Pod Security Policy (PSP) was deprecated in Kubernetes 1.21 and removed from Kubernetes 1.25. As an alternative, you can enforce Pod Security Standards (PSS) by using Pod Security Admission (PSA). To migrate from PSP to PSA, refer to the Kubernetes migration instructions.
Configure CloudBees CI on modern cloud platforms for compatibility with the PSS baseline profile
No changes are required in CloudBees CI on modern cloud platforms to make it compatible with the baseline PSS profile.
The baseline profile is the recommended configuration for PSS when using CloudBees CI on modern cloud platforms.
|
Configure CloudBees CI on modern cloud platforms for compatibility with the PSS restricted profile
The PSS restricted profile is generally not recommended, as it can cause valid Pipelines to immediately fail.
If you decide to use the PSS restricted profile, there are PSA configuration changes required, based on your setup:
Configure PSA for the operations center
Configure the operations center pod with the required ContainerSecurityContext from the values.yaml. Refer to the following example:
ContainerSecurityContext: allowPrivilegeEscalation: false privileged: false capabilities: drop: - ALL runAsNonRoot: true seccompProfile: type: RuntimeDefault
Configure PSA for controllers
When configuring PSA for controllers, the following options are available:
Apply the configuration to existing individual controllers
Apply the following configuration to each controller in the YAML field of the controller item configuration page in the operations center.
To apply the configuration to existing individual controllers:
-
Select a controller on the operations center dashboard, and then select
 .
. -
On the manage controller page, select
 .
. -
On the item configuration page, navigate to the Advanced configuration section.
-
Paste the following configuration in the YAML field:
kind: StatefulSet apiVersion: apps/v1 spec: template: spec: containers: - securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL runAsNonRoot: true seccompProfile: type: RuntimeDefault name: "jenkins" -
Select Save.
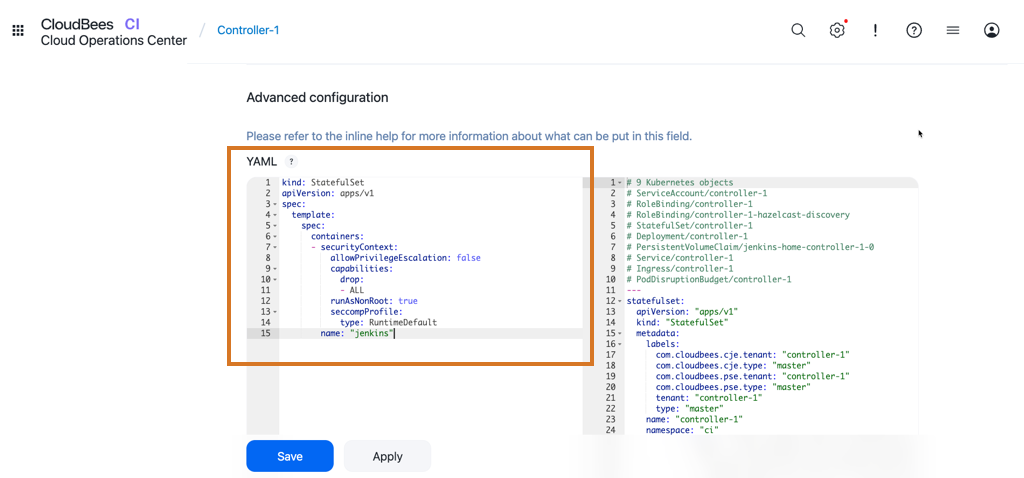 Figure 1. Configure PSA on controller item configuration page
Figure 1. Configure PSA on controller item configuration page
Apply the configuration globally to all new controllers
In the operations center, you can also apply this configuration at the global level in the Default YAML section of the Configure Controller Provisioning page.
| The default configuration only applies to newly-created controllers, and is not applied to existing controllers. |
To apply the configuration globally for new controllers:
-
Select in the upper-right corner to navigate to the Manage Jenkins page.
-
Select Configure Controller Provisioning, and then navigate to the Default YAML section.
-
Paste the following configuration in the Default YAML field:
kind: StatefulSet apiVersion: apps/v1 spec: template: spec: containers: - securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL runAsNonRoot: true seccompProfile: type: RuntimeDefault name: "jenkins" -
Select Save.
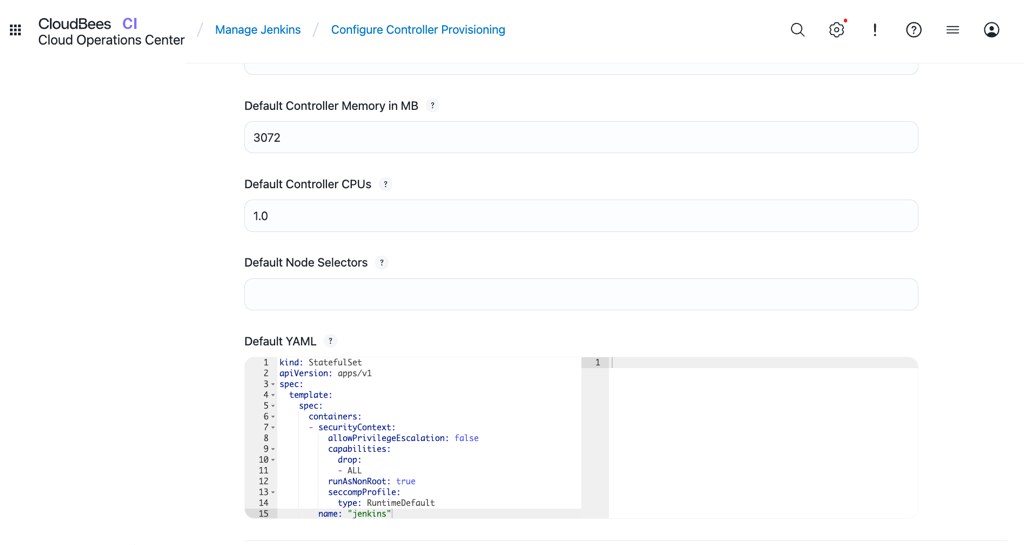 Figure 2. Global PSA configuration on the Configure Controller Provisioning page
Figure 2. Global PSA configuration on the Configure Controller Provisioning page
Configure PSA for Kubernetes build agents
When configuring PSA for Kubernetes build agents, the following options are available depending on the CloudBees CI version:
Configure PSA for Kubernetes build agents on CloudBees CI on modern cloud platforms 2.141.1.4 and later
In CloudBees CI on modern cloud platforms 2.141.1.4 and later, you can automatically inject the required securityContext into the agent containers.
-
Select in the upper-right corner to navigate to the Manage Jenkins page.
-
Select Clouds and then select New cloud. + Enter the name of the cloud, and select Kubernetes as the cloud type.
-
Select Inject restricted PSS security context in agent container definition in the Kubernetes Cloud configuration.
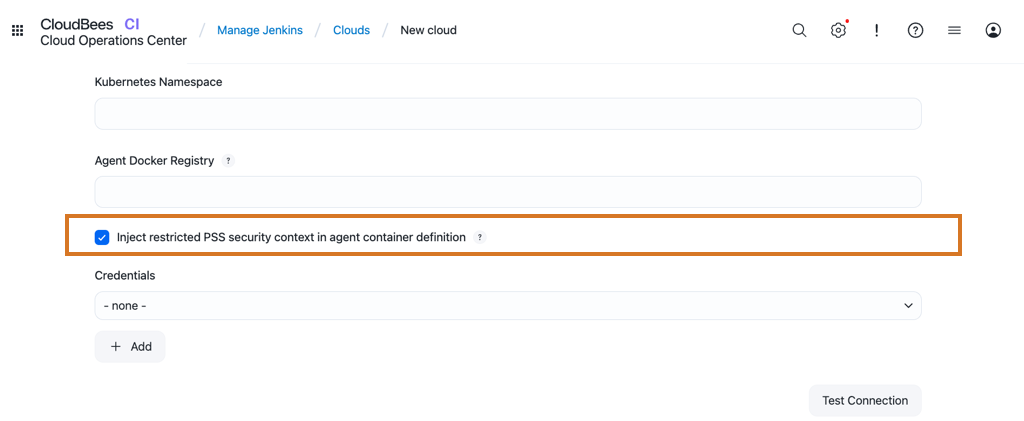 Figure 3. Configure the PSS restricted profile
Figure 3. Configure the PSS restricted profile
Configure PSA for Kubernetes build agents on CloudBees CI on modern cloud platforms prior to 2.141.1.4
All containers in build agents running in Kubernetes need to define the expected container securityContext in the values.yaml. Refer to the following examples.
apiVersion: "v1" kind: "Pod" spec: containers: - name: <container_name> securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL runAsNonRoot: true seccompProfile: type: RuntimeDefault
Kubernetes build agents (provisioned by the kubernetes Jenkins plugin) have a default container injected transparently. It is the jnlp container. This container needs to be overridden to add the securityContext configuration. Apart from the user-defined containers, there must be an override for the jnlp container too:
containers: - name: jnlp(1) securityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL runAsNonRoot: true seccompProfile: type: RuntimeDefault
| 1 | jnlp is a reserved container name used by the Kubernetes plugin. |
For Windows agents, most of the securityContext values are not supported and must be omitted. PSA allows that for compatibility, as long as .spec.os.name is set to windows. Refer to Windows containers in Kubernetes for more information.
Configure PSA for the hibernation monitor
If the hibernation monitor is enabled, configure SecurityContext in the values.yaml file. Refer to the following example:
Hibernation: Enabled: true SecurityContext: allowPrivilegeEscalation: false capabilities: drop: - ALL runAsNonRoot: true seccompProfile: type: RuntimeDefault
Configure PSA for the Ingress controller
When configuring PSA for Ingress controllers, the following options are available depending on the NGINX version:
Configure PSA for the Ingress controller (NGINX version 4.11.2 and later)
When configuring PSA for Ingress controllers running NGINX version 4.11.2 and later, no special configuration is required. For more information, refer to Support Pod Security Standard = "restricted" in the Helm chart.
Configure PSA for the Ingress controller (NGINX version prior to 4.11.2)
ingress-nginx does not support PSA. For more information, refer to Deprecate PSP and use PSA. Therefore, if ingress-nginx is installed using the deprecated built-in Helm chart (where CloudBees CI uses ingress-nginx.Enabled: true in the values.yaml), then PSA cannot be enabled. The solution is to install the Ingress controller separately in another namespace (instead of using the CloudBees CI Helm chart inline installation) and do not enable PSA on that namespace.