The following use cases demonstrate integrating the GitHub-Checks plugin within CloudBees CD/RO pipelines to perform code linting and displaying the completed run results on your GitHub pull requests (PR). The following pipeline steps are described:
-
Using the Git plugin Clone procedure to clone a GitHub repository into a workspace.
-
Using the SonarQube plugin Run Sonar Scan procedure to scan the cloned repository.
-
Transforming the results of the SonarQube scan into DSL properties using a pipeline Command step.
-
Using the DSL properties within the GitHub-Checks plugin Create or Update Check Runs procedure as annotations
-
Running and viewing the GitHub Check run results within a GitHub PR.
Use case prerequisites
The instructions for use cases assume the following tasks have been completed. If they have not, refer to the references provided before starting.
-
You have completed all required actions described in Configure the GitHub-Checks plugin.
This use case uses a GitHub-Checks plugin-specific webhook trigger to return runtime property values from the GitHub Checks API. If you have not configured one, you can still perform this use case, but ensure you following the alternate instructions for given Input Parameters.
-
You have created plugin configurations for the following plugins:
Use the GitHub-Checks plugin for code linting
This section describes the steps to integrate the GitHub-Checks plugin to publish the result of code linting to a GitHub PR. To get started:
-
In CloudBees CD/RO, navigate to .
-
Select the pipeline you created during Configure the GitHub-Checks plugin.
-
If the pipeline is new, for Stage 1 select the three dot menu and Details.
-
If you configured the GitHub App for a pipeline that already existed and had stages, select Create a new stage, and the Details window automatically opens.
-
-
Name your stage
GitHub Checks code lint, and fill any additional desired fields.
After setting up your pipeline, next add a step using the Git plugin to clone a repository into the workspace.
Clone a repository using the Git plugin
The GitHub-Checks plugin can be used to return results for any GitHub repository configured with your GitHub App integration when performing Install your GitHub App in your repositories.
To clone a repository using the Git plugin:
-
In your CloudBees CD/RO pipeline
GitHub Checks code lintstage, select Add task. -
For the task name, enter
Clone repo. -
Select Define and the Edit Task window opens.
-
For Task type, select Plugin from the dropdown menu.
-
In the Search box, enter
Cloneand select the EC-Git Clone.-
Alternately, from the Plugin dropdown menu, select EC-Git, and then select the plugin .
-
-
Select Input Parameters and provide the parameters for the plugin.
For the Git repository field, your entry must be a GitHub repository where you installed the GitHub App during Install your GitHub App in your repositories.
-
Once you have provided the Input parameters, select Save changes.
After configuring your pipeline to clone a GitHub repository, you can configure a step to scan it.
Scan repository using the SonarQube plugin
Because of the open nature of the input parameters for the GitHub-Checks plugin, it is versatile and, when correctly configured, can be used with many third-party tools to perform different analysis types. For this code linting task, the plugin will use results from the SonarQube plugin procedure Run Sonar Scan as GitHub Checks API output.annotations.
To use the SonarQube plugin to scan repository:
-
In your CloudBees CD/RO pipeline
GitHub Checks code lintstage, select Add task. -
For the task name, enter
Scan repo. -
Select Define and the Edit Task window opens.
-
For Task type, select Plugin from the dropdown menu.
-
In the Search box, enter
Run Sonar Scanand select the EC-SonarQube.-
Alternately, from the Plugin dropdown menu, select EC-SonarQube, and then select the plugin .
-
-
Select Input Parameters and provide the parameters for the plugin.
-
For the Work directory parameter, ensure you reference an existing directory in the GitHub repository you cloned in Clone a repository using the Git plugin.
-
-
Once you have provided the Input parameters, select Save changes.
After configuring your pipeline to scan the GitHub repository, you can configure a step to transform the results into DSL properties to use as GitHub Checks API output.annotations and output.annotations.annotation_level.
Transform the scan results into DSL properties
Although the GitHub-Checks plugin allows for manual parameter input for GitHub Checks API output.annotations and output.annotations.annotation_level, the most practical method of using it is to pipe DSL properties from the scan step into the GitHub-Checks plugin. This is done using a Command step in your plugin.
To configure a Command step to return DSL properties:
-
In your CloudBees CD/RO pipeline
GitHub Checks code lintstage, select Add task. -
For the task name, enter
Transform scan to DSL. -
Select Define and the Edit Task window opens.
-
For Task type, select Command from the dropdown menu, and the Command input fields appear.
-
For the Command input fields:
-
For Shell, enter
ec-groovy. -
For Command, enter:
import com.electriccloud.client.groovy.ElectricFlow import com.electriccloud.client.groovy.models.* import groovy.json.JsonSlurper import groovy.json.JsonOutput ElectricFlow ef = new ElectricFlow() def result = ef.getProperty(propertyName:'/myPipelineRuntime/issueList')?.property?.value println(result) def json = new JsonSlurper().parseText(result) def annotations = [] def annotate = [:] json.each{ it -> annotate = [path: (String) it.component.split(":")[1], annotation_level: it.severity == 'HIGH' || it.severity == 'MEDIUM' || it.severity == 'BLOCKER' || it.severity == 'MAJOR' || it.severity == 'CRITICAL' ? 'failure' : it.severity == 'MINOR' || it.severity == 'LOW' ? 'warning' : 'notice', message: (String) it.message, start_line: it.startLine, end_line: it.endLine] annotations.add(annotate) } if($[/javascript (getProperty("/myPipelineRuntime/scanIssue") == null) ? "1":"0"]){ ef.setProperty(propertyName:'/myPipelineRuntime/scanIssue', value:JsonOutput.toJson(annotations)) }else{ ef.modifyProperty(propertyName:'/myPipelineRuntime/scanIssue', value:JsonOutput.toJson(annotations)) }This command returns the
$[/myPipelineRuntime/scanIssue]variable, which stores theoutput.annotationsandoutput.annotations.annotation_levelneeded by the GitHub-Checks plugin. If you change the$[/myPipelineRuntime/scanIssue]variable name within this code sample, ensure you use your custom variable name when configuring the GitHub-Checks plugin Annotation field.
-
-
Once you have provided the Input parameters, select Save changes.
Now that you have a Command step to transform the scan results to DSL properties, you can configure the GitHub-Checks plugin to publish any scan issue results to your GitHub PR.
Create a GitHub Check run
Providing code linting with each GitHub commit can help find common issues, enforce coding standards, and help reduce introducing new known issues. The GitHub-Checks plugin provides this capability by publishing code linting results directly to PRs where developers, reviewers, and QE persons can quickly identify and address newly introduced issues.
To use the SonarQube plugin to scan repository:
-
In your CloudBees CD/RO pipeline
GitHub Checks code lintstage, select Add task. -
For the task name, enter
Publish scan. -
Select Define and the Edit Task window opens.
-
For Task type, select Plugin from the dropdown menu.
-
In the Search box, enter
Create or Update Check Runsand select the Github-Checks.-
Alternately, from the Plugin dropdown menu, select Github-Checks, and then select the plugin .
-
-
Select Input Parameters and provide the parameters for the plugin:
Many of the following entries reference DSL properties from the pipeline webhook. You can use these values or your own custom values.
-
For Configuration Name, provide the GitHub-Checks plugin configuration you created as part of Configure the GitHub-Checks plugin.
-
For Commit SHA, enter
$[/myPipelineRuntime/parsedWebhookData/sha].-
If you are not using a GitHub-Checks plugin webhook trigger, you can not use this runtime property. Instead, provide a valid GitHub commit SHA.
-
-
For Repository, enter
$[/myPipelineRuntime/parsedWebhookData/repository].-
If you are not using a GitHub-Checks plugin webhook trigger, you can not use this runtime property. Instead, provide a valid GitHub repository where you installed the GitHub-Checks plugin as a GitHub App.
-
-
For Installation ID, enter
$[/myPipelineRuntime/parsedWebhookData/webhookData/installId].-
If you are not using a GitHub-Checks plugin webhook trigger, you can not use this runtime property. To find your GitHub App
Installation ID, in GitHub, navigate to . For your GitHub App, select Configure, and theInstallation IDis displayed in the page URL.
-
-
For Name, provide a GitHub Check run name. If this GitHub Check run doesn’t exist, it is created. If this GitHub Check run already exists, it is updated.
-
For Status, select Completed.
-
For Conclusion, select Select None.
If you select any other option, that will be the conclusion of the check regardless of the results of your code linting scan.
-
For Title, enter a title for the check run. For example,
SonarQube lint check. Theoutput.titlefield has a maximum length defined in the GitHub Checks API documentation. -
For Summary, enter a summary to describe the check run. For example,
This check is performed by GitHub App #1234 in CloudBees CD/RO pipeline SonarQube lint GitHub check. Theoutput.summaryfield has a maximum length defined in the GitHub Checks API documentation. -
For Text, provide a description of actions. For example,
For a detailed description of error codes, refer to our coding style guide. Theoutput.textfield has a maximum length defined in the GitHub Checks API documentation. -
For Annotation, enter
$[/myPipelineRuntime/scanIssue].Here $[/myPipelineRuntime/scanIssue]is used as it was the variable returned foroutput.annotationsandoutput.annotations.annotation_levelfrom Transform the scan results into DSL properties. -
For Result property sheet, you can leave as
/myJob/githubChecksor enter a custom value.
-
-
Once you have provided the Input parameters, select Save changes.
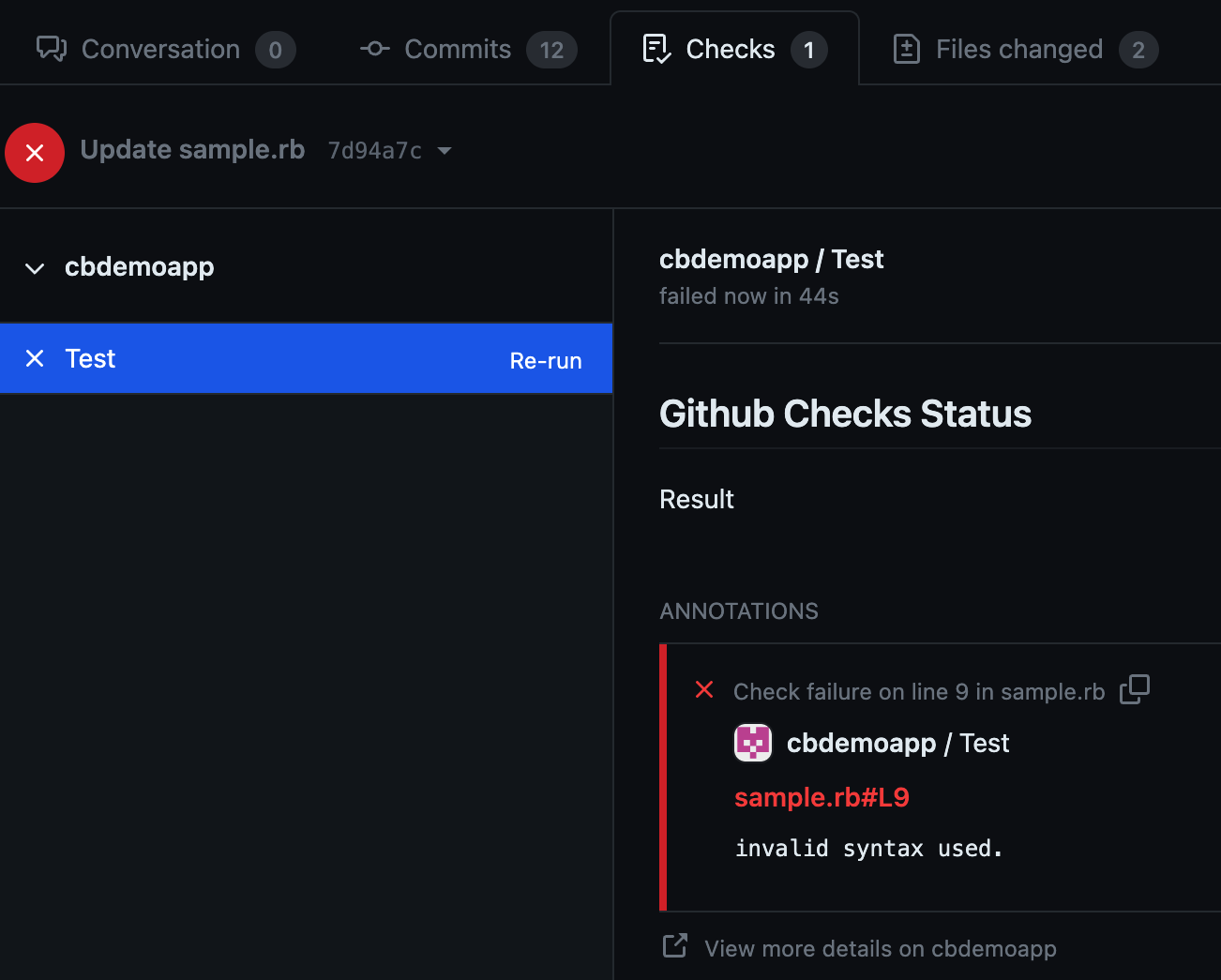
After configuring your pipeline with the GitHub Check plugin, when you make a new commit on a PR within a repository where the GitHub App is installed, this pipeline should run and publish the result to your PR. You can find this results on your GitHub PR in the Checks tab, similar to: