The application security center dashboard provides a centralized location to review security issues and findings across all assets deployed within an application environment, along with their severity ratings. It grants application owners visibility into the run-time security posture of their applications. It helps you review issues, prioritize them, and track remediation efforts, giving you the necessary context to support informed, risk-based decisions before every release.
Unlike the component security center which focuses on individual components, the application security center aggregates security data from multiple assets deployed through your application workflows, and displays comprehensive results with rich contextual information, such as asset deployment details, security tool outputs, and remediation guidance. It integrates findings from both implicit security scans triggered by deployments and explicit security analyses configured in your workflows.
On CloudBees Unify:
-
Issues are security issues reported by security tools.
-
Findings are individual occurrences of a security issue reported in a branch, file, or code location.
-
Severity is the rating reported by the security tool that discovered the finding.
Use the security center
| The security center is only displayed in the navigation once an application has been selected. |
To access the security center:
-
Select an organization.
-
Select Applications, then select an application.
-
Select Security center.
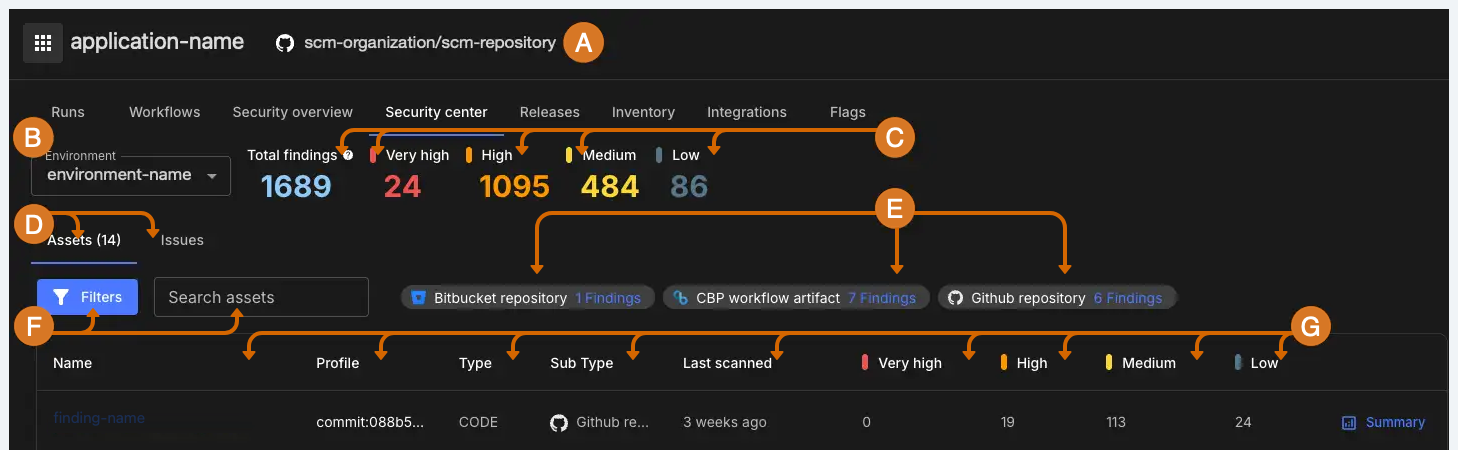
-
The application deployment workflow repository that creates and runs application level workflows. Select the GitHub organization or repository name to navigate to the repository in GitHub.
-
Select an environment configured for the application.
-
Review the total number of open findings across the assets deployed in this application, and the number of findings by each severity.
-
Select to review assets or issues.
-
Review the total number of findings, grouped by asset subtype. For example, GitHub repository, Bitbucket repository, or binary artifact. Select the number of findings for an asset subtype to filter issues by that subtype.
-
Filter issues by asset or subtype, or search for an asset by name, profile, or subtype. Filtering is dynamic, with available filters depending on results.
-
Review finding information:
-
Name: The deployed asset’s name. Select the name to review detailed information for each security issue for that asset.
-
Profile name: The latest commit ID for code assets, or the latest image and version of the deployed binary asset.
-
Type: The asset type, either code or binary.
-
Sub type: The subtype of asset, such as GitHub or Bitbucket repository for code asset types, or CloudBees Unify workflow artifact for binary asset types.
-
Last scanned: The last time the asset was scanned.
-
The number of findings, grouped by the severity rating reported by the security tool that discovered the finding.
-
Security issue details
The issue-centric view provides a consolidated list of all security issues across the application, showing which assets are impacted by each issue. This view helps developers and security engineers focus on specific issues and trace them down to affected components.
To access the issue-centric view, from the application Security center, select the Issues tab.
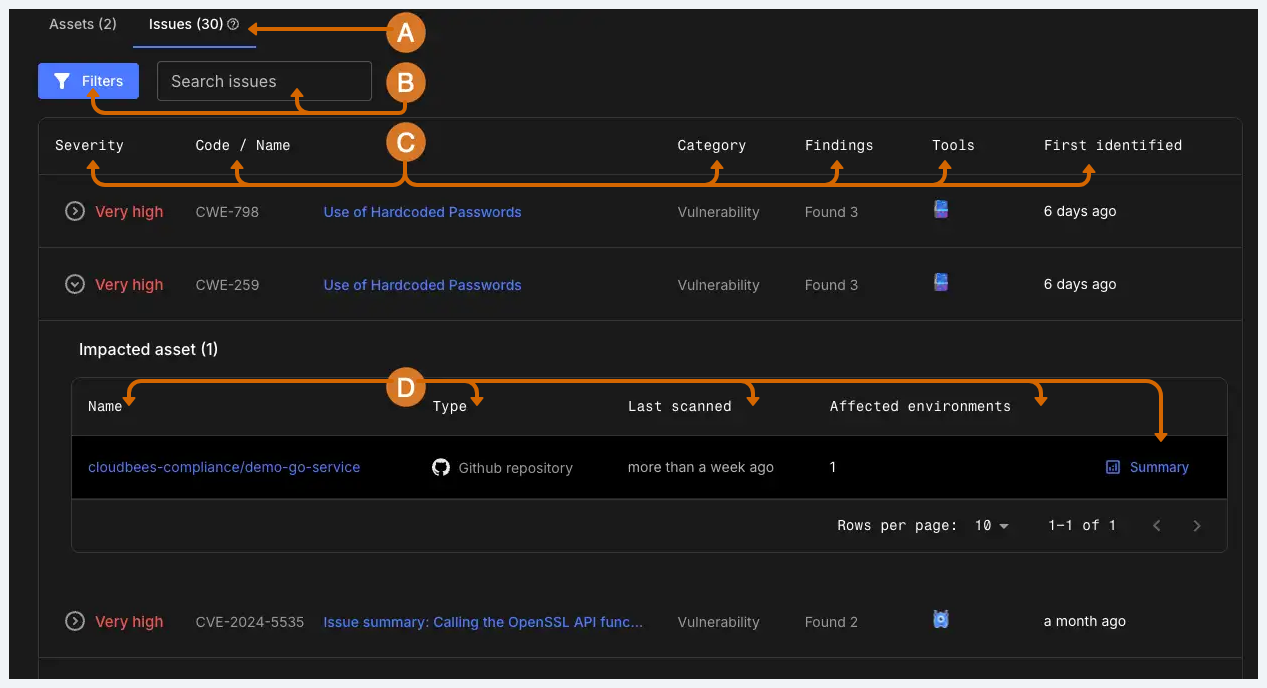
-
Select the Issues tab to review all security issues across the application.
-
Search for an issue, or Filter by:
-
The asset type, either binary or code.
-
The category of finding. One or more of:
-
Configuration.
-
License violation.
-
Operational risk.
-
Penetration testing outcome.
-
Policy violation.
-
SCA.
-
Secret violation.
-
Threat modelling outcome.
-
Vulnerability.
-
-
The date range, or end date, of Risk Accepted findings expiry.
-
The severity rating reported by the security tool that discovered the finding.
-
The SLA status of the finding, either within or breached SLA.
-
The status of the finding (For further information on status, refer to Triage findings):
-
Open
-
In progress
-
Resolved
-
False positive
-
Risk accepted
-
Closed
-
-
The tool that discovered the finding.
-
The triage status of the finding. One of:
-
Unreviewed
-
Fix Required
-
Risk Accepted
-
False Positive
-
Resolved
-
For further information about triage status, refer to Triage findings.
-
-
Review security issue information:
-
Severity: the severity rating reported by the security tool that discovered the finding. Select to review assets affected by the issue.
-
Code / Name: The vulnerability code, or CVE/CWE number of the issue, and the name of the issue.
-
Category: The category of finding. For example, operational risk, or vulnerability.
-
Findings: The number of findings of that issue type that have been identified by security tools.
-
Tools: The security tools that identified the finding.
-
The date the finding was First identified.
-
-
Review detailed information on the assets impacted by the issue:
-
Asset Name: The name of the deployed asset. Select the asset name to navigate to the asset’s detailed security information.
-
Type: The asset type, either code or binary.
-
Last scanned: The last time the asset was scanned.
-
Affected environments: The number of environments affected by the security issue. Hover over the number to review the list of environments.
-
Select Summary to review a summary of all findings for the asset.
-
Detailed asset security information
To access detailed security information for a deployed asset, select the asset name from the asset tab, or from the impacted assets in the issues tab.
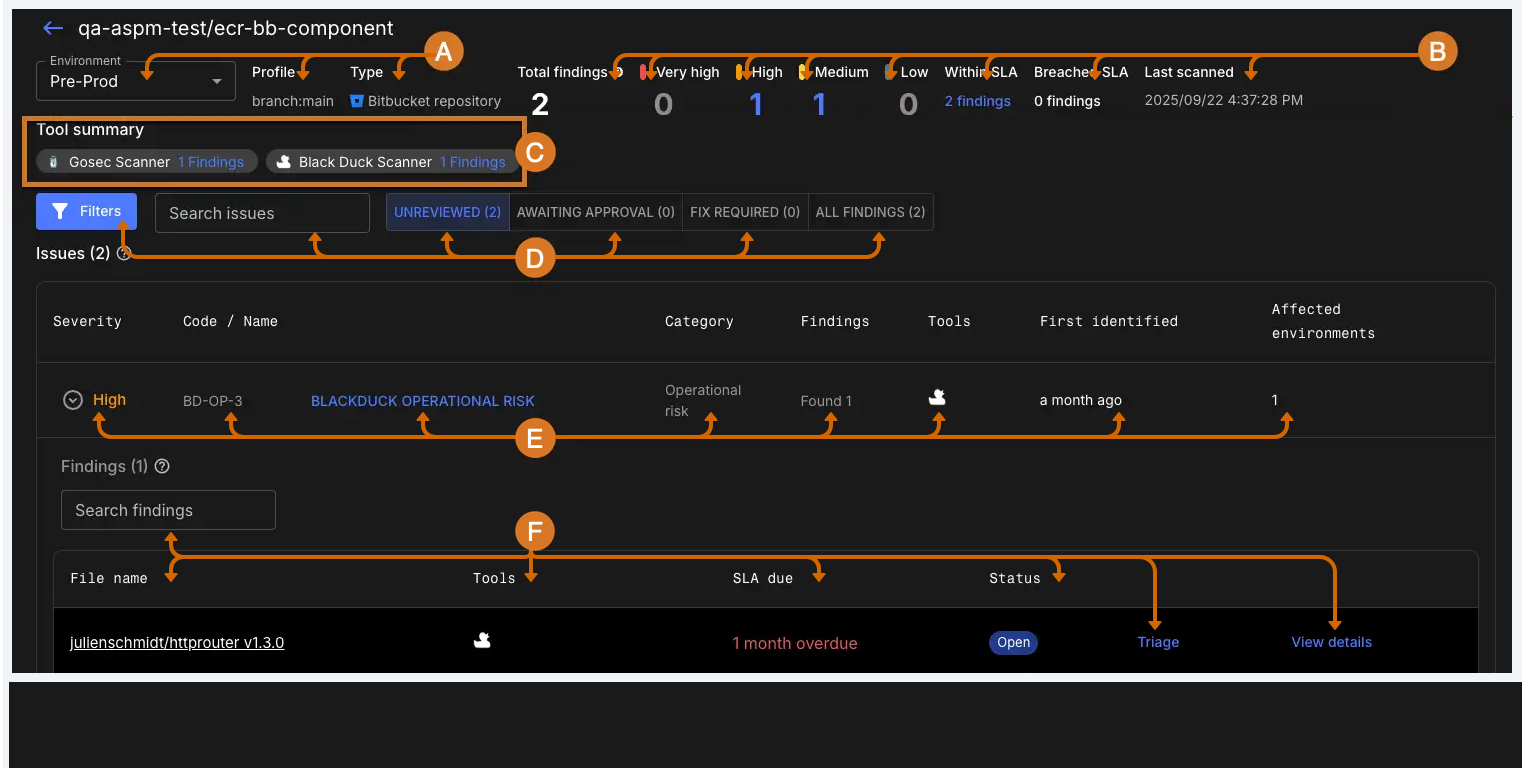
-
Select an environment where the asset is deployed. Review the asset profile and type of asset.
-
Review the total number of findings for the asset, grouped by severity. Select a number of findings to filter issues by that severity, or by findings within or that have breached the SLA.
-
Review the tools that detected findings in the asset, along with the number of findings detected by each tool. Select a tool to filter issues by that tool.
-
Search for an issue, or Filter by:
-
The category of finding. One or more of:
-
Configuration.
-
License violation.
-
Operational risk.
-
Penetration testing outcome.
-
Policy violation.
-
SCA.
-
Secret violation.
-
Threat modelling outcome.
-
Vulnerability.
-
-
The date range, or end date, of Risk Accepted findings expiry.
-
The severity rating reported by the security tool that discovered the finding.
-
The SLA status of the finding, either within or breached SLA.
-
The status of the finding (For further information on status, refer to Triage findings):
-
Open
-
In progress
-
Resolved
-
False positive
-
Risk accepted
-
Closed
-
-
The tool that discovered the finding.
-
-
Review security issue information:
-
Severity: the severity rating reported by the security tool that discovered the finding. Select to review detailed findings for the issue.
-
Code / Name: The vulnerability code, or CVE/CWE number of the issue, and the name of the issue.
-
Category: The category of finding. For example, operational risk, or vulnerability.
-
Findings: The number of findings of that issue type that have been identified by security tools.
-
Tools: The security tools that identified the finding.
-
The date the finding was First identified.
-
The environments where the asset is deployed that are affected by the issue. Hover over the number to review the list of environments.
-
-
Review detailed information on the findings for the issue:
-
File name: The file containing the finding. Select the file name to navigate to the source code management platform, such as GitHub or Bitbucket, to review the finding in context.
-
Tools: The security tool that identified the finding.
-
SLA due date: The date by which the finding should be resolved, based on the SLA defined for the organization.
-
Status: The current status of the finding. For further information on status, refer to Triage findings.
Select Triage to triage the finding.
Select View details to review detailed information about the finding, including the description, remediation guidance, and output from the security tool that discovered the finding.
-
Triage findings
By default, when a security scan detects an issue, a new finding is created in the security center with its status set to Unreviewed. From here, a user with the Admin role, or a custom role with the triage findings permission, should transition its status to Fix Required, at which point it is moved to the Fix Required tab.
During the triage process, a qualified security or DevOps SME is likely to uncover findings that either fall within your tolerance for risk, or are false positives, neither of which require remediation. In the CloudBees Unify, a user with the correct permissions can transition the status of these findings to Risk Accepted if they have decided not to fix the issue, or to False Positive if they believe the security finding is incorrect. Transition all other findings to Fix Required.
Once a finding has been transitioned to Risk Accepted or False Positive, its status won’t be affected by new scans. Resolved findings are automatically updated. Once a developer fixes all the associated findings, the source code management platforms such as GitHub or Bitbucket inform the CloudBees Unify, which initiates a new scan. If the scan doesn’t find any violations, the finding is automatically marked as closed in your collaboration tool, and its status updated to Resolved.
To triage findings:
-
Select an organization.
-
Select Applications, then select an application.
-
Select Security center.
-
Select the asset containing the finding you want to review.
-
For the issue containing the finding you want to review, select to expand the issue.
-
Select Triage.
-
Select one of the following:
-
Fix Required: The finding needs to be fixed.
-
False Positive: The finding is incorrect, or not an actionable issue. Selecting false positive immediately updates the status of the finding, and it appears in dashboards as a false positive finding.
The user can transition the finding back for further triage. An organization owner can also reject the transition to false positive, which reverts the status to Unreviewed.
-
For Justification, enter comments for the organization owner, explaining why the finding is a false positive.
-
-
Risk Accepted: the issue falls within your risk tolerance. Transition to risk accepted requires approval by an organization owner.
-
For Expiry date, select a date for the risk acceptance to expire. Defaults to 90 days.
-
For Justification, enter comments for the organization owner, explaining why the finding falls within risk tolerance.
-
-
-
Select Triage Finding:
-
Fix Required findings are moved to the Fix Required tab.
-
False Positive and Risk Accepted findings are moved to the Awaiting Approval tab, to be reviewed by an organization owner.
-
Approve or deny transitions
Transition requests are approved by users with the Admin role, or another role with the necessary permissions. For further details, refer to Triage permissions.
To approve or deny a transition request:
-
From the Security Center, select the repository containing the finding, then select the Awaiting Approval tab.
-
For the issue containing the asset you want to review, select to expand the issue.
-
Select Review.
-
Select either:
-
Approved
-
Denied
-
-
For approved findings, enter an Expiry Date for the approval.
-
Enter any review comments.
-
Select Submit review:
-
Approved transitions change to the relevant status, false positives indefinitely, and risk accepted findings for the selected timeframe (90 days by default).
For risk accepted findings, the SLA due date is replaced with the risk-acceptance expiry date. Once the expiry date passes and a scan completes, the finding reverts back to unreviewed status, and the SLA due date reverts back to the current SLA setting for the organization. -
Denied transitions have their status changed:
-
Denied false positives to Unreviewed.
-
Denied risk accepted to Fix required.
-
-
Triage permissions
By default, only admins can triage findings, but custom user roles can be created to allow users more granular control of triage.
| Custom permissions assigned to a user belonging to an organization’s system generated teams will not work. Instead, you must assign the user to a custom team. |
The following user role permissions affect triage:
| Role permission | Purpose |
|---|---|
Review risk accepted request |
Review a transition request for a risk accepted finding. |
Review false positive request |
Review a transition request for a false positive finding. |
SLA configuration |
Define the service-level agreement (SLA) for an organization. |
Triage findings |
Triage security findings: transition a finding to fix required, risk accepted, or false positive. |
View findings by triage status |
View security findings in the security center, grouped by triage status. |
For further details on users, roles, and permissions, refer to Role-based access control.