CloudBees Unify integrates third-party security tools, such as SAST or DAST scanners, for use in implicit security assessments. These tools are activated and reviewed from the Marketplace.
The Marketplace can be accessed at organization level, or at component level. Enable or disable tools at organization level, and review the status of each tool at component level.
To access the Marketplace:
-
Select an organization. Optionally, select a component.
-
Select .

-
Select to filter tools by Category, Tags, or Tooling, or clear all filters.
-
Search for a security tool, or filter by activated or available tools.
-
Select to enable or disable implicit security assessment. Implicit security assessment can be enabled or disabled at both tenant and sub-organization level.
Disabling implicit security assessment turns off automatic security analysis for all the components associated with the selected organization and its sub-organizations. For further details, refer to Organization hierarchy, and override records.
-
Select to toggle security tools:
-
For the tenant organization, select to activate or deactivate security tools for all child organizations. Only tools that have been activated at the tenant organization level can be enabled for sub-organizations.
-
For sub-organizations, select to enable or disable security tools for that organization only. Re-enabling a disabled tool for a sub-organization restores any previous configuration of that tool.
Only users with the Admin user role in the organization can enable or disable security tools.
-
-
Select Configure to configure a security tool. This option is only available for certain tools that require configuration, such as Black Duck SCA or Coverity on Polaris.
Any user can view the configuration of a security tool, but only users with the Admin user role in the organization can configure them.
Organization hierarchy, and override records
Enabling or disabling a security tool, or implicit security assessment, is done at the organization level. Changes made to the tenant organization affect all of its child organizations. Below tenant-organization level, changes made to an organization create an override record, such that changes to its parent do not affect that organization.
For example, in the image below, enabling a security tool for the tenant organization would enable it for all three child organizations. If you then disabled it for Child organization 1, it would also disable it for Child organization 3.
Activating a different security tool for Child organization 1 would activate it for Child organization 3, unless that tool had already been deactivated for Child organization 3, which would have created an override record.
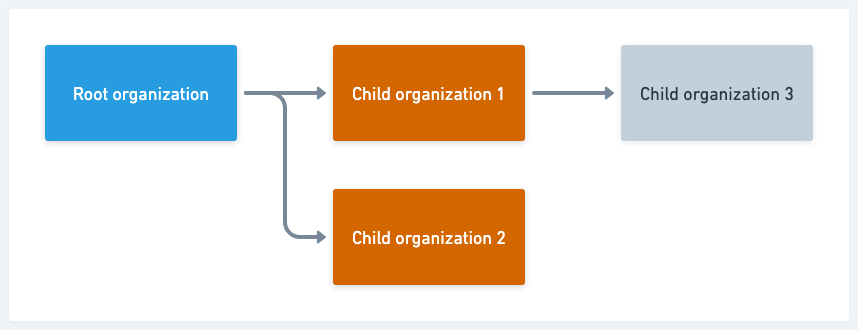
| Deactivating a security tool for the tenant organization disables it for all child organizations, irrespective of override records. |
Configurable tools and inheritance
Certain tools, such as Black Duck SCA, Coverity on Polaris, and SonarQube, must be configured when they are enabled for an organization. When you configure a tool, you are able to specify whether to allow child organizations to inherit that configuration, or require them to be configured separately. This inheritance can be changed at any time.
| Configuration values set within sub-organizations are preserved even if inheritance is disabled and later re-enabled. This ensures that any admin-defined settings at the sub-organization level remain in place until explicitly updated. |
Changing whether child organizations inherit their configuration does not change their configuration in itself. Once inheritance is enabled or disabled, you must update configuration at either the parent level (for inheritance enabled), or the child level (for inheritance disabled), to change the child organization’s configuration.
Configure Perforce Klocwork SAST
Perforce Klocwork SAST must be configured in the Marketplace before it can be used for implicit security analysis. To configure Klocwork SAST:
-
In the Marketplace, select Configure for Klocwork SAST.
-
In the Klocwork SAST Configuration dialog, enter the following details:
-
Select whether to allow child organizations to inherit this configuration.
-
Configuration based on: Select whether to authenticate using credentials, or an application token.
-
Select Enable Klocwork Agent Scan to run a change-only scan with kwciagent. This provides a quick way to confirm that small, recent code changes are clean, as long as a full scan has already been run on the project.
-
Klocwork host URL: The URL of your Klocwork server.
-
Klocwork license server hostname: The hostname of your Klocwork license server.
-
Klocwork license server port: The port number of your Klocwork license server.
-
Klocwork username: The username used to authenticate with the Klocwork server.
-
Klocwork application token or Klocwork password: The application token or password used to authenticate with the Klocwork server.
-
-
Select Save to save the configuration.
Available security tools
The following security tools can currently be configured on the CloudBees Unify:
Code security scanners
|
For Coverity on Polaris, findings redirection to the exact line of code is not supported. CloudBees Unify redirects to the file containing the issue, but does not highlight the line number, because this is not supported by the Coverity tool itself. |
| Security tool | Description | Supported languages | Explicit or implicit | Scan type | Installation type |
|---|---|---|---|---|---|
Black Duck SCA |
Scans open-source dependencies for known vulnerabilities and license risks. |
Explicit |
Code |
Both single and multi tenant |
|
Checkov |
Scans cloud infrastructure configurations, including Terraform and Cloud Formation scripts. |
Implicit |
Code |
Both single and multi tenant |
|
Coverity on Polaris |
Enterprise-grade static analysis for code security and quality. |
Explicit |
Code |
Both single and multi tenant |
|
Gitleaks |
Scans Git repositories for sensitive content, such as credentials. |
N/A (language agnostic) |
Implicit |
Code |
Both single and multi tenant |
Gosec |
An open source Golang security scanner. |
Implicit |
Code |
Both single and multi tenant |
|
Klocwork |
A SAST tool that checks code against secure coding rules to help identify and fix critical vulnerabilities early. |
Implicit |
Code |
Single tenant |
|
Njsscan |
An open source Node.js security scanner. |
Implicit |
Code |
Both single and multi tenant |
|
SCC Scanner |
An application software language analyzer. SCC Scanner is enabled on CloudBees Unify by default. |
Implicit |
Code |
Single-tenant |
|
Synk IaC |
Scans infrastructure-as-code files for security misconfigurations and compliance issues. |
Implicit |
Code |
Both single and multi tenant |
|
Snyk SAST |
Scans source code to identify security weaknesses early in the development process. |
Implicit |
Code |
Both single and multi tenant |
|
SonarQube |
Detects bugs, code smells, and security vulnerabilities across multiple languages. |
|
Explicit |
Code |
Both single and multi tenant |
Binary security scanners
| Security tool | Description | Supported languages | Explicit or implicit | Scan type | Installation type |
|---|---|---|---|---|---|
FindSecBugs |
An open source Java security scanner. Used in CloudBees to scan binary |
Implicit |
Binary |
Both single and multi tenant |
|
Grype |
A vulnerability scanner for container images, SBOMs, and file systems. |
Implicit |
Binary |
Both single and multi tenant |
|
Syft SBOM |
Generates software bills of materials (SBOMs) from containers and binaries. |
Implicit |
Binary |
Both single and multi tenant |
|
Trivy |
A Docker image scanner that supports OS packages and language-specific dependencies. |
Implicit |
Binary |
Both single and multi tenant |