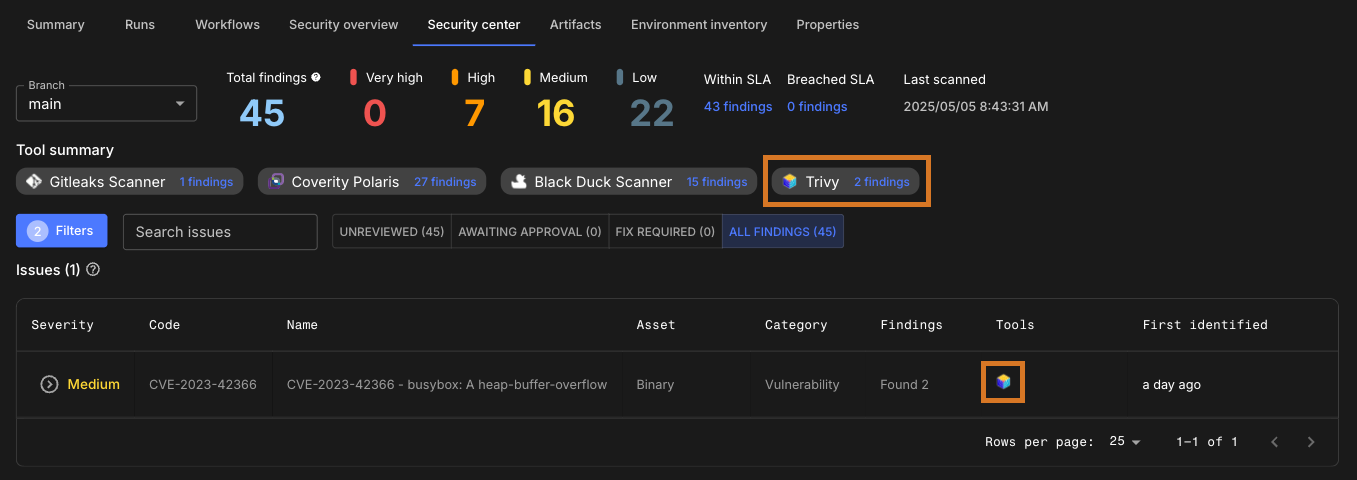
Use this action to perform static application security testing (SAST) on a binary TAR file with the Trivy scanner, and then view comprehensive security results in CloudBees Unify.
This action is available on the GitHub marketplace.
Prerequisites
Set up CloudBees Unify and GHA to work together, providing key features of CloudBees Unify to GHA workflows. Refer to Getting started for more information.
Inputs
| Input name | Data type | Required? | Description | ||
|---|---|---|---|---|---|
|
String |
Yes |
The path of the binary to be scanned.
|
||
|
String |
No |
The CloudBees Unify URL.
The default value is |
||
|
Boolean |
No |
The option to perform license scanning.
Specify |
This action uses GitHub OIDC authentication to securely communicate with the CloudBees Unify. Be sure to set permissions to id-token: write in your workflow.
|
Usage examples
Basic example
The following is a basic example of using this action:
permissions: id-token: write contents: read steps: - name: Trivy SAST scan uses: cloudbees-io-gha/trivy-scan-publish@v2 with: binary-tar-path: example-tar-path.tar
Example using license scan
In the following example, the license option is enabled to scan the binary for license files, and then output the risk to CloudBees Unify analytics dashboards. To learn more, refer to the Trivy license scanning documentation.
permissions: id-token: write contents: read steps: - name: Trivy SAST scan uses: cloudbees-io-gha/trivy-scan-publish@v2 with: binary-tar-path: example-tar-path.tar license: true
Full workflow and run example
The following GHA workflow example builds a Docker binary using Buildx, saves the image as a TAR file, and then scans the image with Trivy.
Example GHA workflow YAML file
After the GHA run has completed, the security findings are collected and displayed in the Component security center of the component containing the workflow.