The security overview dashboard provides application owners and security leaders with a continuous view of the latest security metrics. It can be used for reporting and review purposes, and greatly helps continuous security-posture management.
Use the security overview to review both component and application security. For the component security overview, a selected component and code branch supply the data for the analysis. For the application security overview, the asset profile and environment of deployed assets provide the data.
|
To access the component Security overview:
-
Select an organization.
-
Select Components, then select a component.
-
Select Security overview.
To access the application security overview dashboard:
-
Select an organization.
-
Select Applications, then select an application.
-
Select Security overview.
-
Filter results by:
-
Severity: The risk rating as determined by the plugin that found the issue. Severity can be very high, high, medium, or low.
-
SLA status: Results that have breached or are within your service level agreement (SLA).
-
Tools: Results reported by a specific security tool or tools.
-
-
For components: select a branch for the component from the dropdown menu.
For applications: select or search for an environment.
-
Filter results by Severity: The risk rating as determined by the plugin that found the issue. Severity can be very high, high, medium, or low.
-
Review the date and time when the organization or component was last scanned.
Currently, the last scanned date only appears on the component security overview, and not the application security overview.
Vulnerability findings remediation trend
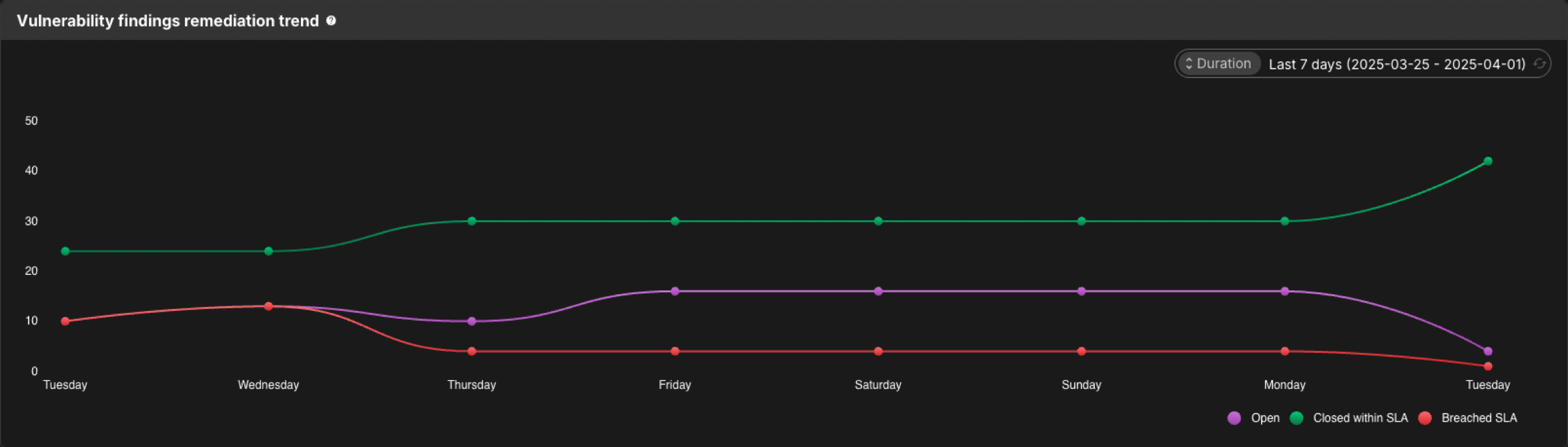
The Vulnerability findings remediation trend depicts newly identified findings, and changes in vulnerability remediation over time. This visualization provides insight into your development team’s efficacy in responding to identified findings.
Hover over a point in time on the graph to display the number of findings at that time that are open, have breached SLA, or are closed within the SLA.
Select Duration to display findings from the last 7 days, 30 days, or year.
| Currently, the New findings data is only displayed on the application security overview, and not on the component security overview. |
Open findings by severity
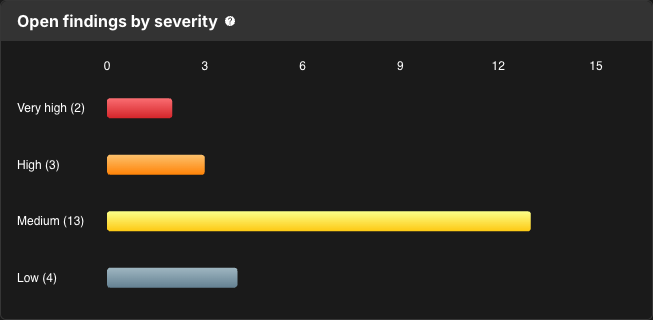
Open findings by severity depicts the number of findings sorted by severity. Severity in CloudBees Unify means the risk rating as determined by the plugin that discovered the security issue.
Select a bar in the graph to navigate to the Component security center, with findings filtered by that severity, along with any other filters applied on the security overview dashboard.
Components with most open findings
| This feature is only available on the application security overview dashboard |
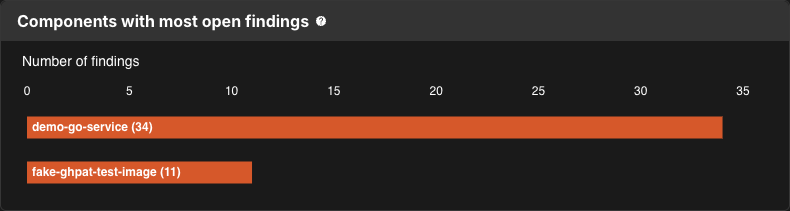
Components with most open findings ranks the components with the most open findings, helping you to prioritise your remediation efforts.
Risk accepted and false positive findings
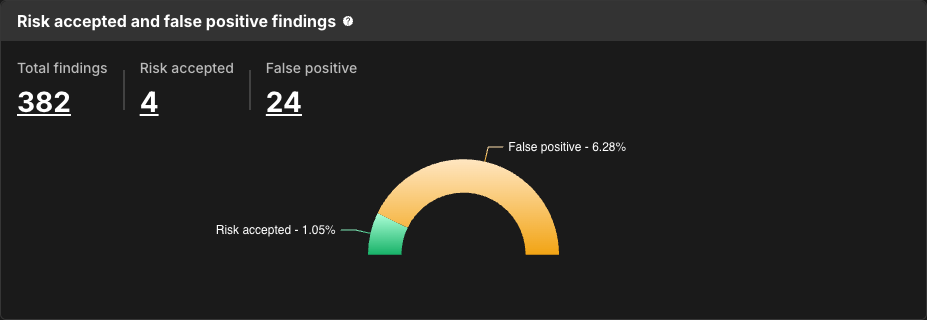
Risk accepted and false positive findings displays the proportion of total findings whose status has been marked as false positive, or reviewed as risk accepted.
Select a number of findings, or a section of the bar, to navigate to the Component security center with findings filtered by that status.
SLA breaches by severity
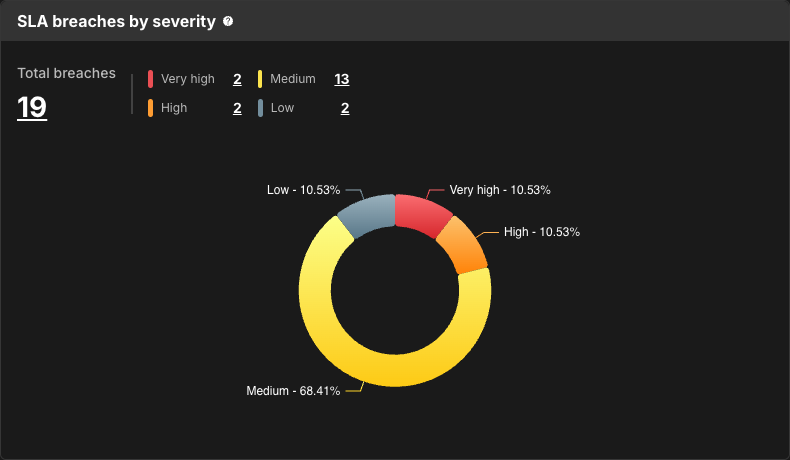
SLA breaches by severity displays the proportion of SLA breaches by the severity of the finding.
Select the number of findings, or a section of the circle, to navigate to the Component security center with findings filtered by SLA breaches of that severity.
Findings identified
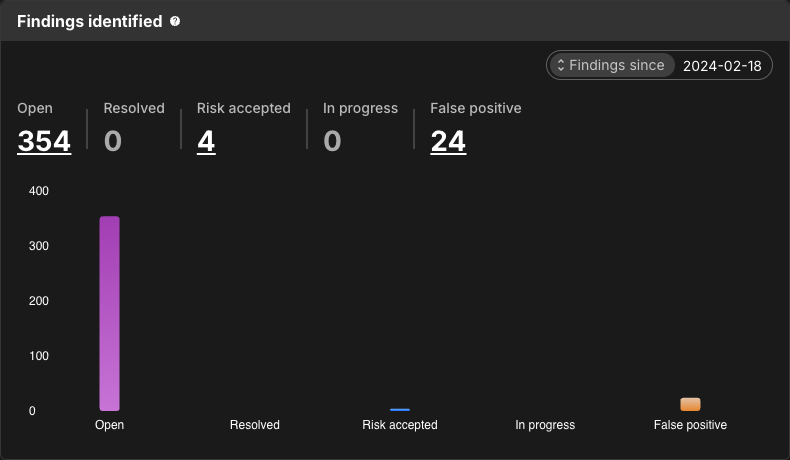
Findings identified visualizes the number of findings by their status.
Select Findings since in the upper right to filter by findings since the selected date.
Select a bar, or the number of findings, to navigate to the Component security center with findings filtered by that status.
Findings by review status
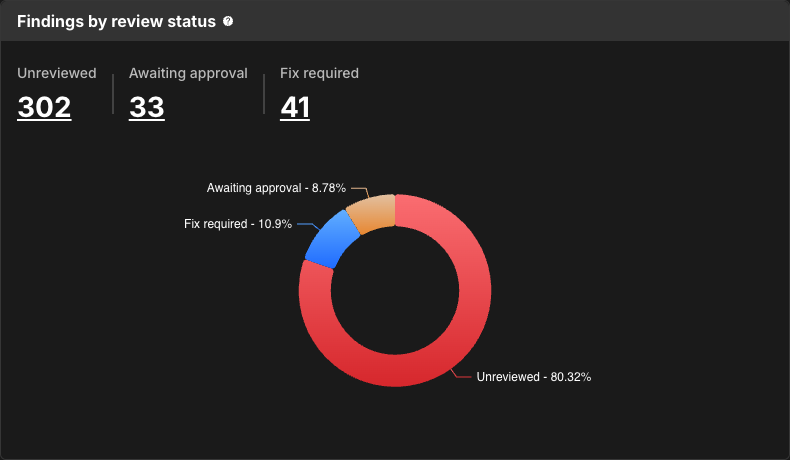
Findings by review status displays the proportion of findings of each review status: unreviewed, awaiting approval, or fix required.
Select a number, or a section of the circle, to navigate to the Component security center with findings filtered by that review status.
Open findings by SLA status
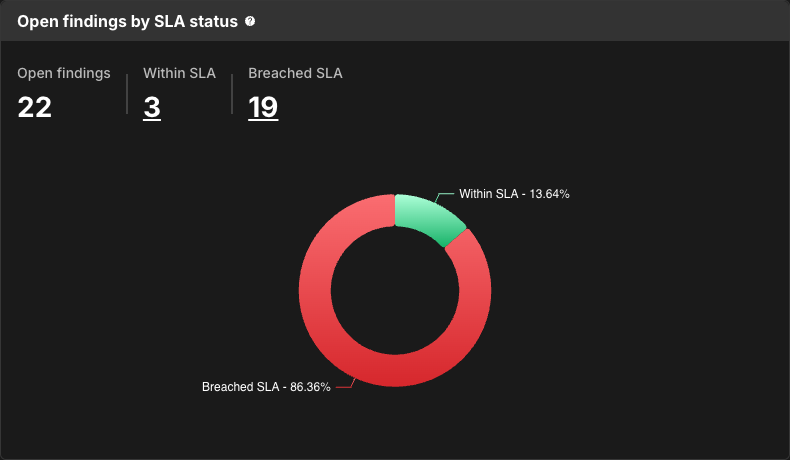
Open findings by SLA status displays the proportion of open findings that are within or have breached your SLA.
Select a number of findings, or a section of the circle, to navigate to the Component security center with findings filtered by that SLA status.
Open findings by security tool
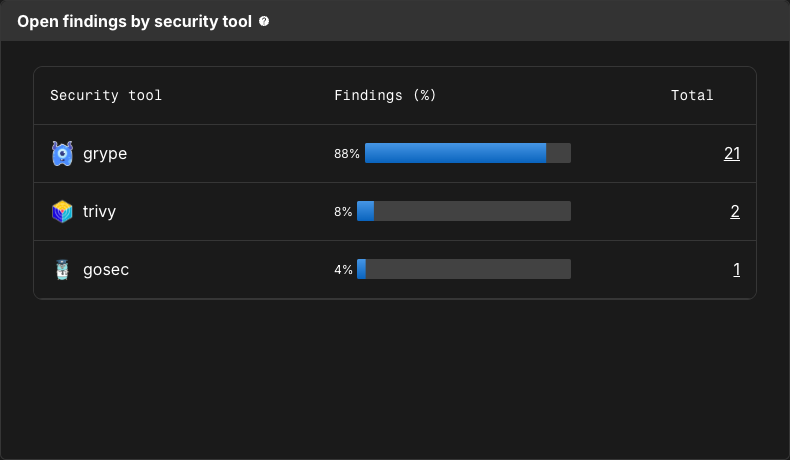
Open findings by security tool displays the number and proportion of security findings discovered by each configured security tool.
Select a number of findings to navigate to the Component security center with findings filtered by that security tool.
Open findings distribution by security tool
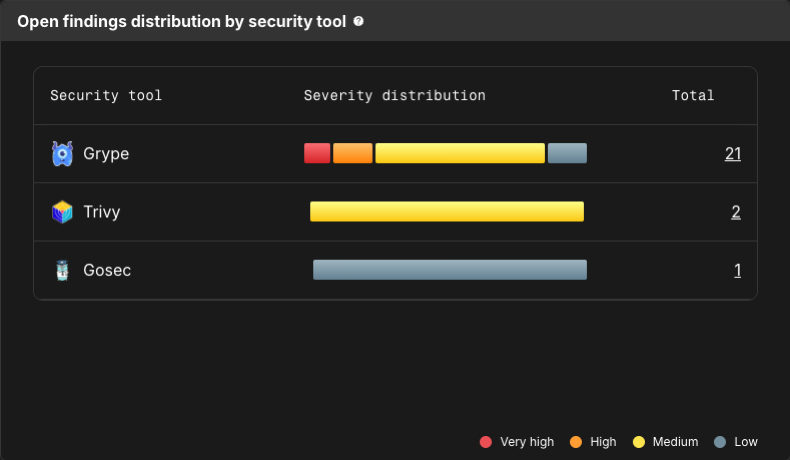
Open findings distribution by security tool displays the severity distribution of security findings discovered by each configured security tool. Each severity is represented by a color:
-
Very high: Red.
-
High: Orange.
-
Medium: Yellow.
-
Low: Grey.
Hover over a bar to display the number of findings of each severity for that tool. Select a section of the bar, or a number of findings, to navigate to the Component security center with findings filtered by that severity and security tool.
Open findings distribution by category
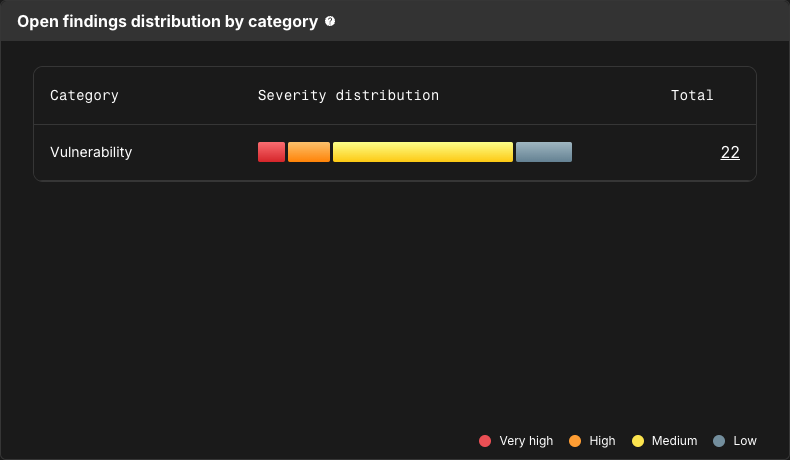
Open findings distribution by category displays the severity distribution of security findings for each category of issue, such as vulnerabilities, operational risks, or secret violations. Each severity is represented by a color:
-
Very high: Red.
-
High: Orange.
-
Medium: Yellow.
-
Low: Grey.
Hover over a bar to display the number of findings of each severity for that category. Select a section of the bar, or a number of findings, to navigate to the Component security center with findings filtered by that severity and category.
SLA breaches by asset type
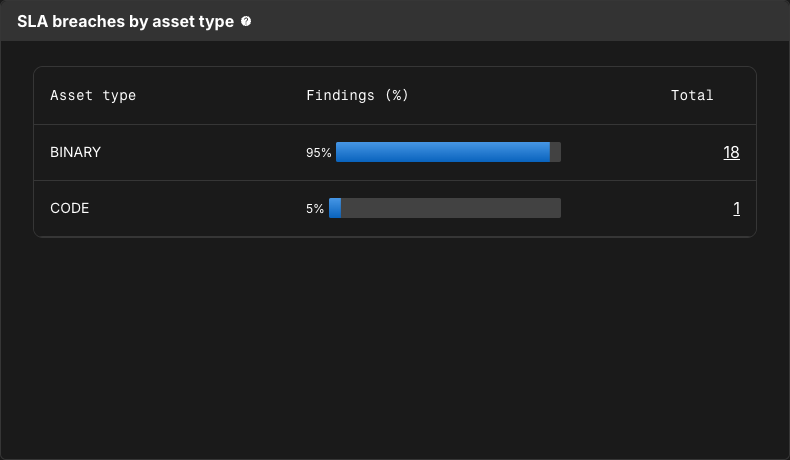
SLA breaches by asset type displays the proportion of findings that have breached SLA by asset type.
Select a number of findings to navigate to the Component security center with findings filtered by those within that asset type that have breached SLA.