| Configuration as Code for controllers is available for CloudBees CI 2.222.4.3 and later. |
Configuration as Code for controllers simplifies the management of a CloudBees CI cluster by capturing the configuration of CloudBees CI controllers in human-readable declarative configuration files which can then be applied to a controller in a reproducible way. By capturing the configuration in files, it can be treated as a first class revision-controlled artifact - versioned and then applied to controllers while being centrally managed from the CloudBees CI operations center, which can be used to store and distribute CasC bundles to the controllers in the cluster.
The following diagram illustrates the main elements and the architecture when an operations center is used to distribute CasC bundle and configure controllers:
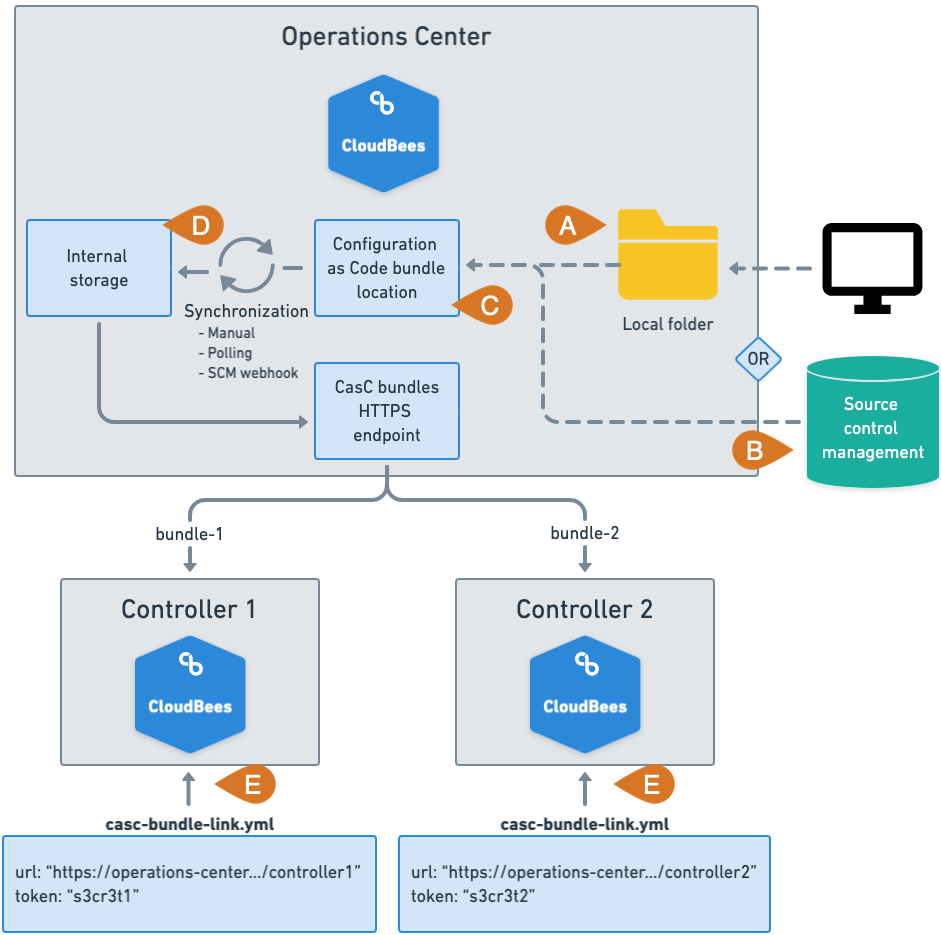
-
Bundles can be uploaded to a local folder within the operations center.
-
Bundles can be also retrieved from an SCM repository.
-
Users with the correct CasC permissions must configure the operations center adding the different bundles locations used as a source for the CasC bundles, local folders, or SCM repositories.
-
The operations center loads the bundles from the different bundle locations and stores them in the operations center local storage. The operations center periodically checks for new bundles or new bundle versions on the different bundle locations.
-
controllers must be configured using a
casc-bundle-link.yamlfiles that points to the HTTP endpoint in the operations center that provides the CasC bundles.