CloudBees CD provides a comprehensive access control mechanism to control how individuals use the system. For a general discussion of access control in CloudBees CD, see Configuring Access Control .
-
Users must log in to view information or perform operations.
-
After you log in, system access is limited based on:
-
User name.
-
Groups to which that user belongs.
-
Permissions specified for various CloudBees CD objects.
-
While configuring access control is primarily an admin function, individual end users may want to view their direct and inherited privileges for specific objects and change permissions on selected objects.
For many CloudBees CD objects, access control is configured from the object’s editor view via the Access Control selection on the Object Menu. Selecting Access Control opens the Access Control dialog.
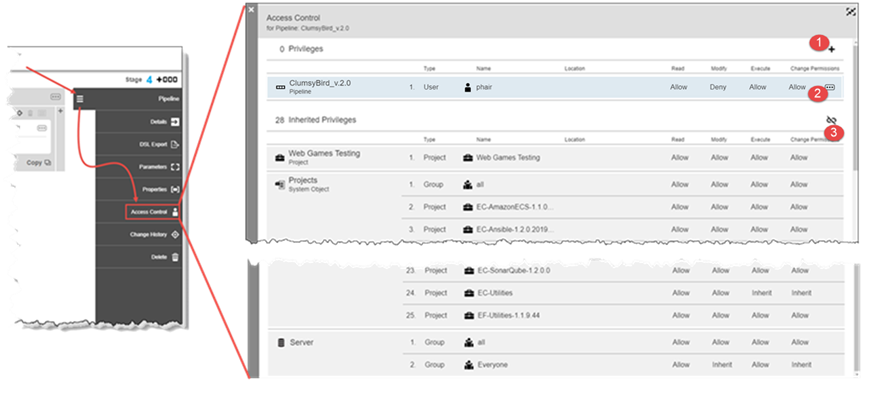
where:
| 1 | Add Privilege button—Opens the add privilege dialog. From here you can add a new privilege. See Privileges for further information. |
|---|---|
2 |
Edit/Delete button—Use to open the privilege editor or to delete the privilege. |
3 |
Break Inheritance button—Use to break the link to inherited privileges. See Inheritance for further information. |
This access control interface is available to these objects:
Release |
Sub Release |
Pipeline |
Stage |
Task |
Gate Rule |
Application |
Application Tier |
Application Microservice |
Containers |
Components |
Processes |
Application Process Steps |
Component Processes |
Component Process Steps |
Microservices |
Microservice Processes |
Microservice Process Steps |
Environments |
Environment Tiers |
Environment Templates |
Environment Template Tiers |
Resource Templates |
Dashboards |
Reports |
Catalogs |
Personas |
Service Accounts |
Archive |