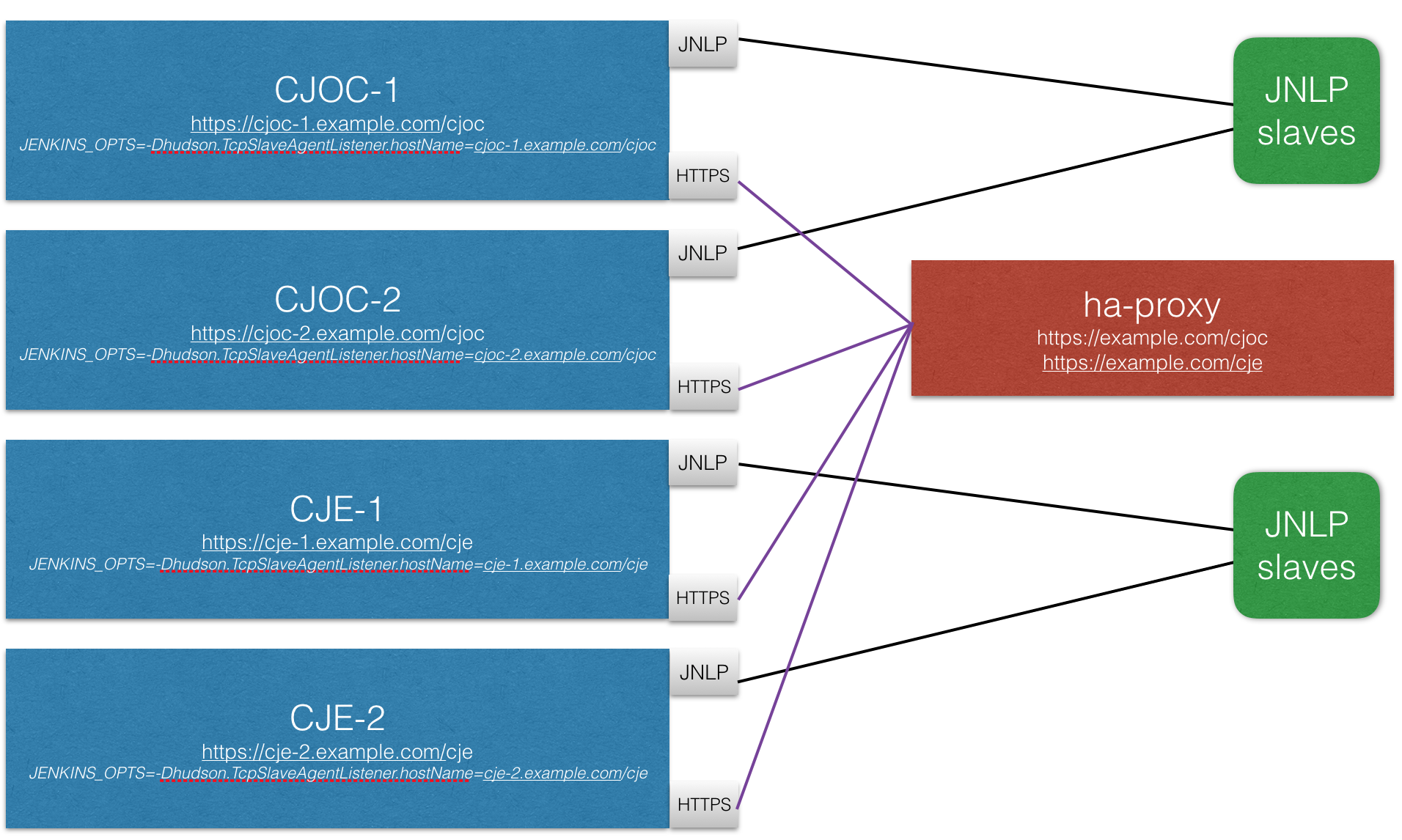
The following KB article is based on the below architecture where an ha-proxy is in front of all the boxes.
Creating a Private Key and a Self-Signed SSL Certificate
The openssl library is required to create your own ssl certificate.
-
Generate a Server password key
openssl genrsa -des3 -passout pass:changeit -out server.passwd.key 2048
-
Generate a private key
server.key
openssl rsa -passin pass:changeit -in server.passwd.key -out server.key
-
Delete the password server key
rm server.passwd.key
-
Generate a server certificate
openssl req -new -key server.key -out server.csr
-
Generate the SSL certificate
server.crt
The self-signed SSL certificate is generated from the server.key private key and server.csr files.
openssl x509 -req -days <NUMBER OF DAYS> -in server.csr -signkey server.key -out server.crt
Configure Operations Center to use SSL
-
Edit your jenkins configuration file adding in the
JENKINS_ARGSsection:
--httpsCertificate=/path/to/cert/server.crt --httpsPrivateKey=/path/to/key/server.key --httpsPort=443 --httpPort=-1
-
/etc/default/jenkins-oc: location for most of the Linux distributions. -
/etc/sysconfig/jenkins-oc: location for RedHat/CentOS distribution. -
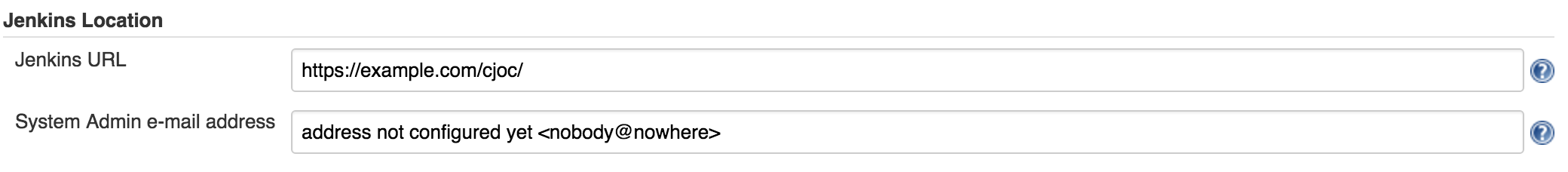
In Manage Jenkins -> Configure System configure the new URL
-
Follow How to install a new SSL certificate to install the SSL certificate in OC
-
After changing the Jenkins URL you will need now to release all the client controller and re-attach them again to update the new URL they need to reach out.
Configure Client controllers to use SSL
-
Edit your jenkins configuration file adding in the
JENKINS_ARGSsection:
--httpsCertificate=/path/to/cert/server.crt --httpsPrivateKey=/path/to/key/server.key --httpsPort=443 --httpPort=-1
-
/etc/default/jenkins: location for most of the Linux distributions. -
/etc/sysconfig/jenkins: location for RedHat/CentOS distribution.
Now, you need to add your OC self-signed certificate to your controller keystore with keytool.
keytool -import -alias server -keystore $JAVA_HOME/jre/lib/security/cacerts -file server.cer
-
Notice that
server.ceris the self sign certificate from OC
Once the command is executed, then the final part is to make sure that the JVM uses the correct cacert file. To do this please add the following arguments to your controllers Java startup process:
-Djavax.net.ssl.keyStore=$JAVA_HOME/jre/lib/security/cacert -Djavax.net.ssl.keyStorePassword=changeit
Configure the ha-proxy
The below ha-proxy configuration represents a configuration example for the architecture presented before.
For ssl, ensure that in the back end the checks are done with check ssl verify none and in the front-end you are injecting the certificate with ssl crt /path/to/pem/server.pem.
To generate server.pemyou can use cat /path/to/crt/server.crt /path/to/key/server.key > server.pem
#---------------------------------------------------------------------
# Global settings
#---------------------------------------------------------------------
global
maxconn 4000
log 127.0.0.1 local0
log 127.0.0.1 local1 notice
defaults
log global
mode http
retries 3
timeout client 50s
timeout connect 5s
timeout server 50s
timeout http-keep-alive 10s
backend cjoc
balance roundrobin
option httpchk HEAD /cjoc/ha/health-check
server joc-ha1 cjoc-1.example.com:443 check ssl verify none
server joc-ha2 cjoc-2.example.com:443 check ssl verify none
backend cje
balance roundrobin
option httpchk HEAD /cje/ha/health-check
server je-ha1 cje-1.example.com:443 check ssl verify none
server je-ha2 cje-2.example.com:443 check ssl verify none
frontend cjoc
bind *:443 ssl crt /path/to/pem/server.pem
timeout client 15m
acl cje-ha path_beg -i /cje
acl cjoc-ha path_beg -i /cjoc
use_backend cjoc if cjoc-ha
use_backend cje if cje-ha
# monitor port
listen status
bind 0.0.0.0:8088
stats enable
stats uri /