The Federal Information Processing Standards (FIPS) are a set of security standards established by the National Institute of Standards and Technology (NIST) to safeguard sensitive data within U.S. government agencies and their affiliated vendors and contractors.
When a product, system, or solution is referred to as "FIPS compliant," it means that it adheres to the guidelines and requirements outlined in the relevant FIPS 140 standard. This adherence ensures a baseline level of security for data protection, especially important when handling sensitive information.
There are multiple FIPS standards, however, CloudBees supports FIPS 140-3 for CloudBees CI on modern cloud platforms only. FIPS 140-3 primarily focuses on cryptographic modules (CM) that are algorithms that encrypt data stored within a system or device.
The FIPS 140-3 standard has four security levels, with level 1 providing the most basic level of security and level 4 providing the highest level of security. CloudBees CI on modern cloud platforms uses FIPS validated Bouncy Castle library for encryption and is therefore at Level 1. For more information on FIPS 140-3 security levels, refer to Security Requirements for Cryptographic Modules.
FIPS 140-3 Security Levels
Level 1 |
The lowest level of security. At least one approved algorithm or security function in the cryptographic module; no physical component required. A personal computer (PC) encryption board is an example of a Level 1 cryptographic module. |
Level 2 |
Level 1+ features that show evidence of tampering in attempt to gain physical access to crypto-keys (tampering proof sticker). |
Level 3 |
Level 2+ physical security mechanisms that respond to crypto module tampering or attempted access by destroying all keys. |
Level 4 |
Level 3+ physical security mechanisms provide a complete envelope of protection around cryptomodule with tampering resulting in destruction of keys. |
FIPS 140-3 compliant vs. validated
CloudBees CI on modern cloud platforms is FIPS 140-3 compliant not validated. It uses the FIPS approved Bouncy Castle library for encryption. FIPS 140-3 compliant means that CloudBees checked the components within CloudBees CI on modern cloud platforms and they adhere to the FIPS 140-3 standards and use a validated library. Any component within CloudBees CI on modern cloud platforms that cannot be brought into compliance either will not be available or will not function properly when the system is in FIPS mode. Unlike FIPS 140-3 compliance, FIPS 140-3 validation is a formal process where a third-party assessment of a system is performed at a National Institute of Standards and Technology (NIST) laboratory.
CloudBees CI on modern cloud platforms in FIPS mode
FIPS mode is enabled on a CloudBees CI on modern cloud platforms cluster during the installation process on AWS GovCloud using Elastic Kubernetes Servers (EKS). Once your cluster is in FIPS mode, it cannot revert back to non-FIPS mode.
| If you want a cluster in non-FIPS mode, you need to reinstall CloudBees CI on modern cloud platforms and recreate your jobs. Your configuration and job history may not be imported and backups from the cluster in FIPS mode may not work on your non-FIPS mode cluster. |
When CloudBees CI on modern cloud platforms is in FIPS mode, a "FIPS" label appears on the CloudBees CI on modern cloud platforms banner at the top of the page.
To enable FIPS mode on a CloudBees CI on modern cloud platforms cluster, refer to Install CloudBees CI on modern cloud platforms in FIPS mode.
FIPS-mode status page
The FIPS 140 status page is only accessible when your CloudBees CI on modern cloud platforms instance is in FIPS mode. This page provides information about the FIPS 140-3 compliance of your instance.
To access this page:
-
Select in the upper-right corner to navigate to the Manage Jenkins page.
-
Select FIPS 140 Status.
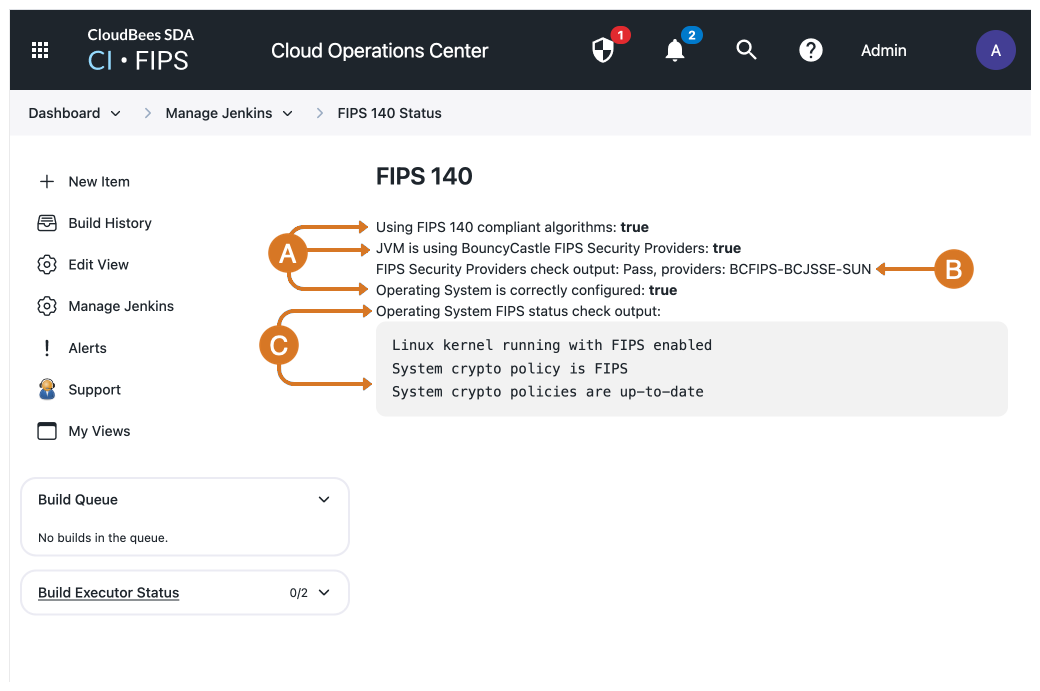 Figure 2. FIPS 140 Status page
Figure 2. FIPS 140 Status page
-
These settings are set to
truewhen the CloudBees CI on modern cloud platforms instance is in FIPS mode. -
The value in this setting explains why the Operating System is correctly configured setting (shown in step A) is set to
trueorfalse. -
Output that confirms your system is in FIPS mode.