This content applies only to CloudBees CI on modern cloud platforms and managed controllers.
In a CloudBees CI on modern cloud platforms installation, users with the appropriate CasC permissions can configure managed controllers by adding CasC bundle locations in the operations center. The operations center uses the bundles in the locations to configure the managed controllers.
Because the operations center is the only source of CasC bundles for the managed controllers, this setup creates a single point of failure. Additionally, if your organization has a large number of managed controllers, the operations center performance may be impacted as it is responsible for the following operations:
-
Query the bundle locations for new bundles or updates.
-
Check out new bundles and updates to the operations center local storage.
-
Validate the bundles.
-
Distribute the bundles to the managed controllers.
To address these scenarios, CloudBees provides the CasC Controller Bundle Service. This service, disabled by default, is installed as a part of the CloudBees CI on modern cloud platforms Helm chart and, if enabled, frees the operations center from the responsibility of distributing CasC bundles to managed controllers.
|
Using the CasC Controller Bundle Service and using the operations center to distribute CasC bundles are not mutually exclusive. Administrators can use both methods to distribute CasC bundles to managed controllers, according to their needs. However, a managed controller can only be configured to use one method at a time. The CasC bundle comes from the operations center or from the CasC Controller Bundle Service. CloudBees recommends using the CasC Controller Bundle Service, particularly when you have a large number of managed controllers. |
|
The CasC Controller Bundle Service does not support Bundle inheritance or bundle availability. If the |
Enable the CasC Controller Bundle Service for CloudBees CI on modern cloud platforms
Install CloudBees CI covers the requirements and the installation process for CloudBees CI on modern cloud platforms.
Specific installation instructions depend on your CloudBees CI setup, and the infrastructure where CloudBees CI is deployed.
The installation process is typically performed using Helm charts, where the CasC Controller Bundle Service is disabled by default, and by running the helm install command where needed, depending on your CloudBees CI setup.
To enable the CasC Controller Bundle Service on default setups, you must add the following property to the values.yaml files used to install CloudBees CI:
CascBundleService: enabled: true(1) createConfig: true|false(2)
| 1 | Enable the CasC Controller Bundle Service service. The default value is false, which leaves the service disabled. |
| 2 | This property is optional and it is used to automatically create the Kubernetes secret that holds the connectors and credentials configuration.
If set to true, the default value, the CasC Controller Bundle Service creates the secret with the name casc-bundle-service-config in the operations center namespace.
If set to false, the CasC Controller Bundle Service does not create the secret, and administrators must create it manually before deploying the service. |
|
If |
Different CloudBees CI setup requires different values.yaml files, different helm install commands, and varying enablement of the CasC Controller Bundle Service.
-
For Single cluster and single namespace setups, where the operations center and all managed controllers are deployed in the same Kubernetes cluster and in the same namespace (the default setup), you must enable the service in the
values.yamlfile used to install CloudBees CI in the unique existing namespace.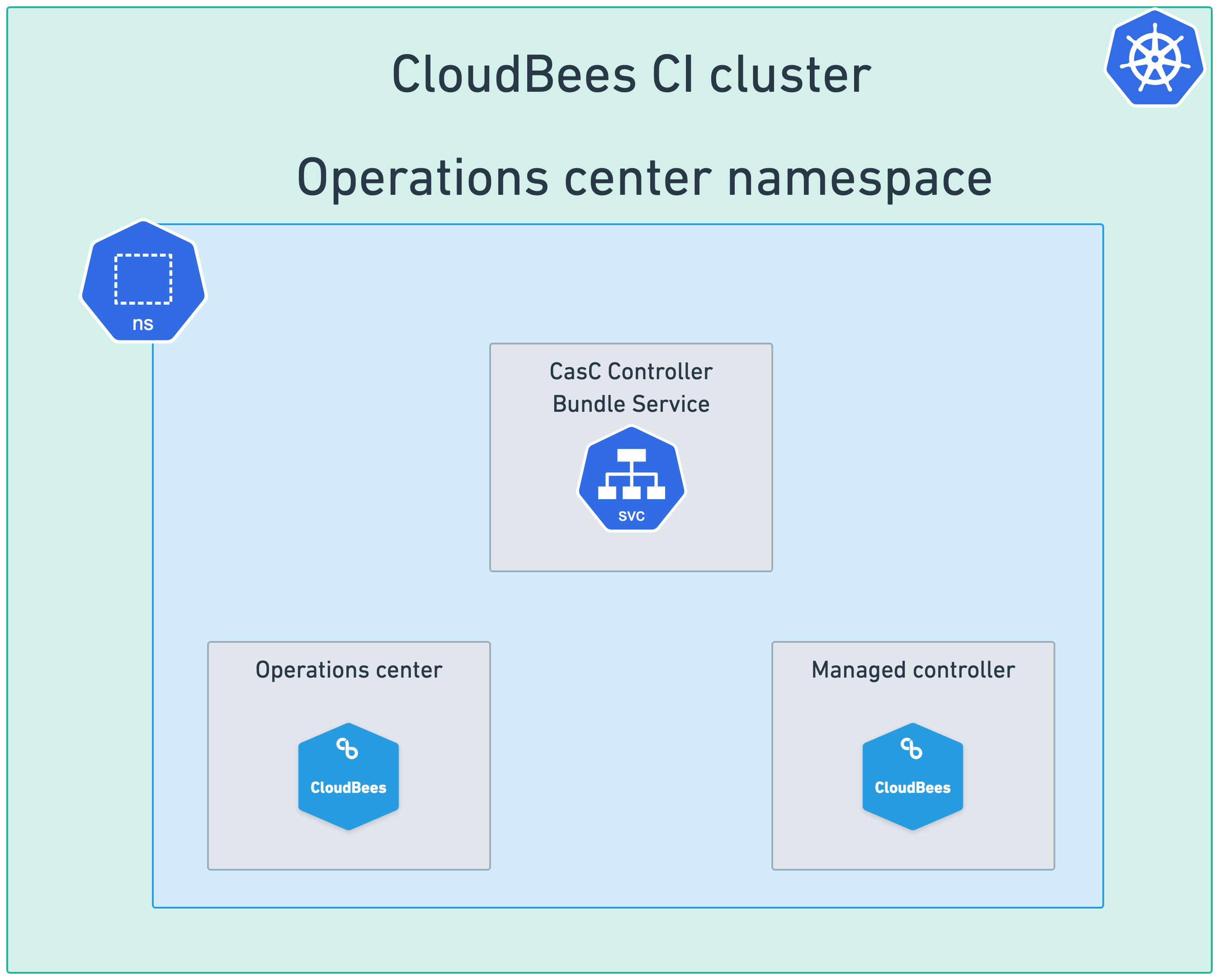 Figure 1. Single cluster and single namespace setup with the CasC Controller Bundle Service enabled
Figure 1. Single cluster and single namespace setup with the CasC Controller Bundle Service enabled -
For Single cluster and multiple namespaces setups, where the operations center and all managed controllers are deployed in the same Kubernetes cluster but in different namespaces, you must enable the CasC Controller Bundle Service only in the
values.yamlfile used to install CloudBees CI in the operations center namespace, leaving the CasC Controller Bundle Service disabled in the other namespaces.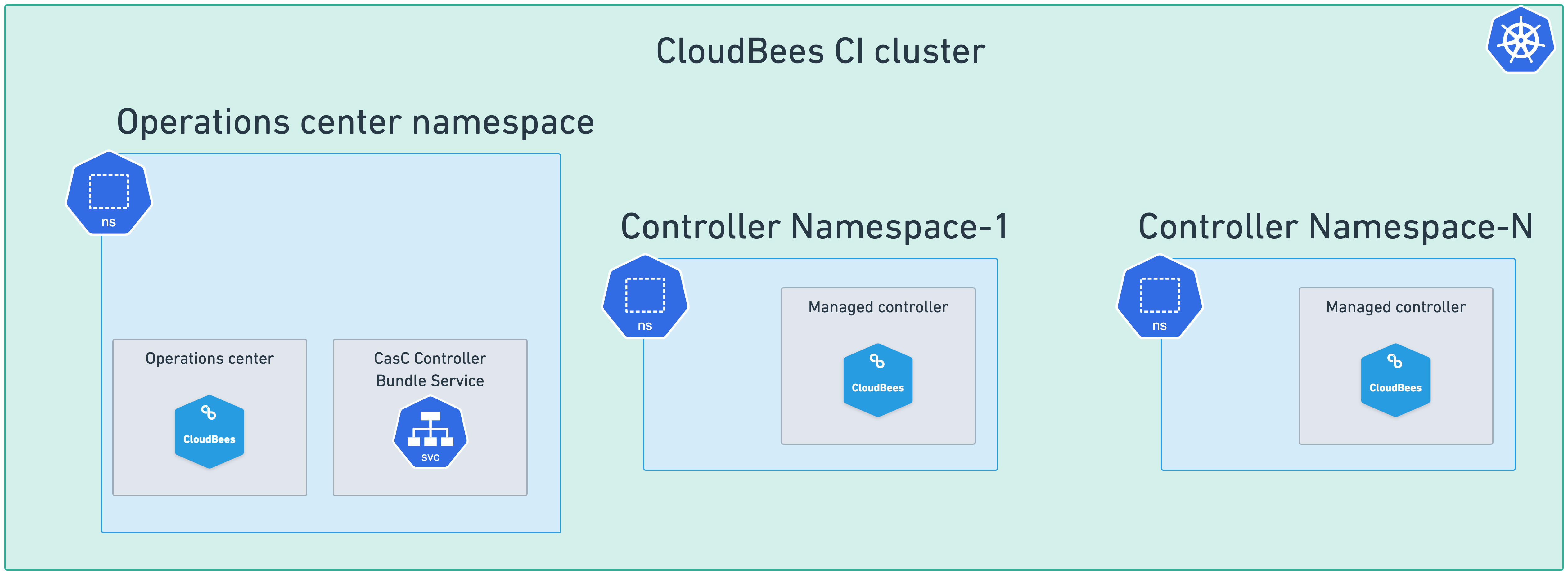 Figure 2. Single cluster and multiple namespaces setup with the CasC Controller Bundle Service enabled
Figure 2. Single cluster and multiple namespaces setup with the CasC Controller Bundle Service enabled -
For Multiple cluster setups, where the operations center and the managed controllers are deployed in different Kubernetes clusters, you must enable the CasC Controller Bundle Service while installing the operations center, in only one of the controller namespaces in other clusters.
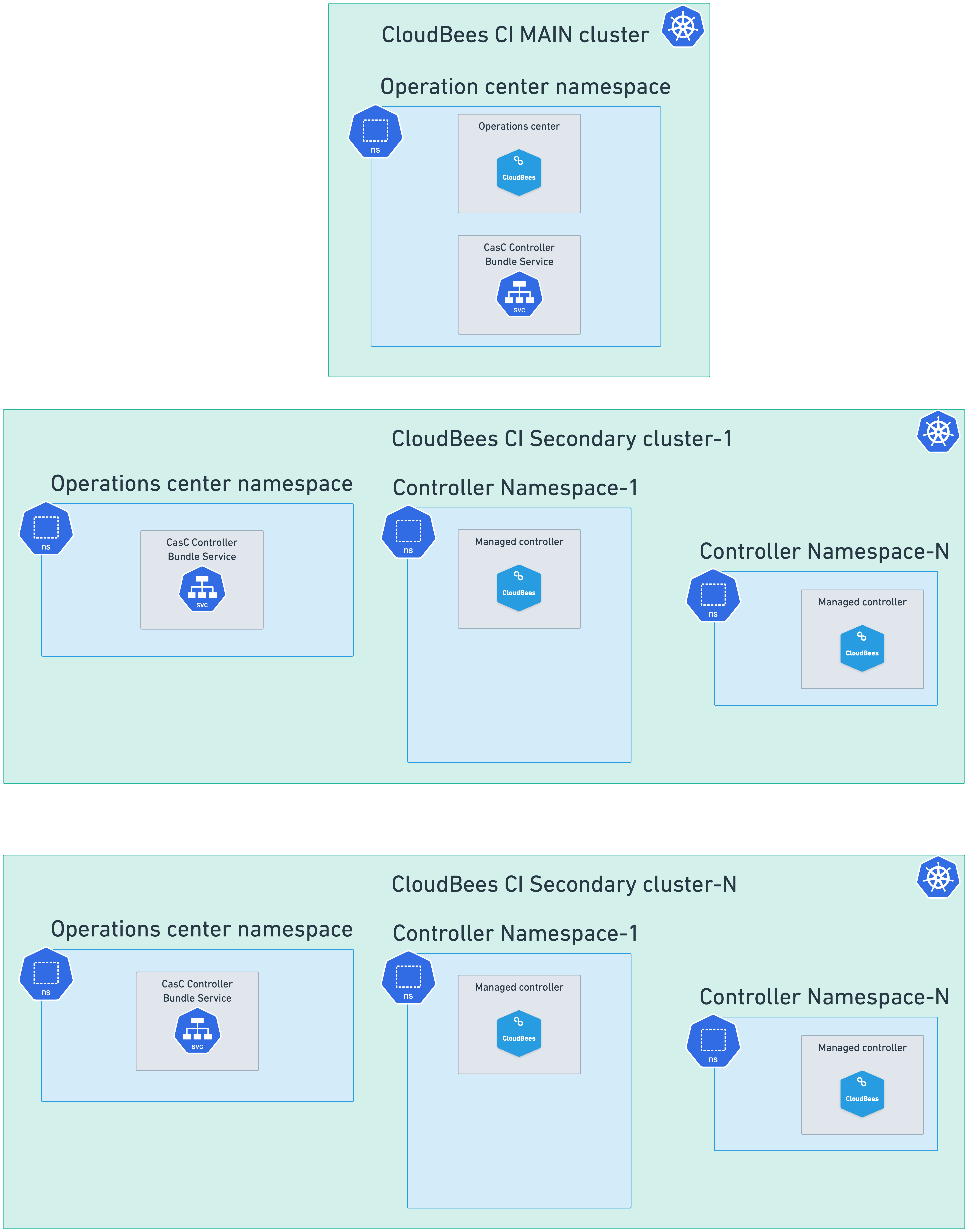
Refer to Install CloudBees CI and Deploy CloudBees CI across multiple Kubernetes namespaces and clusters for detailed information about the different CloudBees CI setups, the different helm install commands, and the different values.yaml files involved and how to install CloudBees CI.
CasC Controller Bundle Service architecture
Regardless of the CloudBees CI setup chosen for deploying CloudBees CI, or where the CasC Controller Bundle Service has been enabled, the CasC Controller Bundle Service architecture looks like the following image from a high-level perspective:
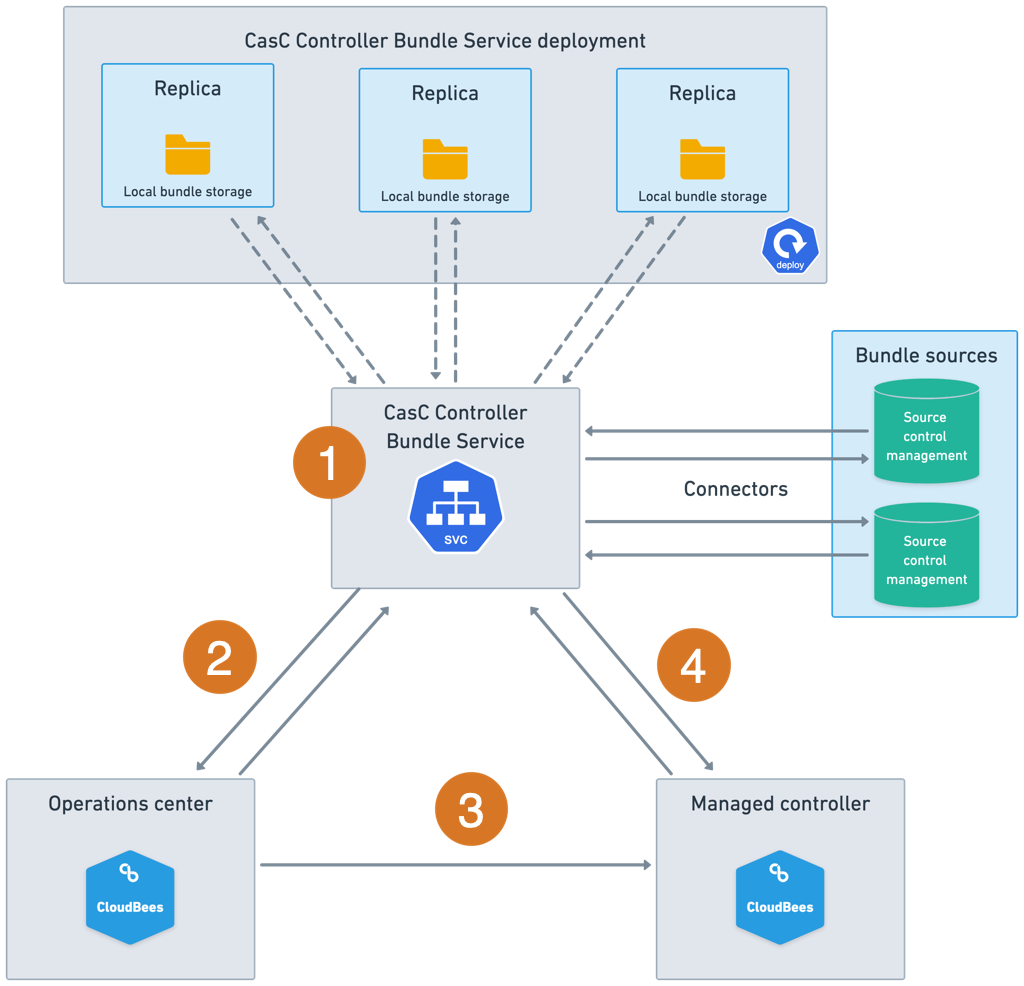
-
The CasC Controller Bundle Service is a separate service. It can be enabled during the CloudBees CI installation, and it is configured with connectors to the locations where the CasC bundles are stored. A connector is an authenticated connection from the CasC Controller Bundle Service to systems that serve CasC bundles (SCMs in the image).
-
The CasC Controller Bundle Service periodically queries the connectors to retrieve the CasC bundles.
-
When administrators create or update a managed controller, the operations center queries the CasC Controller Bundle Service and retrieves a list of available bundles.
-
The managed controller is configured to use a CasC bundle provided by the CasC Controller Bundle Service.
-
The managed controller retrieves the CasC bundle from the CasC Controller Bundle Service. After the CasC bundle is applied, the managed controller periodically checks the CasC Controller Bundle Service for updates.
Enable debug logs for the CasC Controller Bundle Service
To test the CasC Controller Bundle Service or troubleshoot issues, enable DEBUG logs by adding the following property to the values.yaml that enables the CasC Controller Bundle Service:
CascBundleService: javaOpts: -Dquarkus.log.category."com.cloudbees".level=DEBUG
Security context for the CasC Controller Bundle Service pods
As described in the service architecture, the CasC Controller Bundle Service creates a Kubernetes deployment. Security contexts for the service pods and containers are empty by default. However, the CasC Controller Bundle Service requires a security context configuration if CloudBees CI runs in a Kubernetes cluster that defines Pod Security Standards by using Pod Security Admission (PSA) labels.
Administrators can provide custom pod security contexts or custom container security contexts by adding the PodSecurityContext or the ContainerSecurityContext property to the CascBundleService section in the values.yaml files where the CasC Controller Bundle Service is enabled, as shown in the following examples:
CascBundleService: ... PodsecurityContext: fsGroup: 1000 runAsUser: 1000 runAsGroup: 1000 ...
CascBundleService: ... ContainerSecurityContext: allowPrivilegeEscalation: false privileged: false runAsGroup: 10001 runAsNonRoot: true runAsUser: 10001 ...
|
If no value is provided for
|
Refer to the Kubernetes documentation for more information on pods and containers security contexts.
Add connectors to the CasC Controller Bundle Service
|
For Multiple cluster setups, this process must be performed in the operations center namespace of each Kubernetes cluster where the CasC Controller Bundle Service is enabled. In the Kubernetes cluster where the operations center runs, the CasC Controller Bundle Service configuration must list all connectors. These connectors allow the operations center to configure managed controllers in any other Kubernetes cluster where the CasC Controller Bundle Service is enabled. For the rest of the Kubernetes clusters in a multiple cluster setup, the CasC Controller Bundle Service only needs to contain the connectors for the CasC bundles used by the managed controllers in that cluster. Those managed controllers periodically perform checkouts, looking for updates to the bundles they use. |
The service, as described in the CasC Controller Bundle Service architecture, uses connectors to retrieve CasC Bundle from SCMs.
When the service is enabled, using the CascBundleService.createConfig Helm chart property, you can decide whether to create the Kubernetes secret that holds the connectors and credentials configuration automatically or manually.
The secret is empty when created automatically (CascBundleService.createConfig: true) and must be populated with the connectors and credentials configuration. If the secret is created manually (CascBundleService.createConfig: false), administrators must create it before the CasC Controller Bundle Service is deployed.
Regardless of whether the Kubernetes secret is created automatically or manually, it must have the following structure:
apiVersion: v1 kind: Secret metadata: name: casc-bundle-service-config (1) labels: app: casc-bundle-service (2) type: Opaque stringData: service-configuration.yaml: | (3) connectors: ... <list-of-connectors> (4) ... credentials: ... <list-of-credentials> (5) ... knownHosts: (6) ... <public-keys-for-ssh-connectors> ...
| 1 | Keep casc-bundle-service-config as the name of the secret. |
| 2 | Keep casc-bundle-service as the value for the app label. |
| 3 | The service-configuration.yaml key contains the configuration for the CasC Controller Bundle Service. |
| 4 | List of connectors to the SCM repositories. |
| 5 | List of credentials referenced by the connectors to authenticate to the SCM repositories. |
| 6 | (Optional) List of public keys required for SSH connectors.
Those keys are usually stored in your ~/.ssh/known_hosts file. |
Connectors and credentials properties are listed in the tables below:
| Property name | Required | Description | Example | ||
|---|---|---|---|---|---|
|
Yes |
A unique identifier for the connector. |
|
||
|
Yes |
The URL of the SCM repository. HTTP and SSH URLs are supported. HTTP URLs can use token or username and password authentication. SSH URLs use SSH authentication. |
|
||
|
No |
The type of connector.
|
|
||
|
No |
The branch of the repository to use.
|
|
||
|
No |
The relative path to the directory containing the CasC bundles. |
|
||
|
No |
It provides an authentication method for push notifications from the connector. Refer to Notification webhooks for the SCM connectors for more information. |
|
||
|
Yes |
The credential used for the connector. It contains subproperties of fields described in more detail in the table below. |
credential: token: tokenCred type: token |
| Credential property name | Required | Description | Example | ||
|---|---|---|---|---|---|
|
Only required if used to reference a credential defined in the |
It uses and ID to reference a credential defined in the |
|
||
|
Only required if the |
The type of credential.
The supported values are |
|
||
|
Required if the |
The token to use for authentication. |
|
||
|
Required if the |
The username to use for authentication. |
|
||
|
Required if the |
The password to use for authentication. |
|
||
|
Required if the |
The SSH key to use for authentication.
|
|
||
|
No |
The passphrase to use for the SSH key.
Only used if the |
|
||
|
Only required if the |
This property refers to the GitHub application ID that must be created to display bundle validation results in a GitHub pull request. Refer to Bundle validation using the CasC Controller Bundle Service for more information. |
|
||
|
Only required if the |
A PKCS8 key used for authentication in the GitHub application. Refer to Bundle validation using the CasC Controller Bundle Service for more information. |
|
||
|
Only required for loading credentials from another Kubernetes secret. |
This property refers to the name of the Kubernetes secret containing the values for the different credential properties. Refer to Use Kubernetes secrets to store credentials for more information. |
|
|
When defining connectors, if the Each credential must have a unique |
apiVersion: v1 kind: Secret metadata: name: casc-bundle-service-config labels: app: casc-bundle-service type: Opaque stringData: service-configuration.yaml: | connectors: - id: id1 url: https://<your-repository1-url> webhookSecret: <your-webhook-secret> (1) credential: credentialId: cred1 type: reference - id: id2 url: https://<your-repository2-url> branch: testBranch path: testPath type: scm credential: user: bob password: fake type: userPassword - id: id3 url: https://<your-repository3-url> credential: credentialId:cred3 - id: id4 url: ssh://<your-ssh-user>@<your-ssh-server>/<your-repository4-name>.git credential: credentialId: cred4 - id: id5 url: ssh://<your-ssh-user>@<your-ssh-server>/<your-repository5-name>.git credential: sshKey: longSSHKey passPhrase: passPhrase type: sshKey - id: id6 url: https://github.com/<your-organization-or-username>/<your-repository6-name>.git credential: credentialId: cred6 credentials: - credentialId: cred1 user: bob password: fake type: userPassword - credentialId: cred3 sshKey: longSSHKey type: sshKey - credentialId: cred4 sshKey: longSSHKey passPhrase: passPhrase type: sshKey - credentialId: cred6 appId: <your-github-app-id> type: githubAppKey privateKey: | -----BEGIN PRIVATE KEY----- key-content -----END PRIVATE KEY----- knownHosts: | (2) # github.com:22 SSH-2.0-7d0489107 github.com ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOMqqnkVzrm0SdG6UOoqKLsabgH5C9okWi0dh2l9GKJl # github.com:22 SSH-2.0-7d0489107 github.com ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCj7ndNxQowgcQnjshcLrqPEiiphnt+VTTvDP6mHBL9j1aNUkY4Ue1gvwnGLVlOhGeYrnZaMgRK6+PKCUXaDbC7qtbW8gIkhL7aGCsOr/C56SJMy/BCZfxd1nWzAOxSDPgVsmerOBYfNqltV9/hWCqBywINIR+5dIg6JTJ72pcEpEjcYgXkE2YEFXV1JHnsKgbLWNlhScqb2UmyRkQyytRLtL+38TGxkxCflmO+5Z8CSSNY7GidjMIZ7Q4zMjA2n1nGrlTDkzwDCsw+wqFPGQA179cnfGWOWRVruj16z6XyvxvjJwbz0wQZ75XK5tKSb7FNyeIEs4TT4jk+S4dhPeAUC5y+bDYirYgM4GC7uEnztnZyaVWQ7B381AK4Qdrwt51ZqExKbQpTUNn+EjqoTwvqNj4kqx5QUCI0ThS/YkOxJCXmPUWZbhjpCg56i+2aB6CmK2JGhn57K5mj0MNdBXA4/WnwH6XoPWJzK5Nyu2zB3nAZp+S5hpQs+p1vN1/wsjk= # github.com:22 SSH-2.0-7d0489107 github.com ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEmKSENjQEezOmxkZMy7opKgwFB9nkt5YRrYMjNuG5N87uRgg6CLrbo5wAdT/y6v0mKV0U2w0WZ2YB/++Tpockg=
| 1 | The webhookSecret property is used to authenticate the push notifications from the SCM repository. Replace <your-webhook-secret> with the desired secret used to authenticate the push notifications.
Refer to Notification webhooks for the SCM connectors for more information. |
| 2 | github.com public key retrieved using ssh-keyscan github.com.
The secret includes this public key in the knownHosts section because of the id5 SSH connector that refers to a github.com repository. |
To update the list of connectors you must update the values stored in the Kubernetes secret.
kubectl replace secret generic casc-bundle-service-config -n <oc-namespace> --from-file service-configuration.yaml=<your-secret-yaml-file> (1)
| 1 | Replace oc-namespace with the operations center namespace where the CasC Controller Bundle Service was enabled, and <your-secret-yaml-file> with the name of the file with the Kubernetes secret holding the connector configurations and credentials. |
Once the secret defining the connectors is updated, you can use one of the following options to get the CasC Controller Bundle Service to use the new list.
-
Wait until the next connector polling cycle (defaults to 5 minutes).
The default polling interval can be changed by setting the
CascBundleService.pollingIntervalproperty in thevalues.yamlfile used to install CloudBees CI.CascBundleService: enabled: true pollingSchedule: 5m (1)1 Replace 5mwith the desired polling interval. The default value is5m, which means that the CasC Controller Bundle Service polls the connectors every 5 minutes.
|
When reducing the polling interval, the new value must be greater than the time the CasC Controller Bundle Service requires to checkout all the bundles from the different connectors. |
-
Restart the CasC Controller Bundle Service with the following command:
kubectl rollout restart deployment casc-bundle-service -n <your-oc-namespace> (1)1 Replace <your-oc-namespace>with the operations center namespace where the CasC Controller Bundle Service was enabled.
Use Kubernetes secrets to store credentials
Values for the different credential properties can be loaded from Kubernetes secrets into the casc-bundle-service-config secret.
This process requires the following steps:
-
Set
CascBundleService.credentialSecretsNamespaceas a Helm chart property in thevalues.yamlfile used to install CloudBees CI. This property defines the namespace where the Kubernetes secrets containing credentials are stored. The namespace must exist before the CasC Controller Bundle Service is enabled.If the
CascBundleService.credentialSecretsNamespaceproperty is set, the namespace must be created before the CasC Controller Bundle Service is enabled. If the namespace does not exist, the installation of the Helm chart fails. -
Use the
sourceproperty in the credential definition to refer to the Kubernetes secret containing the values for the different credential properties. The values of the credential properties are then replaced with the values defined in the Kubernetes secret. For example, ifuser: user-datais part of the credential definition,user-datais replaced with the value ofuser-dataproperty in the Kubernetes secret definition. See the examples below for further information:
|
When defining a Kubernetes secret to feed the values for the credentials properties, you can use a separate secret for each credential or a single secret containing the values for multiple credentials. |
credentials sectionconnectors: - id: id1 url: https://<your-repository-url> credential: credentialId: cred1(1) ... credentials: - credentialId: cred1(2) user: user-data(3) password: password-data(4) type: userPassword source: userPasswordSecretName(5)
| 1 | The credentialId property is used to reference a credential defined in the credentials section. |
| 2 | The credentialId property is the name of the credential defined in the credentials section. |
| 3 | The user-data property is the name of the property in the Kubernetes secret that contains the user name. |
| 4 | The password-data property is the name of the property in the Kubernetes secret that contains the user password. |
| 5 | The source property is the name of the Kubernetes secret that contains the values for the user-data and password-data properties. The secret must be created in the namespace defined by the CascBundleService.credentialSecretsNamespace property in the values.yaml file. |
apiVersion: v1 kind: Secret metadata: name: userPasswordSecretName data: user-data: <base64 encoded username> password-data: <base64 encoded password>
connectors: - id: id1 url: https://<your-repository-url> credential: token: token-data(1) type: token source: tokenSecretName(2)
| 1 | The token-data property is the name of the property in the Kubernetes secret that contains the token. |
| 2 | The source property is the name of the Kubernetes secret that contains the value for the token-data property. The secret must be created in the namespace defined by the CascBundleService.credentialSecretsNamespace property in the values.yaml file. |
kind: Secret metadata: name: tokenSecretName data: token-data: <base64 encoded token>
connectors: - id: id1 url: git@<your-git-repository-url> credential: sshKey: key-data(1) passphrase: passphrase-data(2) type: sshKey source: sshSecretName(3)
| 1 | The key-data property is the name of the property in the Kubernetes secret that contains the SSH private key. |
| 2 | The passphrase-data property is the name of the property in the Kubernetes secret that contains the SSH private key passphrase. |
| 3 | The source property is the name of the Kubernetes secret that contains the values for the key-data and passphrase-data properties. The secret must be created in the namespace defined by the CascBundleService.credentialSecretsNamespace property in the values.yaml file. |
apiVersion: v1 kind: Secret metadata: name: sshSecretName data: key-data: <base64 encoded private key> passphrase-data: <base64 encoded passphrase>
connectors: - id: id1 url: https://<your-repository2-url> credential: user: user-data (1) password: password-data (2) type: userPassword source: multipleSecretName(3) - id: id2 url: https://<your-repository-url> credential: token: token-data(4) type: token source: multipleSecretName(3) - id: id3 url: git@<your-git-repository-url> credential: sshKey: key-data(5) passphrase: passphrase-data(6) type: sshKey source: multipleSecretName(3)
| 1 | The user-data property is the name of the property in the Kubernetes secret that contains the user name. |
| 2 | The password-data property is the name of the property in the Kubernetes secret that contains the user password. |
| 3 | The source property is the name of the Kubernetes secret that contains the values for the user-data, password-data, token-data, key-data, and passphrase-data properties. The secret must be created in the namespace defined by the CascBundleService.credentialSecretsNamespace property in the values.yaml file. |
| 4 | The token-data property is the name of the property in the Kubernetes secret that contains the token. |
| 5 | The key-data property is the name of the property in the Kubernetes secret that contains the SSH private key. |
| 6 | The passphrase-data property is the name of the property in the Kubernetes secret that contains the SSH private key passphrase. |
apiVersion: v1 kind: Secret metadata: name: multipleSecretName data: user-data: <base64 encoded username> password-data: <base64 encoded password> token-data: <base64 encoded token> key-data: <base64 encoded private key> passphrase-data: <base64 encoded passphrase>
Configure a managed controller using a bundle from the CasC Controller Bundle Service
The process to configure a managed controller using a CasC bundle from the CasC Controller Bundle Service is similar to the process described in Set up a managed controller using CasC. The only difference appears in the managed controller configuration screen, where you must select whether you are using a CasC bundle to configure the controller or not, and the source for the CasC bundles (the operations center or the CasC Controller Bundle Service) if you are using one.
To configure a managed controller using a CasC bundle from the CasC Controller Bundle Service, follow these steps:
-
Select New Item from the operations center main menu.
-
Enter a name for the managed controller in the Item name field.
-
Select the Managed Controller option.
-
Click OK.
In the controller configuration screen:
-
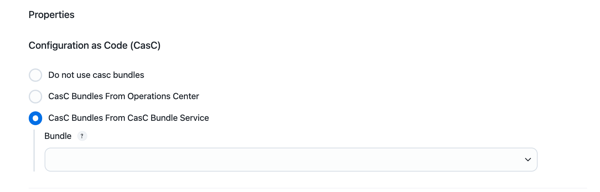
Scroll down to the Configuration as Code (CasC) section.
-
Select CasC Bundles From CasC Bundle Service as the source for the CasC bundles.
-
Select the bundle for the new managed controller from the Bundle dropdown list.
-
Set the rest of the configuration options as needed.
-
Select Save.
|
Bundles displayed in the Bundle dropdown list are retrieved from the connectors. The dropdown list displays the value of the Description field in the bundle.yaml file to identify the CasC bundle. If the Description field is not set, the dropdown list displays information from the connector configuration instead. CloudBees recommends using meaningful descriptions for the CasC bundles to make them easier to identify in the dropdown list. |
Notification webhooks for the SCM connectors
When the CasC Controller Bundle Service is enabled, the service automatically creates the following endpoints in your Kubernetes cluster to receive push notifications from the SCM repositories associated with the connectors:
-
/casc-bundle-service/api/v1/github-webhookfor GitHub repositories. -
/casc-bundle-service/api/v1/gitlab-webhookfor GitLab repositories. -
/casc-bundle-service/api/v1/bitbucket-webhookfor Bitbucket repositories.
You must configure your SCM repositories to send push notifications to the CasC Controller Bundle Service endpoints.
If the webhookSecret property is set in the connector configuration, you must also add the secret to the webhook configuration in the SCM repository.
When the CasC Controller Bundle Service receives a push notification due to changes in any of the CasC bundles:
-
It finds the connector associated with the webhook.
-
Authenticates the request using the
webhookSecretproperty. -
Checks out the new CasC bundle.
-
Makes the new bundle available for the managed controllers using the connector.
|
The If this property is set to |
Bundle validation using the CasC Controller Bundle Service
Troubleshoot CasC for controllers describes how to validate and troubleshoot problems with controller CasC bundles.
From the operations center UI, administrators can select a CasC bundle provided by the CasC Controller Bundle Service to configure a managed controller. CasC bundles are automatically validated when applied to managed controllers. The validation results appear in the Configuration as Code export and update screen, specifically in the Bundle update and Update log tabs and in the managed controller logs.
In addition to the validations described in Troubleshoot CasC for controllers, administrators can display bundle validation results using GitHub Checks. When administrators update a CasC bundle and create a new pull request in a GitHub repository, CasC Controller Bundle Service automatically validates the bundle against the first managed controller found using that bundle. After the validation process, the validation results display in the pull request as a GitHub check.
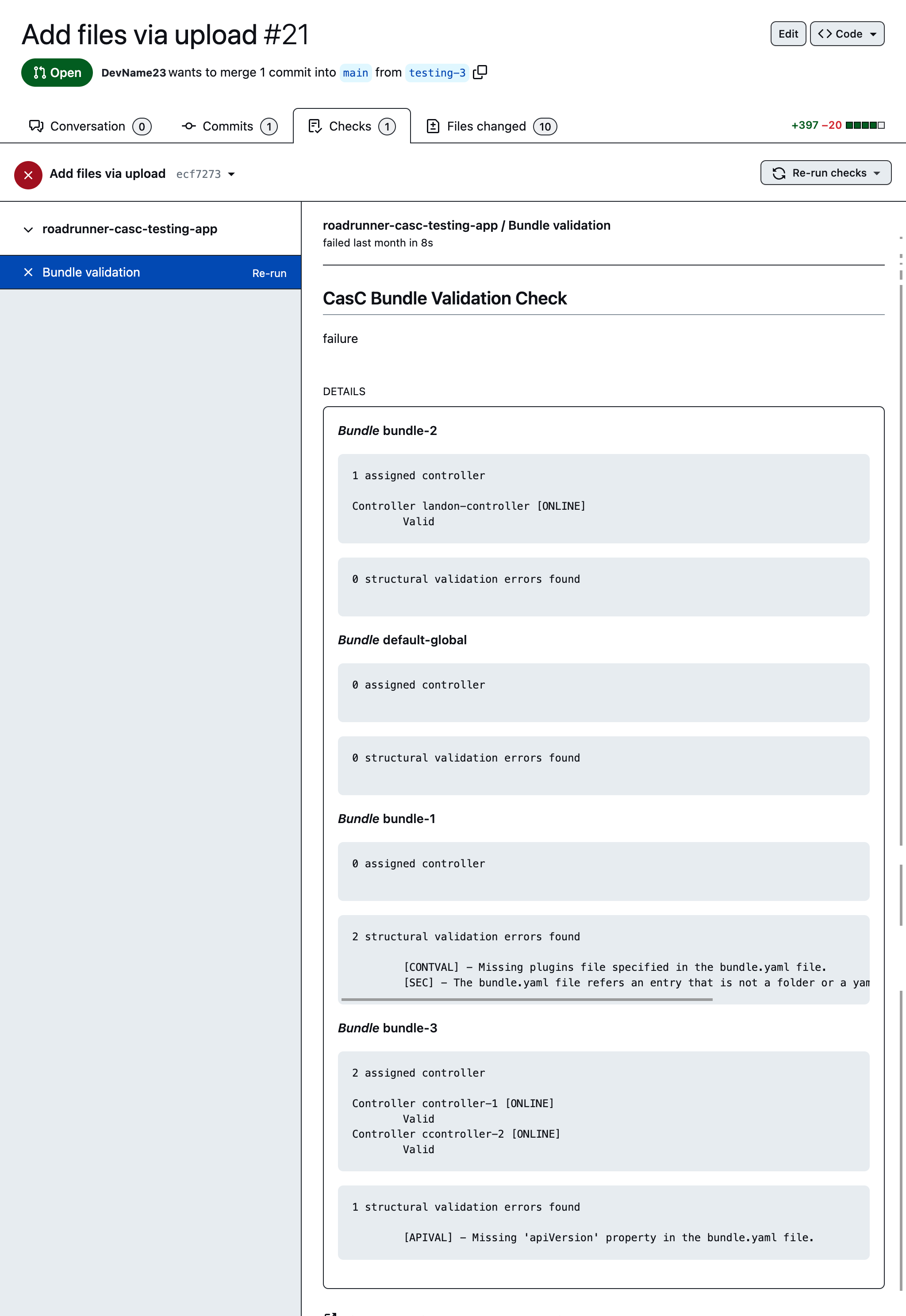
Administrators can review these validation results, and if they are acceptable, merge the pull request to update the bundle in the repository. The CasC Controller Bundle Service then notifies all managed controllers using that bundle to update their configuration.
To display the validation results in a GitHub pull request requires the following configurations.
-
Create a GitHub app with the following permissions:
-
Checks:Read and Write. -
Commit Statuses:Read and Write. -
Contents:Read-only. -
Pull Requests:Read-only.
-
-
Once the GitHub app is ready, generate a private key for the GitHub app and download the
pemfile. -
Transform the private key into a PKCS8 key by using the following
opensslcommand.openssl pkcs8 -topk8 -inform PEM -outform PEM -in <your-github-app-key>.pem -out <your-pkcs8-key>.pem -nocrypt (1)1 Replace <your-github-app-key>with the name of the GitHub application key and<your-pkcs8-key>with the name of the PKCS8 key to be used in the connector configuration. -
Install the GitHub app in the repository or repositories where you want to display the validation results.
-
Add the
appIdandprivateKeyproperties to the connector configuration in the Kubernetes secret. Now the CasC Controller Bundle Service can use the GitHub app to display the validation results in the pull request.
apiVersion: v1 kind: Secret metadata: name: casc-bundle-service-config labels: app: casc-bundle-service type: Opaque stringData: service-configuration.yaml: | connectors: .... - url: https://<your-github-repository-url> credential: appId: <your-github-app-id> type: githubAppKey privateKey: -----BEGIN PRIVATE KEY----- key-content -----END PRIVATE KEY----- ....
Alternatively, administrators can also manually validate the bundle using the Configuration as Code (CasC) CLI or by sending requests to the Configuration as Code HTTP API.