Issue
-
I am trying to update or download a plugin using the Plugin Manager in a managed controller that is configured from the Operations Center to use CloudBees Update Center (at the operations center level
Update center→Specify update center for Controller) and I am getting the following error:
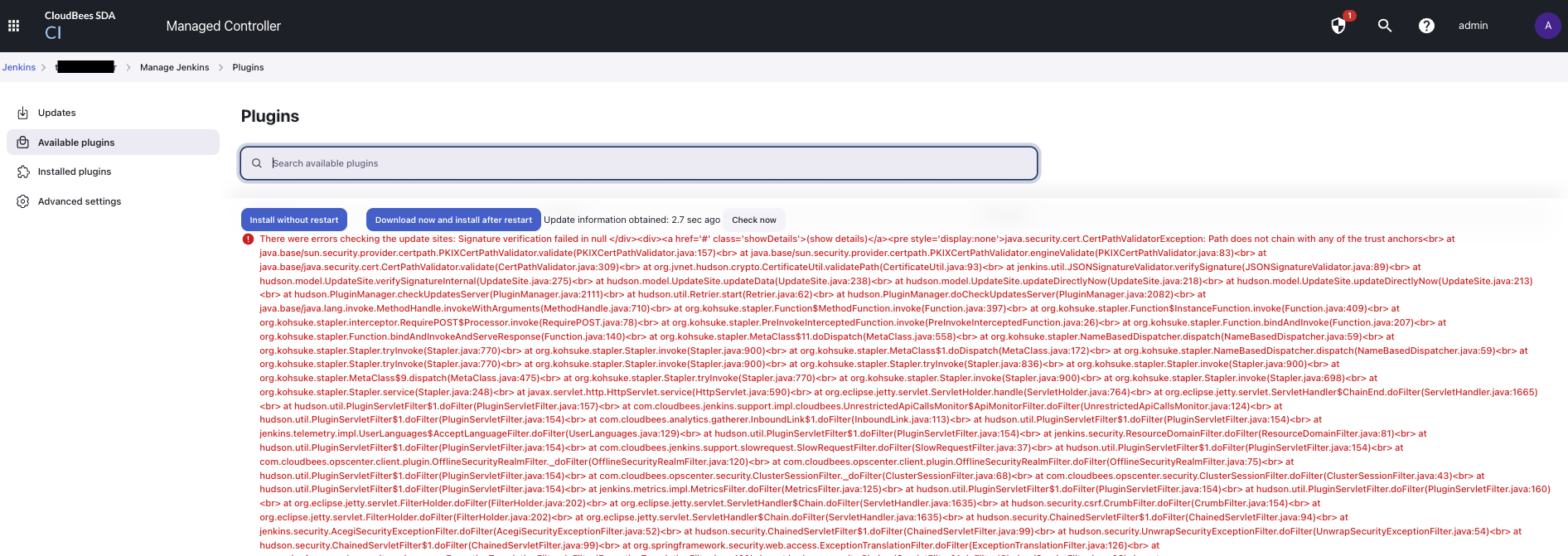
There were errors checking the update sites: Signature verification failed in null </div><div><a href='#' class='showDetails'>(show details)</a><pre style='display:none'>java.security.cert.CertPathValidatorException: Path does not chain with any of the trust anchors<br>...
Environment
-
CloudBees CI on modern cloud platforms - operations center until 2.414.1.4
-
CloudBees CI on modern cloud platforms - managed controller until 2.414.1.4
-
CloudBees CI on traditional platforms - operations center until 2.414.1.4
-
CloudBees CI on traditional platforms - client controller until 2.414.1.4
Explanation
The CloudBees Update Center certificate has been updated. CloudBees Update Center plugin, which is installed on Operations Centers, and provides the option to specify an update center at controller provisioning (custom or not), does not use this new certificate yet.
Resolution
This issue in CloudBees Update Center plugin is resolved in the 2.414.2.2 release of CloudBees CI.
Workaround
There are two workarounds to avoid the signature check fail:
-
Either you disable the Signature Check in your controllers,
-
or you manually import the certificate to
JENKINS_HOME/update-center-rootCAsin your controller’s file system.
None of the workarounds will require a restart.
How to disable the Signature Check
Whether the Update Center’s certificate signature is going to be checked in the controller or not is handled by the Jenkins System property hudson.model.DownloadService.signatureCheck. You can disable the signature check by running the following line from your controller’s Groovy console:
hudson.model.DownloadService.signatureCheck = false
This will immediately solve the issue. However, if you restart the instance, you will see that the value is lost. To make it persistent, you need to add it as a startup argument as well:
-Dhudson.model.DownloadService.noSignatureCheck=true
Please note that this is a temporary measure and we recommend that you re-enable signature checking after you upgrade to a version that contains the fix.
If you have a lot of affected controllers under an Operations Center, you can run the Groovy script using a cluster operation and pass the Java startup argument at Controller Provisioning, so that also new controllers will get it.
How to import the new certificate
If it does not exist yet, create a directory named update-center-rootCAs in your controller’s Jenkins Home. Copy the following certificate, cloudbees-root-cacerts.pem, inside that folder:
-----BEGIN CERTIFICATE----- MIIFhDCCA2wCCQDGSFE7A358zjANBgkqhkiG9w0BAQsFADCBgzELMAkGA1UEBhMC VVMxCzAJBgNVBAgMAkRFMRgwFgYDVQQKDA9DbG91ZEJlZXMsIEluYy4xFjAUBgNV BAMMDXVwZGF0ZS1jZW50ZXIxNTAzBgkqhkiG9w0BCQEWJm9wZXJhdGlvbnMrdXBk YXRlLWNlbnRlckBjbG91ZGJlZXMuY29tMB4XDTIwMDUyOTAxMjgxNFoXDTMwMDUy NzAxMjgxNFowgYMxCzAJBgNVBAYTAlVTMQswCQYDVQQIDAJERTEYMBYGA1UECgwP Q2xvdWRCZWVzLCBJbmMuMRYwFAYDVQQDDA11cGRhdGUtY2VudGVyMTUwMwYJKoZI hvcNAQkBFiZvcGVyYXRpb25zK3VwZGF0ZS1jZW50ZXJAY2xvdWRiZWVzLmNvbTCC AiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAJyeG1X+jhC6NdNTyYRP0iPB F8j1gt9BGsGfTktdwpHpHSfHWwn2S3SAkAGVpck6kOWudejHvKmaAHMEiON0T4RH LnOc0BRd5W/BOzyVgB0eytkjSANeB9UIRNuCZoUM8NdNCyAcr9fmsns6jVRzCwnu yxeXFvGYgikzoO/ZC0/vsyAHp/2AzvgTE/7tFuJYHuvQ8ACfSPRgSQ3rc0hpSnSV V1UqTwrE/1AIhEjisNRXc6eMxlStFIsVuRkdaJRr7pi6W0mFmQr2gFtDHJkqX2nw HqNPzuJ7AVF2VXlh4j7GecDxwVdtVKdQEuCxn7IbX8UbWLcA/IwBnR8ZaHUr1KER +LjTIjwXlQnv3wAoz3YqCvgvKlx1HVTtf/PVlJG0STiPHZtwSqJpgXjQ+XLXCW1g sevDR2fyyddxC5p21AvQ480SGY1cRuesTEpoZjTYW4jNJsb8JKhyyAM50GHYWIgC yCavgHH+da+J7kgSqVmBIgum9Ws4Mh6AQHTUcxozff3vIUnRU8B5Lg20q4UZqDrF HKxQMyvEFXBmGIsqw6EtPTKzPWIq/noq2YT4mrpi1iFDPd8phHuy7IIDqmHPP0Gv cL9f/QUDysmVgOuOQShtFhA5ZX2KHJ4sjtPDzYq/EjStI+tytR10aV12a/iL4eBf NlhP0UiPVhw2hLg3xMLBAgMBAAEwDQYJKoZIhvcNAQELBQADggIBAHGSLYRRZ032 pmbwHY8yg9+z7P2TljaYA4dI5/WUmev0oNyEwEwcbMhhLq1yIG9bDjo65WFYyNij X7eJHGSTR2clRLRZ67N2z4hOkymgLbpXgCoyAr7Pgkl2sxz3lW/VPTN7ZFl37Zkb sUuSFy5BnNXkISh5bDATX9JCJCPYzdVKBbjd2kyMeiOz7Gf/SYOEBvp/vgz3gqv5 ZLQIEKFmZT2imiELmfgO0uuVlCgJWU9PDGEb2MW4Td0v0hzL5aycYQSl0bAbiTSq ofSIOUdniELYJEtn0G/tdxY5ZnlgEP8jdSNlsnESArjyxGJanwxzQdMps6MaTxew +tYPzjMACEQaLeNUHmLtlMRFaqWPcOj85XZ3qzBwwOESFq3NQu8NZcOJrNr84AHF kPnE90gSNaZlA2XJReioGViBmo421LypKobjbny0z2L2jvQ7lI23Hdt4DA34cB6d lPg/6Vi9PyhokeNTL5VZCGpU8WzhMoxq/4pNLawq2suE92OeYuWDz2v65OJWJe1E EXQhX5H8G1001pv2OD+p5xew/QfDxshCsi3hPVRSB1qVquMgmhOBCnq1j/ocGOub LKQ0WpeSUYDynVrfpvQ1rCW+Sbz0fEduMPrD8c+2+v/U6NFDxqZCtooRbtNQeKuy JYtKoB6VuUAWHOqi95lCirlplY2Mjljn -----END CERTIFICATE-----
If you have a lot of affected controllers under an Operations Center, you can run a Groovy script that automatically creates the certificate in the controller’s Jenkins Home using a cluster operation.