This content applies only to CloudBees CI on modern cloud platforms.
In this scenario, the administrator wants to delegate administer permissions, so the internal-oc-admin-group will be assigned the default pre-configured admin_role. All users in that group will be able to perform cluster management functions in operations center, so membership for this group should be limited to only the Admin team in this example organization. This configuration is propagated to all connected controllers, so operations center-level admins will also have administer permissions over those controllers.
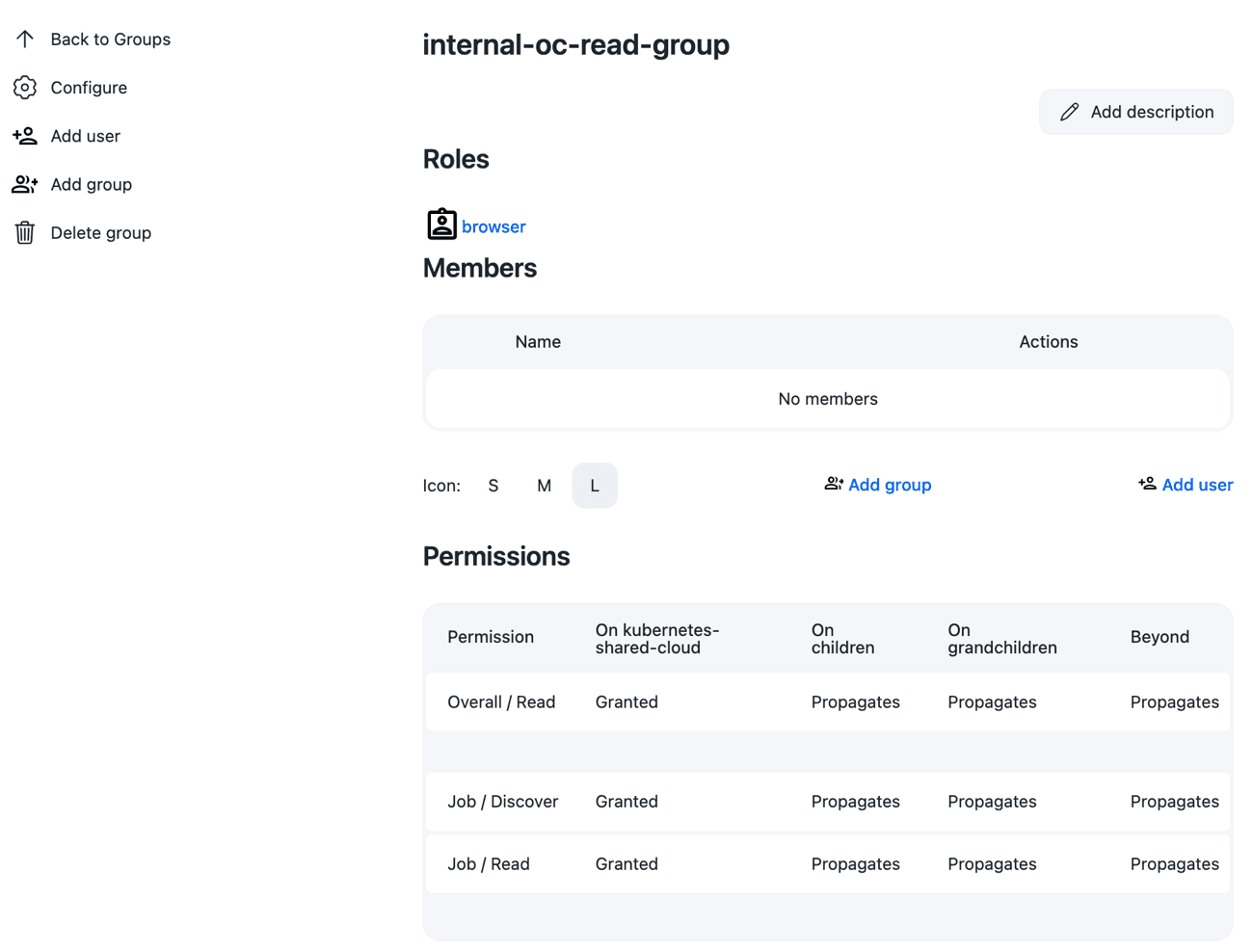
For non-admin teams, the administrator will want to prevent them from changing any configurations to the cluster in operations center, and so the administrator will need to create another group - internal-oc-read-group - and assign to that group the pre-configured read_role. Developer teams and Tester team belong in this group, as they will have limited interactions with operations center and therefore do not need any permissions above read access at the operations center-level.
Groups can be created and configured from the "Groups" item in the left-hand menu. Once a group has been added, administrators will be able to assign roles and users to the group.
| Context | Group | Role(s) | Member(s) |
|---|---|---|---|
ROOT |
internal-oc-admin-group |
|
All the administrator(s) of the operations center instance |
ROOT |
internal-oc-read-group |
|
|
Once the administrator has added themselves to a group with the admin_role, the administrator should disable the default roles of authenticated and anonymous. The *authenticated permission includes overall administration permissions and is no longer necessary once a formal admin role exists and is assigned to an administration group.