Security Assertion Markup Language (SAML) is a standard for exchanging authentication and authorization data between an identity provider (IdP) and a service provider. SAML is a common single sign-on (SSO) configuration that allows users to sign in to multiple software applications using the same credentials. CloudBees Unify uses the SAML 2.0 protocol to implement SSO.
SAML authentication is initiated from the service provider site. CloudBees Unify integrates with an IdP by linking a CloudBees Unify user with an IdP user. The connection is made using the user’s unique ID (the SAML NameIdFormat), which is required. The default Active Directory setting usually does not include NameIdFormat, so you may have to add it manually.
You can enable SSO through Okta by connecting your existing SAML configuration to the Okta tile application. This integration allows users who click CloudBees Unify links to be redirected to CloudBees Unify through Okta for authentication. Refer to Enable Okta SSO for setup instructions.
Perform the following to set up SSO in the CloudBees Unify:
-
Navigate to .
-
Add a domain to CloudBees Unify.
-
Verify domain ownership by adding a platform verification code to your domain name system (DNS).
-
Configure SAML to connect your IdP.
-
Enable SAML to manage SAML connections.
|
You must have the Admin role to configure, update, and manage the SAML connection. Use role-based access control to fine-tune who can perform each SSO setup task. |
Add a domain
Add a domain to be used for SSO. The domain name must be available (not currently listed in ).
To add an available domain name to CloudBees Unify:
-
Select to the left of your account name.
-
Select Create SAML.
-
Enter a Domain name; for a user with the email
user@example.com, the domain name isexample.com. -
The domain name is checked for availability. A green checkmark indicates the name is available.
-
Select Next to display the verification code.
The domain is listed in with an Unverified status. You are ready to verify domain ownership.
|
Return later to verify domain ownership, if desired.
|
Verify domain ownership
To prevent unauthorized use of your domain, confirm ownership by adding the displayed verification code to the DNS records for your domain.
To verify domain ownership:
-
Sign in to your domain registrar’s website and locate the section for managing DNS records.
-
Create a new record, formatted as a TXT file, in your DNS.
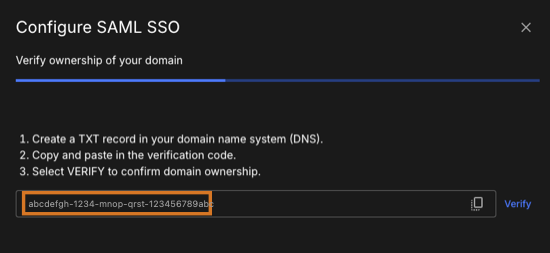 Figure 1. An example verification code for the DNS is highlighted.
Figure 1. An example verification code for the DNS is highlighted. -
(Optional) If the verification code, as in the example above, is not displayed in CloudBees Unify, do the following:
-
Go to and select
 next to your unverified domain.
next to your unverified domain. -
Select Verify domain to display the verification code.
-
-
Copy the verification code from CloudBees Unify and paste it into the DNS TXT file.
-
Save the updated TXT file.
-
Select Verify.
-
It may take some time for the changes to propagate across the DNS provider. Check the propagation progress at dnschecker.org.
-
The TXT record with the verification code must exist within your DNS for the verification to be successful.
-
If the domain verification is successful, the Domain status is listed as Verified in , and you are ready to configure a SAML connection.
|
Return later to configure SAML, if desired.
|
Configure SAML
CloudBees Unify SSO uses SAML to provide a streamlined user experience. Use a verified domain name to set up a SAML connection.
| Each verified domain can only accommodate a single SAML connection with a given IdP. To create multiple SAML connections, you must either use multiple domains or multiple IdPs. |
To configure a SAML SSO connection:
-
Go to and select a verified domain.
-
Select
 next to your unverified domain, and then select Link connection.
next to your unverified domain, and then select Link connection. -
Select an existing connection from the options, or select Create new to create a new one.
If you select an existing SSO connection, you overwrite all existing XML information. -
Enter a Connection name.
-
Locate the metadata XML from your IdP.
-
Use one of the following methods to enter the metadata XML:
-
Select Import metadata XML file, and then upload your XML file.
-
Paste the XML from your IdP into Metadata XML.
-
Enter the Entity ID, the Sign-on URL, and the Signing certificate.
-
-
Select NEXT. CloudBees Unify generates the XML information.
-
Perform one of the following:
-
Select Download XML to download the generated XML file to add to your IdP.
-
Copy the generated XML information and paste it into your IdP.
Refer to instructions specific to your IdP for more information.
-
-
Verify that your configuration fulfills the requirements checklist.
-
Select Close.
The SAML connection for your domain is configured accordingly. You are ready to enable your SAML connection.
Configuration requirements checklist
Confirm that you have configured SAML correctly in CloudBees Unify to enable enhanced security.
The following are required to ensure security via a correctly configured connection:
| Requirement details | |
|---|---|
|
Your IdP uses HTTP POST binding. |
|
Your IdP signs SAML responses using a private key that matches the signing certificate provided to CloudBees during the SAML connection step. |
|
Your IdP encrypts the SAML responses via the RSA-OAEP algorithm, and uses the public certificate provided by the CloudBees Unify.[1] |
|
Your SAML responses have the |
|
Your SAML responses include valid values for both of the SAML attributes |
|
Your IdP should set the format of the NameID attribute as |
[1]The CloudBees Unify provides the service provider metadata, which contains the CloudBees Unify public certificate, during the final SAML creation step.
| If settings for your organization or IdP do not allow you to configure SAML according to the checklist above, contact CloudBees Support for assistance with a custom configuration. For example, when using Microsoft Entra ID, SAML token encryption is available only in specific Microsoft Entra editions. |
After confirming that your SAML connection is set up with all of the above requirements, you are ready to enable your SAML connection.
Enable and manage the SAML connection
Manage your SAML connections in .
Enable your SAML connection by setting the Enabled toggle to On (![]() ).
You may additionally set Strict mode or Auto-provisioned to be On if desired.
).
You may additionally set Strict mode or Auto-provisioned to be On if desired.
|
Enabled must be set to On ( |
| Connection | Definition |
|---|---|
Strict mode |
Set Strict mode to On to disable the invite function, so all users to your domain must sign in to the tenant organization via SAML. All users in your tenant must be from that domain. |
Auto-provisioned |
Set Auto-provisioned to On to enable the invite function. New users who log in with an email containing the approved domain are automatically added to your tenant. If disabled, new users must first be manually invited to your tenant. |
Enabled |
Set Enabled to On to enable SAML, allowing users to sign in to your tenant using SAML. If disabled, users must sign in how they originally signed in to CloudBees Unify. |
Enable Okta SSO
You can enable SS through Okta by connecting your existing SAML configuration to the Okta tile application. This integration allows users who select CloudBees links to be redirected to CloudBees Unify through Okta for authentication.
When enabling Okta SSO, keep the following in mind:
-
Your existing SAML configuration process is the same regardless of this integration.
-
Updating the Service provider assertion consumer service (ACS) URL enables Okta tile functionality.
-
You may notice a brief authentication redirect (about half a second) during sign in. This is expected behavior when Okta SSO is enabled.
Set up Okta SSO for new customers
If you are setting up SSO for the first time and plan to use the Okta tile:
-
Follow the standard steps to Configure SAML in CloudBees Unify.
-
After completing the setup, select
 . Then select View on your new SAML connection to open the SAML summary page.
. Then select View on your new SAML connection to open the SAML summary page. -
Copy the Service provider assertion consumer service URL.
-
Follow Okta’s documentation for creating a custom app integration: Create SAML custom app integrations | Okta Classic Engine.
-
When configuring the app in Okta, paste the copied URL into the Single sign-on URL field. Refer to Okta SAML reference for details on where this field appears.
-
Complete the setup in Okta.
Set up Okta SSO for existing SAML customers
If you already use SAML and want to enable Okta SSO:
-
In CloudBees Unify, select
 . Then select View on your existing SAML connection to open the SAML summary page.
. Then select View on your existing SAML connection to open the SAML summary page. -
Copy the Service provider assertion consumer service URL.
-
Follow Okta’s documentation for creating a SAML custom app integration: Create SAML custom app integrations | Okta Classic Engine.
-
When configuring the app in Okta, paste the copied URL into the Single sign-on URL field. Refer to Okta SAML reference for details on where this field appears.
-
Complete the setup in Okta.
| Existing SAML customers will continue to authenticate normally. Updating the ACS URL is optional but required to enable the Okta tile redirect. |
|
Administrators can select |
Update a SAML configuration
You can change your SAML settings if you are an organization administrator.
To update the SAML configuration:
-
Select at the top of the screen by your username.
-
Select Connections.
-
Select
 next to the connection you want to update.
next to the connection you want to update. -
Select Edit, and make the desired updates.
-
Select Next.
-
Select Save.
The SAML configuration is updated accordingly.
Remove a SAML connection
You can remove a SAML connection for your tenant organization. A removed SAML connection is completely and irreversibly removed from the CloudBees Unify.
To remove a SAML connection:
-
Select at the top of the screen by your username.
-
Select Connections.
-
Select
 next to the connection you want to remove.
next to the connection you want to remove. -
Select Remove.
-
Select Next.
-
Select Save.
The selected SAML connection is removed from CloudBees Unify.