Operations center uses the standard Jenkins security model. In other words there are two axes to security:
-
The security realm: Responsible for identifying the user and reporting on any groups that are defined in the security realm to which the user belongs.
-
The authorization strategy: Responsible for determining the set of permissions that an identified user has on any specific object within the Jenkins object tree.
There are three modes you can select with the CloudBees operations center:
-
All Jenkins client controllers are independent and can choose their own security realms and authorization strategies.
-
All Jenkins client controllers will be forced to delegate their security realm to the operations center but can choose their own authorization strategies.
-
All Jenkins client controllers will be forced to delegate their security realm to the operations center and will be forced to use the same authorization strategy configuration as the operations center.
Finally, authorization strategies that are operations center-aware (at the time of writing the only such authorization strategy is the CloudBees Role-Based Access Control plugin) can contextualize the authorization strategy configuration of individual client controllers based on the context within operations center that the client controller is defined in.
Recommended configuration
Securing your CloudBees CI instance is managed on the Security page; select in the upper-right corner to navigate to the Manage Jenkins page, and then select Security. CloudBees recommends configuring the following settings to provide the greatest functionality, flexibility, and secure setup of your CloudBees CI instance.
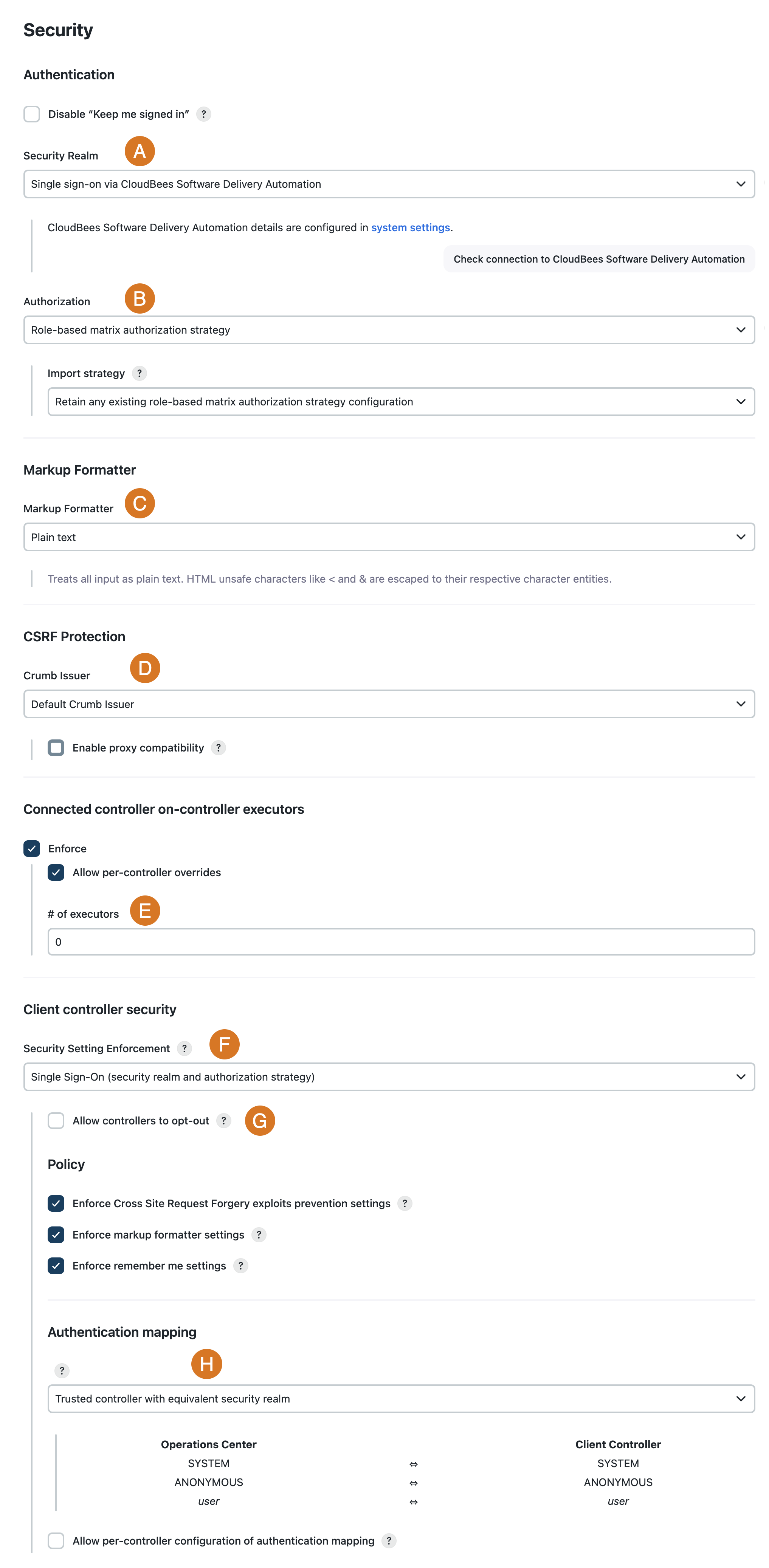
| Label | Field | Description/Recommendation | ||
|---|---|---|---|---|
A |
Security Realm |
Select a security realm that integrates with external company systems and are part of the CloudBees Assurance Program (CAP).
|
||
B |
Authorization |
Select the CloudBees Role-Based Access Control plugin as the authorization strategy.
|
||
C |
Markup Formatter |
The default Plain text markup formatter is safe, but does not support any formatting. For more formatting options, choose OWASP Markup Formatter plugin, which allows use of a safe subset of HTML. |
||
D |
CSRF Protection |
The default value for this setting, Default Crumb Issuer, is safe. If you need more flexible options, consider using the Strict Crumb Issuer plugin. However, this plugin is not supported in CAP. |
||
E |
Connected controller on-controller executors |
Enforce |
||
F |
Security setting enforcement |
Select Single Sign-On (security realm and authorization strategy) for the security settings enforcement policy.
|
||
G |
Allow controllers to opt-out |
If you are integrating existing client controllers into operations center, it may be beneficial to allow client controllers to opt-out of the security settings enforcement policy while you decide how to transition their existing configuration to the operations center managed configuration. |
||
H |
Authentication mapping |
Select the appropriate default authentication mapping strategy. If you have different classes of controllers you will want to enable per-controller configuration of authentication mapping.
|
Configure the security context in Helm charts
Security contexts are a Kubernetes object that defines permissions or capabilities of pods and containers. The securityContext setting allows for a more finely grained security configuration. You can configure the securityContext within the values.yaml file of the Helm chart as shown below.
securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true capabilities: drop: - all