Microsoft Entra ID (formerly Azure AD) is a cloud-based identity and access management service. It is designed to simplify and secure access to resources across your organization, whether on-premises or in the cloud. When integrated with CloudBees CI administrators can:
-
Control who can access CloudBees CI
-
Manage accounts in one central location
-
Grant users the ability automatically sign-in to CloudBees CI with their Microsoft Entra accounts.
To integrate CloudBees CI with Microsoft Entra ID:
-
Install the SAML plugin on your CloudBees CI instance.
-
Configure single sign-on (SSO) options in the operations center.
-
From the operations center dashboard, select in the upper-right corner to navigate to the Manage Jenkins page, and then select Security.
-
Navigate to Security Realm and select SAML 2.0.
-
Configure the following recommended settings as shown in the image below.
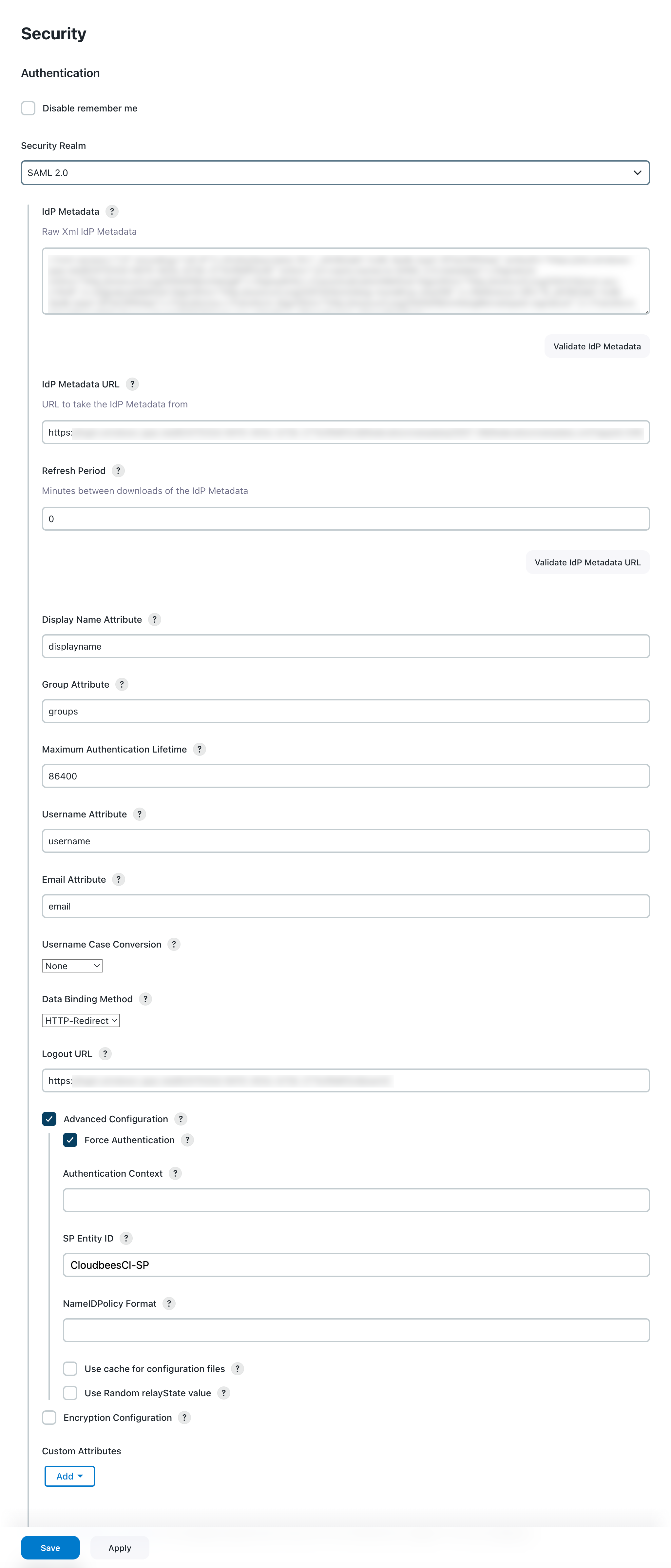 Figure 1. Configure SAML 2.0 details
Figure 1. Configure SAML 2.0 detailsLabel Definition IdP Metadata
The identity provider (IdP) Metadata in XML format. Download this metadata from Microsoft Entra ID and copy and paste into this field.
This setting is not needed if the IdP Metadata URL value is configured. IdP Metadata URL
The URL where the IdP metadata XML can be retrieved. This URL is provided by Microsoft Entra ID.
Refresh Period
The period of time (in minutes) to wait to refresh the IdP Metadata. Set the value to
0to not update the metadata.Display Name Attribute
Enter attribute name that contains the Display Name of the user set in the Microsoft Entra ID configuration.
Group Attribute
Enter the attribute name that contains the Groups of the user set in the Microsoft Entra ID configuration.
Username Attribute
Enter the attribute name that contains the User Name of the user set in the Microsoft Entra ID configuration.
Email Attribute
Enter the attribute name that contains the Email of the user set in the Microsoft Entra ID configuration.
Data Binding Method
Select one of the following redirection binding methods:
-
HTTP-Redirect - urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST
-
HTTP-POST - urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect
Check supported binding redirection types of your IdP. Logout URL
Enter the URL of your IdP where you want to be redirected once logged out.
Advanced Configuration
Select this option to enable additional options to force logins at your IdP, override default authentication mechanisms, or force multi-factor authentication. You can also set the sessions on Jenkins to be shorter than those on your IdP.
Force Authentication
Select this option to request the SAML IdP to force re-authentication of the user, instead of allowing an existing session with the IdP to be reused. This setting is left blank by default.
SP Entity ID
Enter the ID that identifies the specific Entra configuration. This field overrides the default Entity ID for this service provider. The service provider entity IDs are usually a URL, such as
http://jenkins.example.org/. -
-