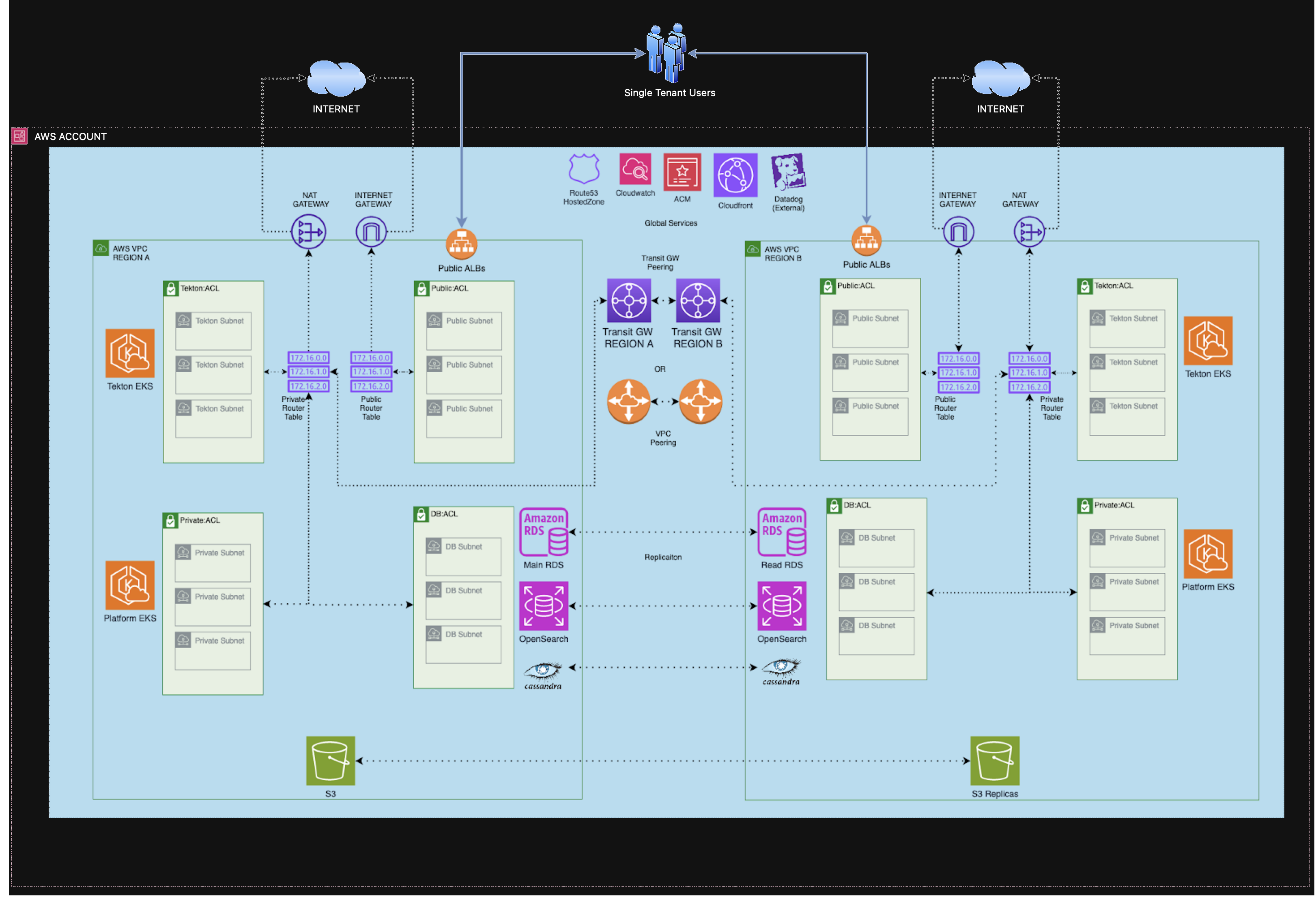
The CloudBees Unify is built using a microservice architecture. Services are containerized and deployed using Helm and Pulumi automation scripts. The infrastructure is deployed in an Amazon Web Services (AWS) region or multi-regions (for users requiring higher availability).
YAML configuration file
Automation scripts include a YAML configuration file that defines:
-
Regions / Availability zones
-
Access control list rules
-
Security groups
-
Resources
-
Relational database service (RDS)
-
OpenSearch
-
Amazon Elastic Kubernetes Service (EKS) clusters
-
Two clusters per region are expected — one for Tekton and one for platform services.
-
Clusters are configurable.
-
-
Virtual private cloud (VPC)
-
Subnets
-
Route 53 Domain name system (DNS)
-
S3 object storage
-
Hosted zone for specific domain routing
-
Certificate manager
-
CloudFront content delivery network (CDN)
-
Datadog monitoring
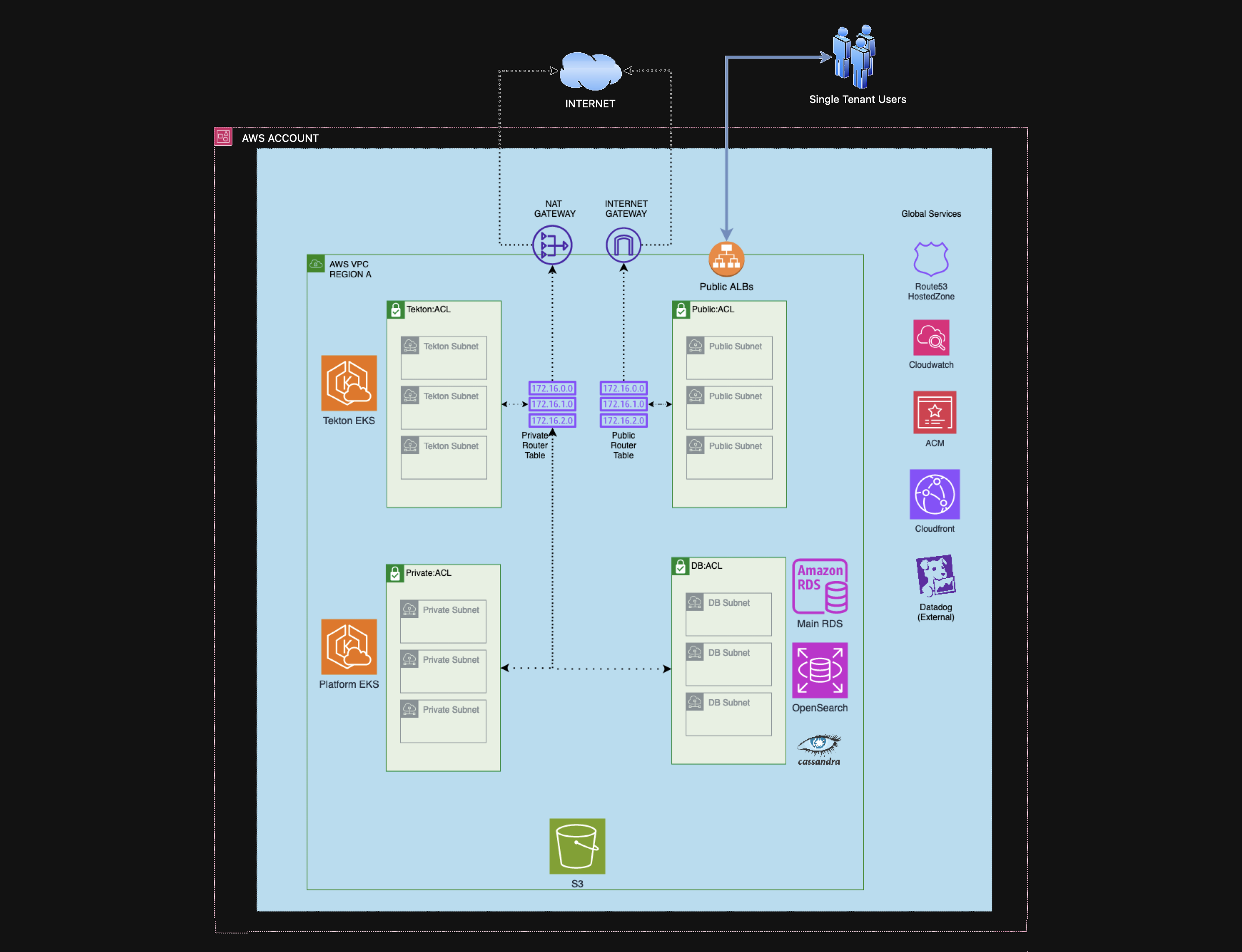
Standard single region
The AWS EKS clusters are configurable, although two deployed per region is standard. One cluster is generally used to host most services required to run CloudBees Unify. The other cluster hosts Tekton itself, platform-specific services for managing Tekton, and it is also where customer workflows run.
Standard multi-region
The multi-region deployment for higher availability users has replication among regions. S3 data, and RDS, OpenSearch, and Cassandra databases are replicated. Using DNS traffic distribution, users can access CloudBees Unify interface that runs in the region closest to them. Workloads are distributed between regions when they are run.