Issue
We have a requirement to allow teams to have access to Job/Configure without any permissions within Client/Managed Controller Configure and Client/Managed Controller Lifecycle. We can not allow development teams to override the configuration on their controllers.
Resolution
First of all, it is worth noting that enabling the permission Job/Configure greys out the permissions Client/Managed Controller Configure and Client/Managed Controller Lifecycle, because granting the former implies granting the latter.
That being said, let’s explain how this use case can be covered. First, in the role matrix, you have to add a create role granting the permission Job/Create. (browse and develop roles are the default ones added besides administer when selecting RBAC → Typical initial setup (ignoring existing authorization strategy)).
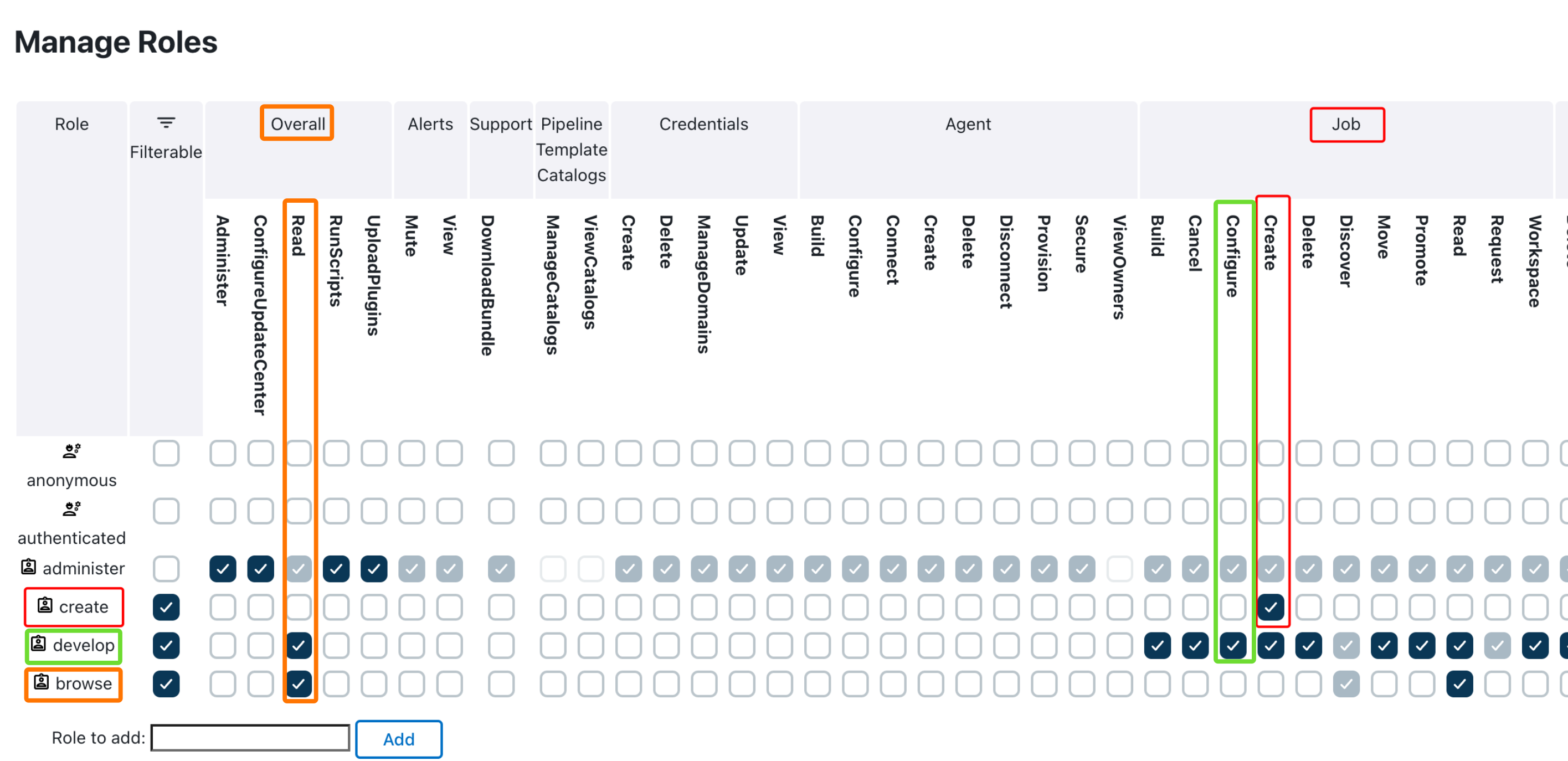
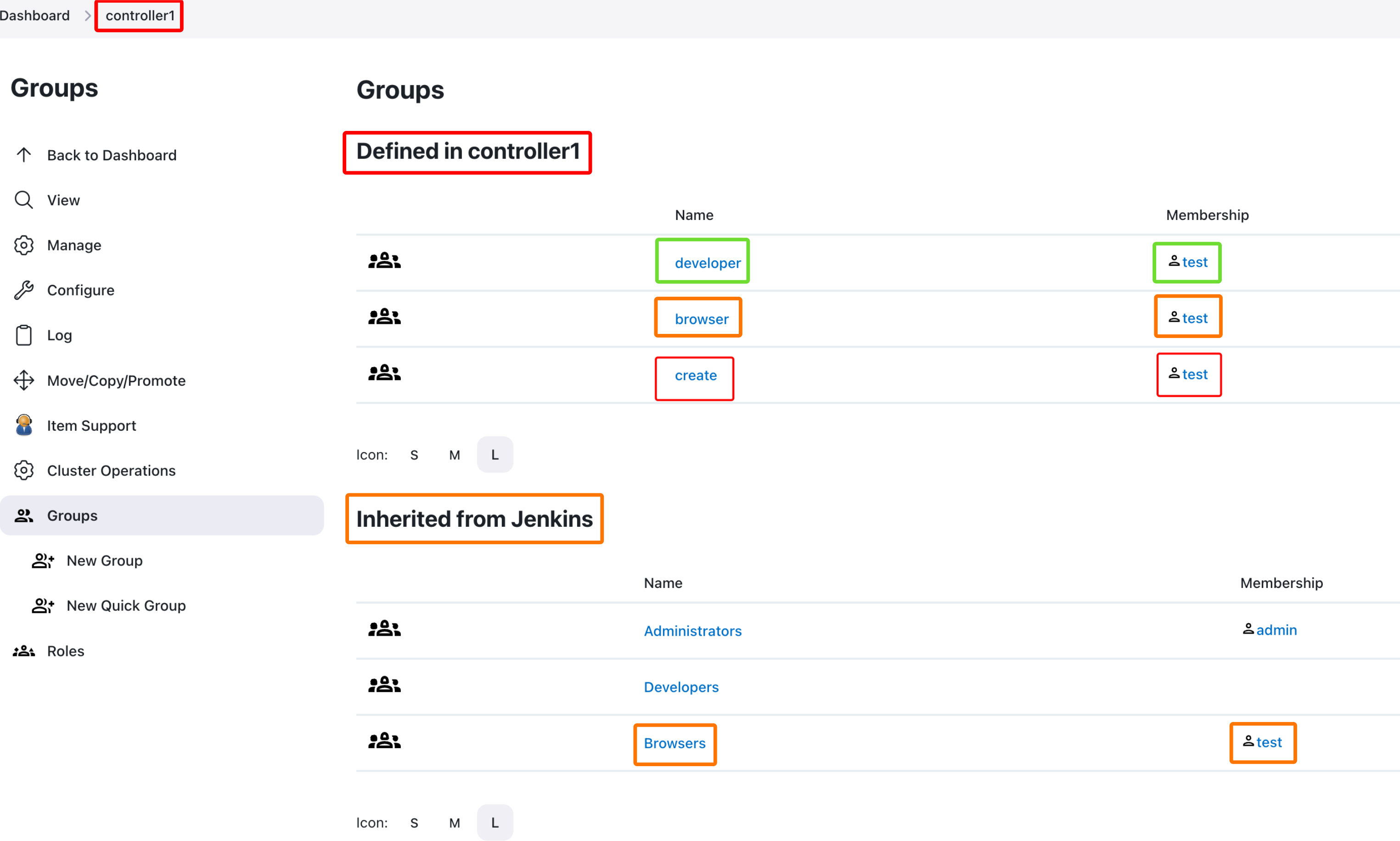
Then, using the principles to achieve RBAC granularity from RBAC: Limit folder access, we will configure browser, developer, and create groups as shown in the following screenshot.
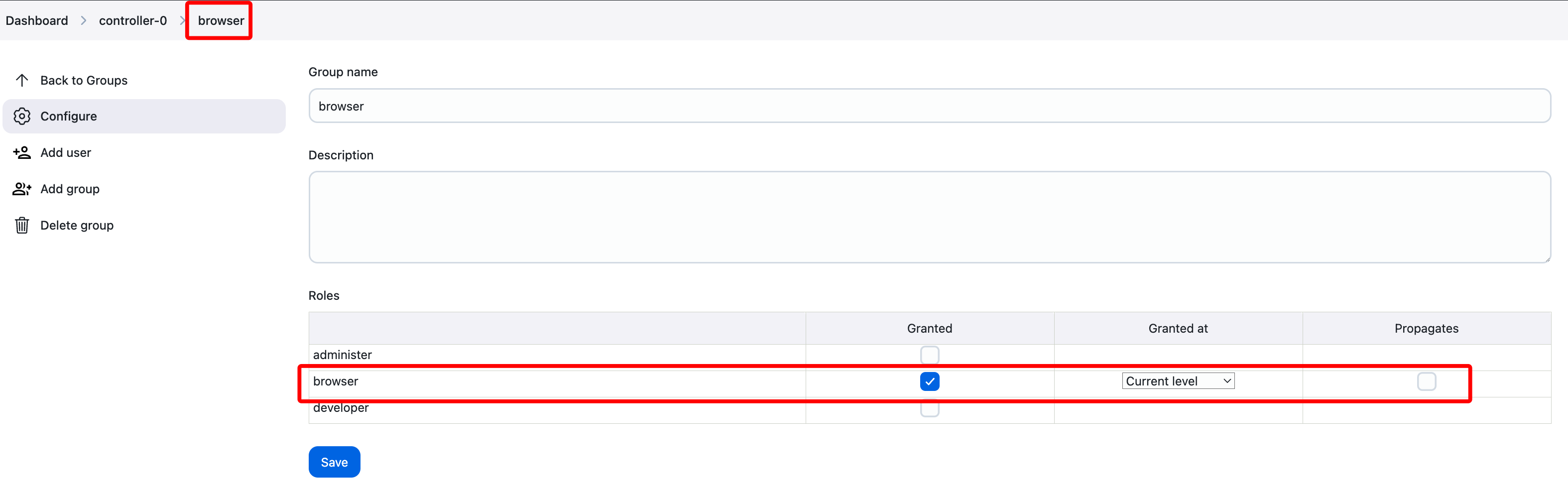
Then, we will configure the browser group at current level without propagation at CJOC and at controller level:
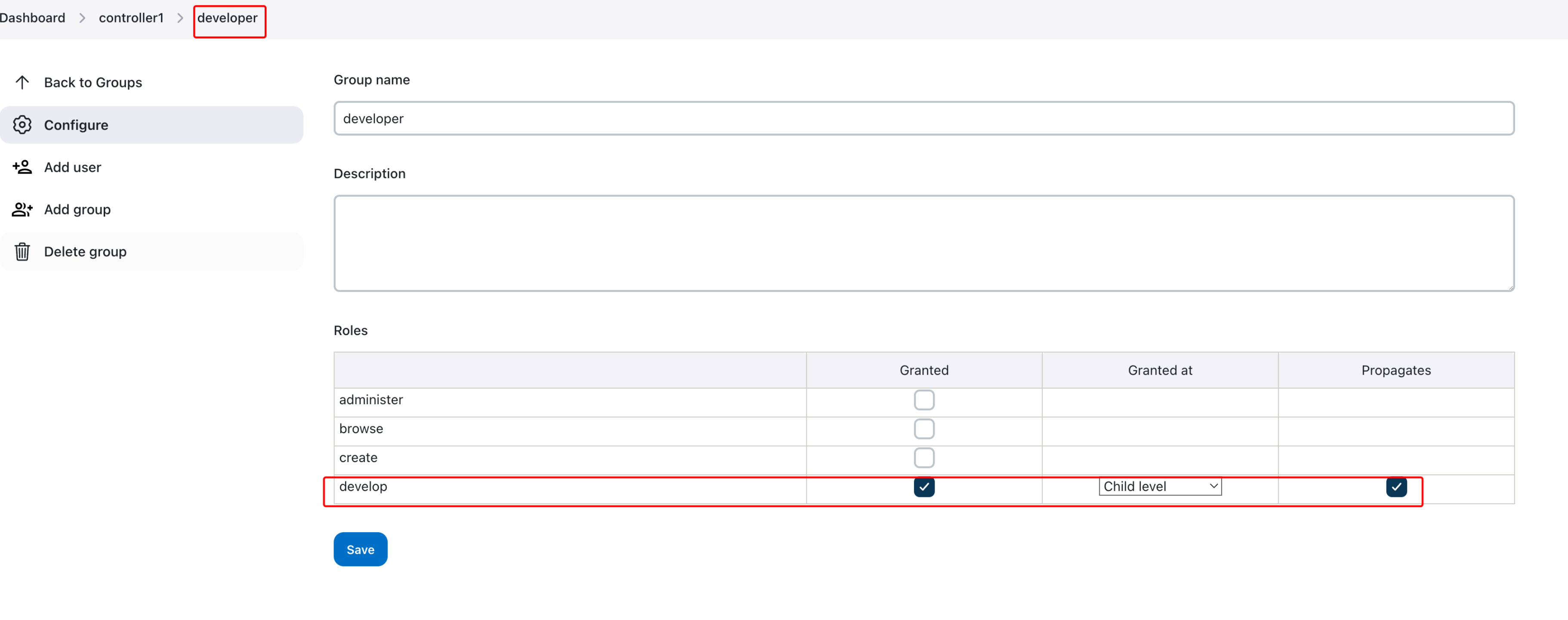
Following, we will configure the developer group at child level with propagation at controller level:
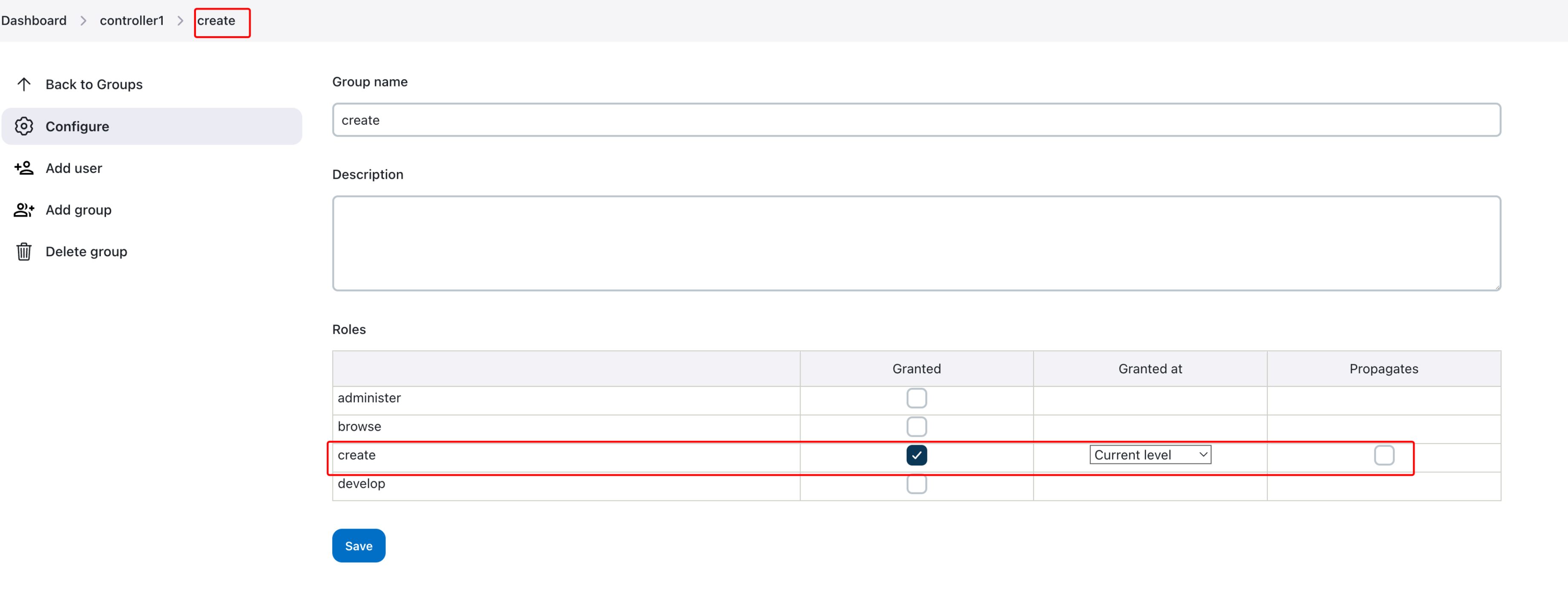
Finally, we will configure the create group at current level without propagation at controller level:
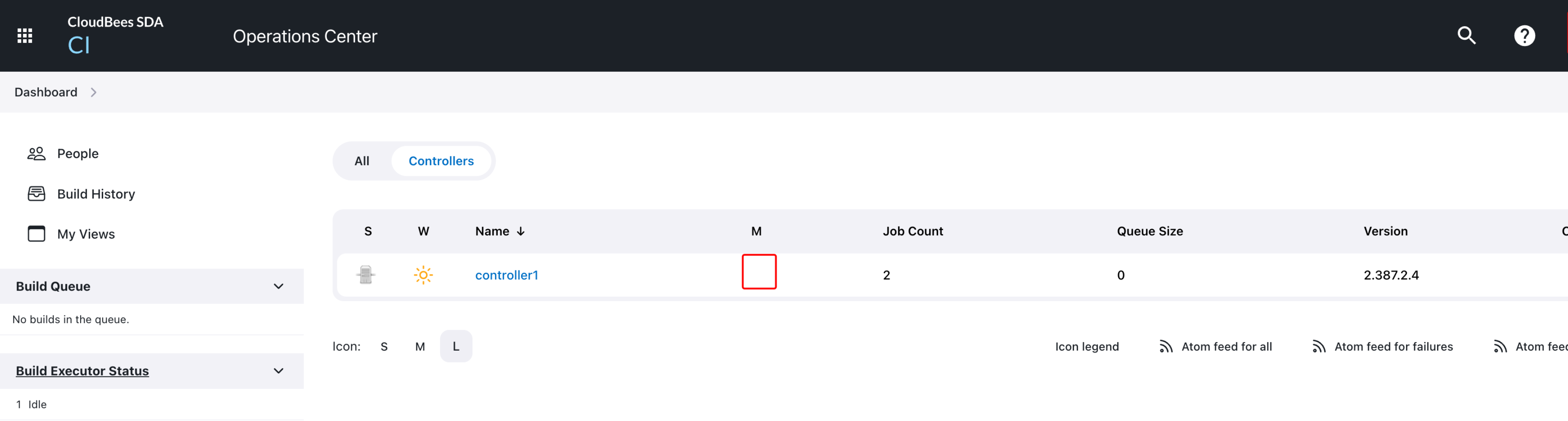
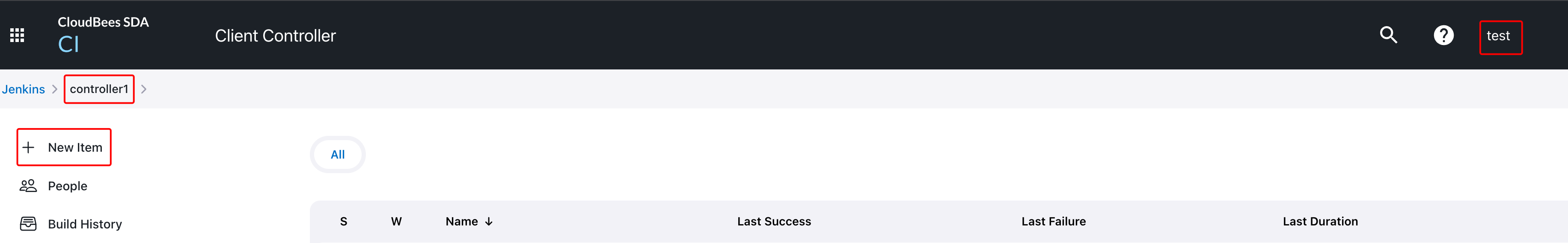
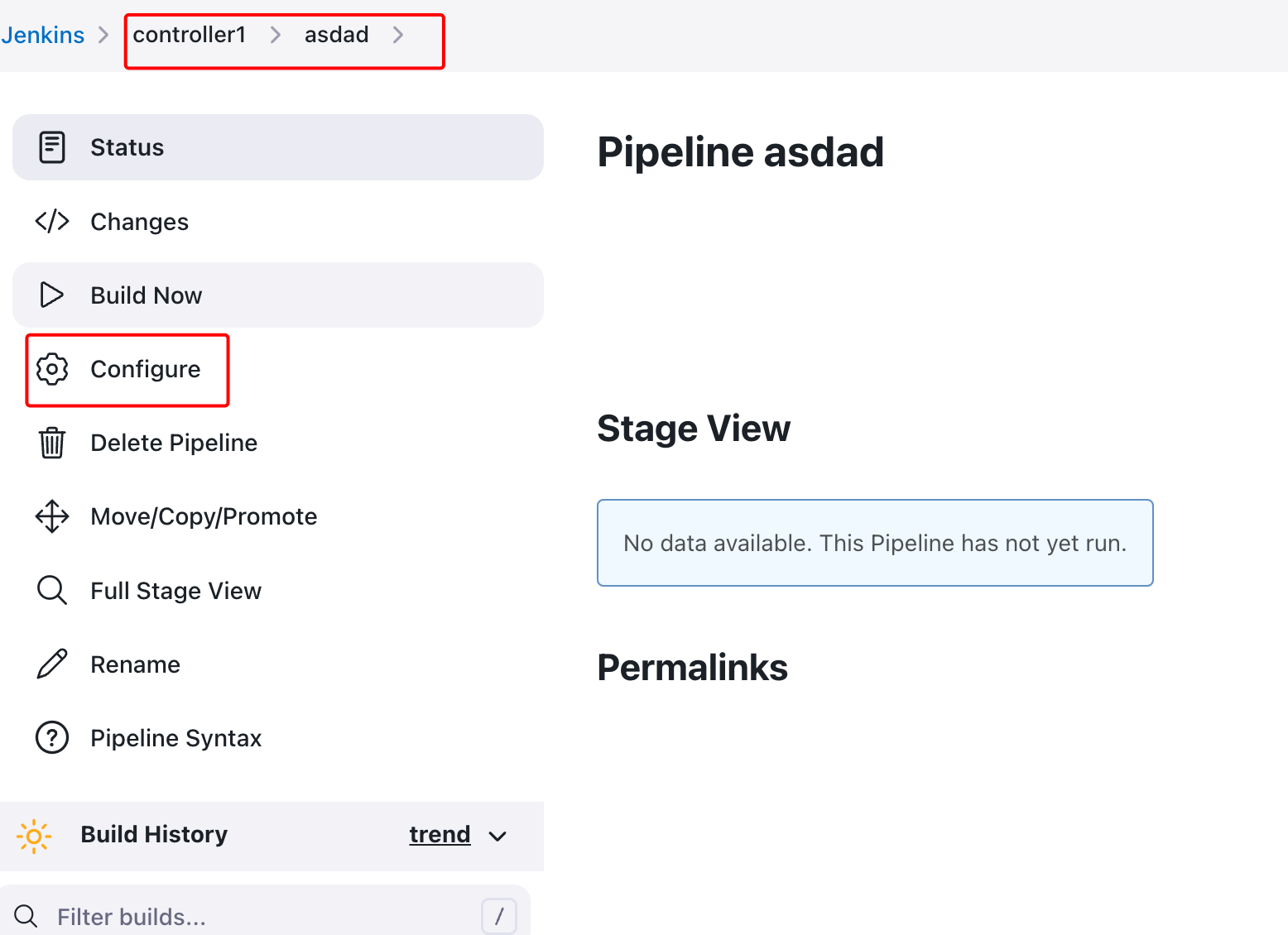
You can check the results from the previous RBAC configuration in the below 3 screenshots (at CJOC level, at controller level, and at job level, respectively).