Issue
Control environment variables inside a Docker container with the Docker Pipeline plugin.
Resolution
By default, when using the Docker Pipeline plugin the node’s environment variables will not be propagated to the docker container - since with Docker you want to get isolate environments. You can check this here
However, if at Node level (http/s://
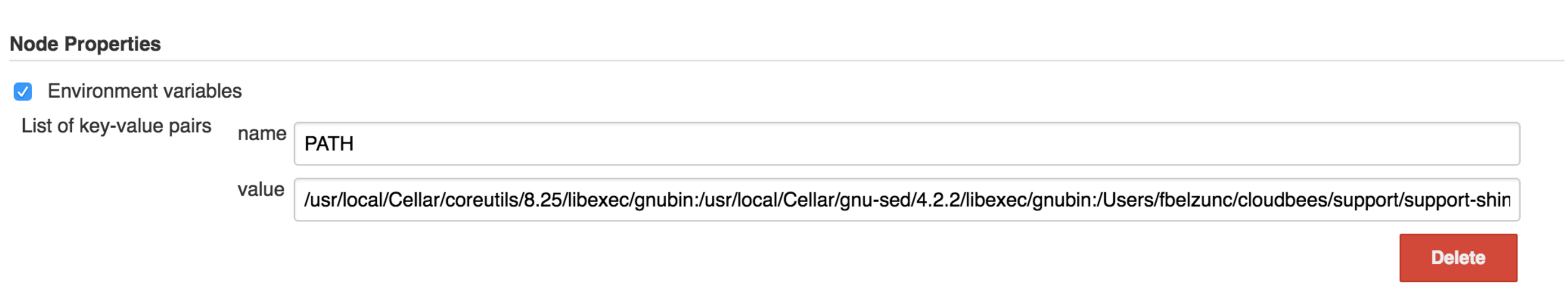
If you would like to override again what is injected at Node level then you will need to use withEnv step.
node ('linux-agent') { withEnv(['PATH=/usr/local/sbin:/usr/local/bin:/usr/local/bin:/usr/bin:/bin']) { docker.image('maven:3.3.3-jdk-8').inside { sh 'echo $PATH' sh 'mvn --version' } } sh 'echo $PATH' }
This article is part of our Knowledge Base and is provided for guidance-based purposes only. The solutions or workarounds described here are not officially supported by CloudBees and may not be applicable in all environments. Use at your own discretion, and test changes in a safe environment before applying them to production systems.